Professional Security Metaphor Diagram Template for PowerPoint & Google Slides
Description
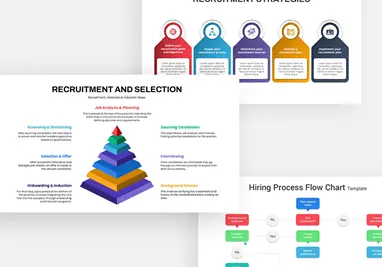
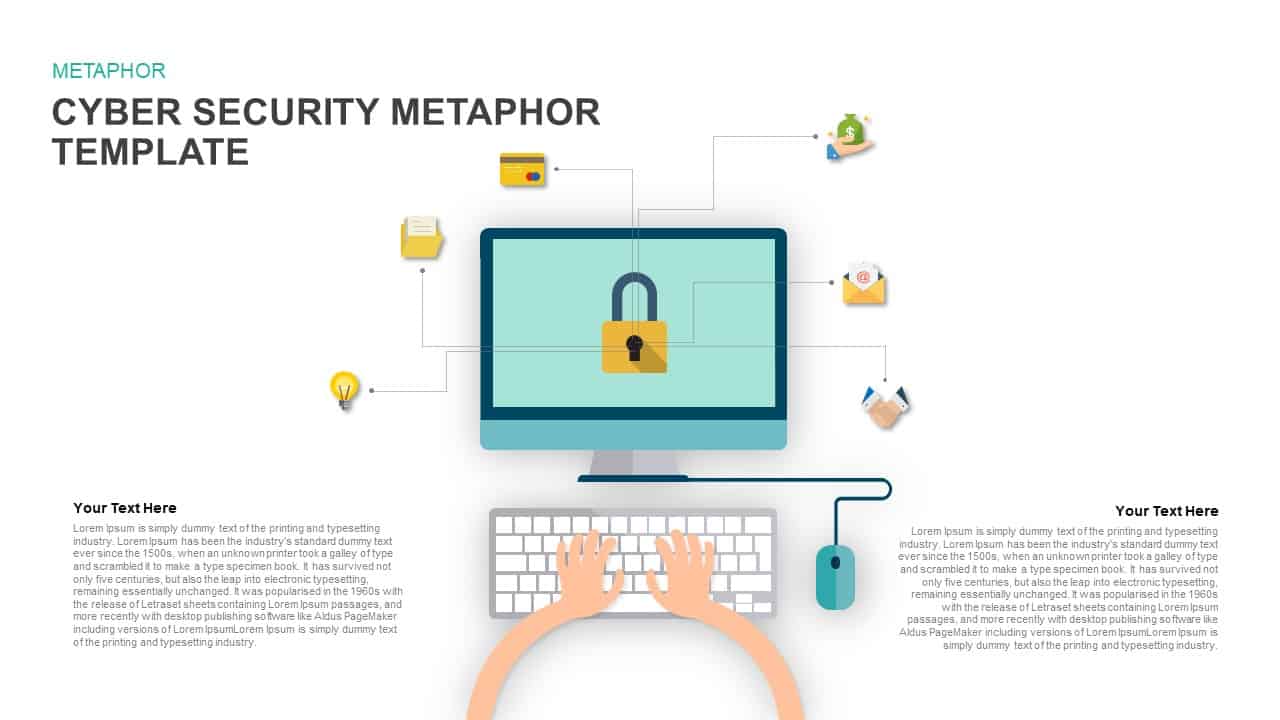
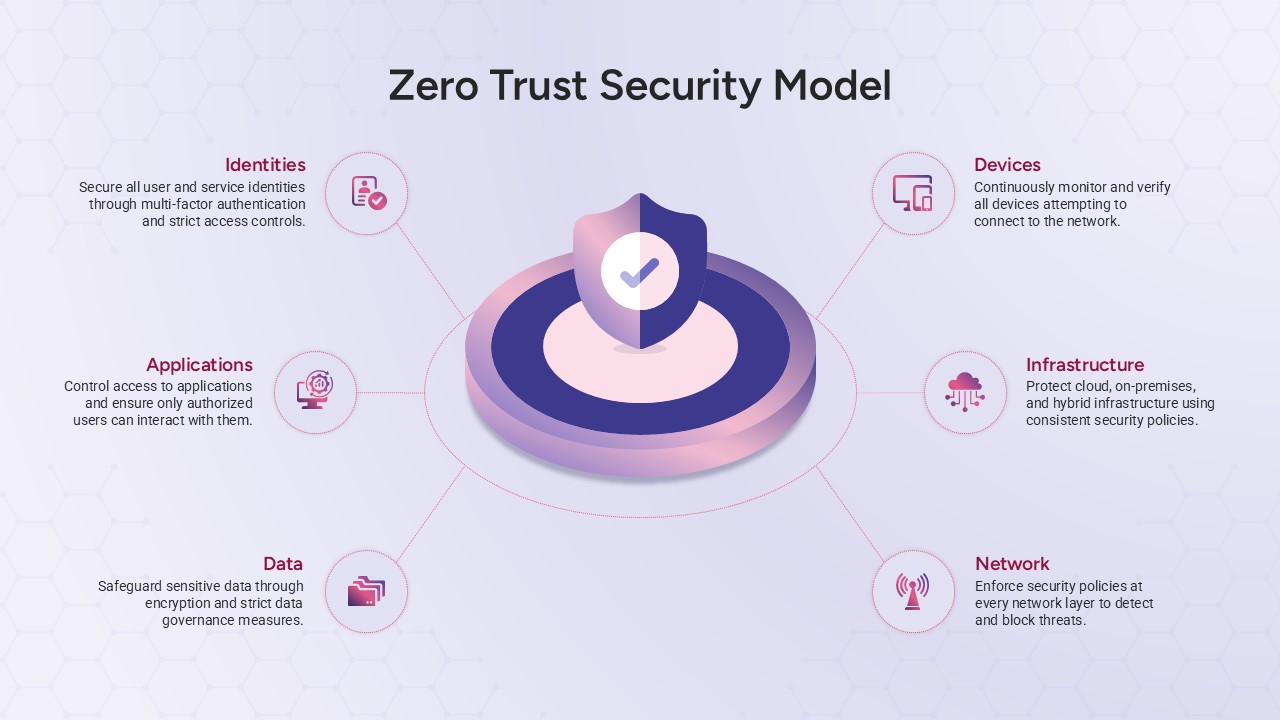
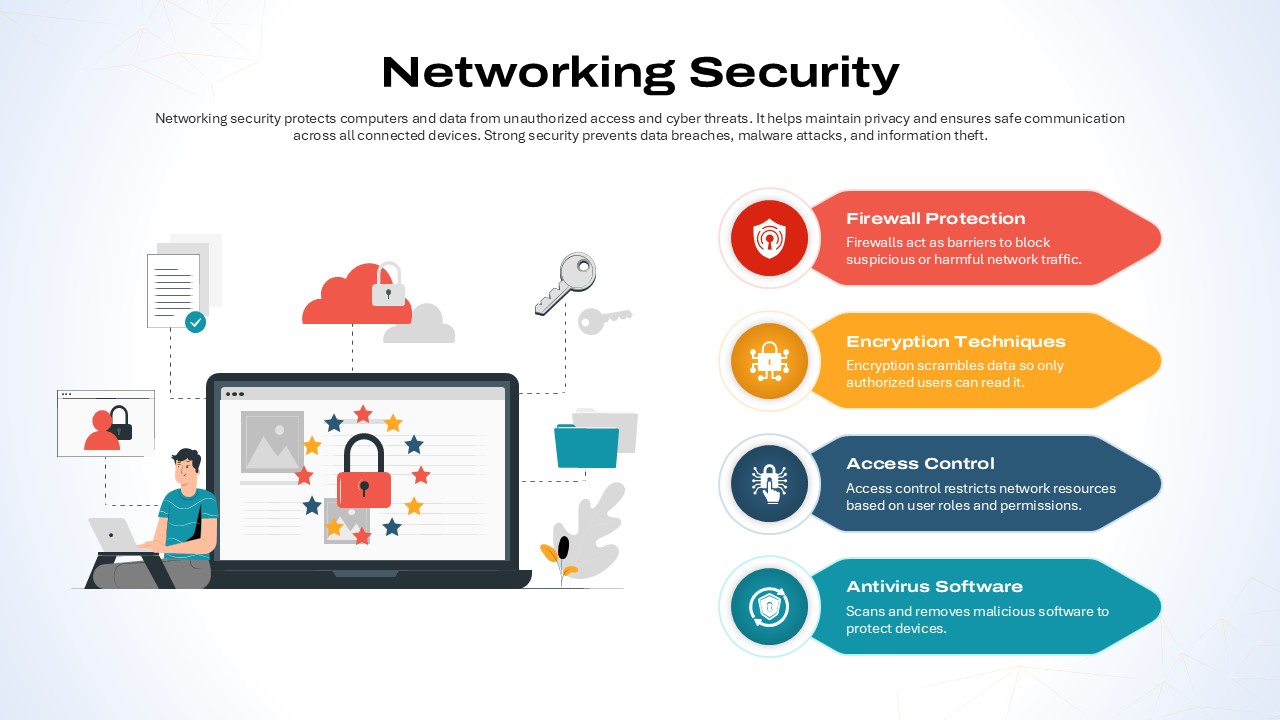
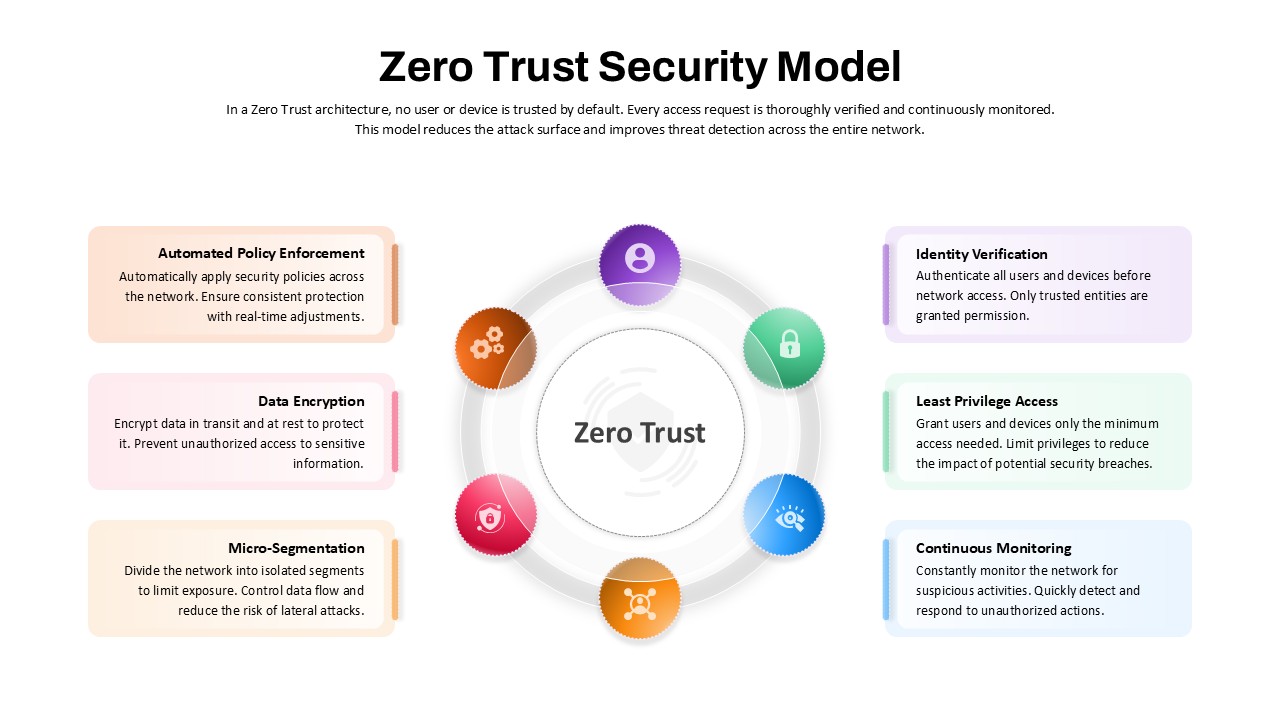
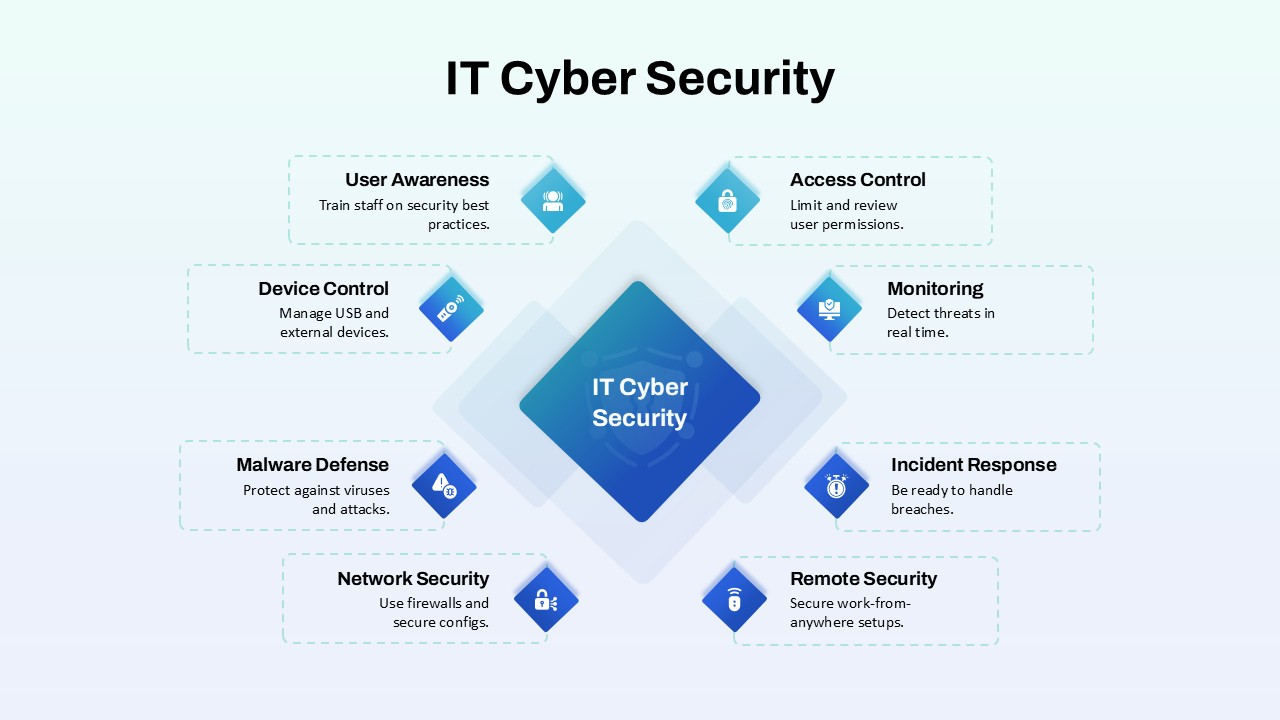
Leverage this Security Metaphor slide to depict digital protection frameworks and network safety with a modern, professional design. The slide showcases a bold shield with an embedded padlock icon against a rich blue gradient background, symbolizing robust data security. A clear header area accommodates your main title and subtitle, followed by a customizable text block for key messages or definitions. Vector-based graphics—including the shield, lock, and background elements—ensure crisp rendering and full scalability across devices, while the balanced layout and white space maintain optimal readability.
Built on master slides for both PowerPoint and Google Slides, this asset offers intuitive placeholders for titles, subtitles, and body text, enabling rapid content updates. Theme-linked color swatches allow you to adjust the primary hue and accent tones in seconds to match branding guidelines, while editable vector shapes let you recolor the shield outline and lock icon or swap in alternative symbols. Safe-zone guides, light and dark background variants, and optional fade-in animations enhance visual impact and presentation fluency. Preformatted text styles ensure consistent typography throughout your deck, and vector backgrounds preserve full-resolution fidelity on any screen size.
Completely scalable and distortion-free, the slide’s vector elements adapt seamlessly to 16:9 widescreen formats and accommodate optional grouping for quick repositioning. Drag-and-drop icon replacements, adjustable icon sizes, and flexible text box placement let you tailor layouts for boardroom presentations, client pitches, or training workshops. The slide’s minimalistic yet impactful design fosters stakeholder alignment by combining conceptual imagery with practical content areas, making it a versatile asset in any corporate, startup, or educational setting.
Whether you’re outlining IT compliance policies, presenting threat assessment findings, or educating teams on cybersecurity best practices, this slide streamlines communication with intuitive visual metaphors. Use the editable text area to highlight security protocols, performance metrics, or access control procedures, ensuring clarity and emphasis on critical safeguards.
Who is it for
IT managers, cybersecurity professionals, and risk officers will benefit from this diagram when presenting data protection strategies, security policies, or threat models. Consultants, trainers, and executive leaders can leverage its clear metaphor to align stakeholders and reinforce compliance initiatives.
Other Uses
Beyond security briefings, repurpose this slide for illustrating compliance workflows, access control hierarchies, incident response plans, or encryption overviews. Adapt the shield icon to represent privacy frameworks, network integrity checks, or user-authentication processes in any technology presentation.
Login to download this file