Zero Trust Security Model Overview template for PowerPoint & Google Slides
Description
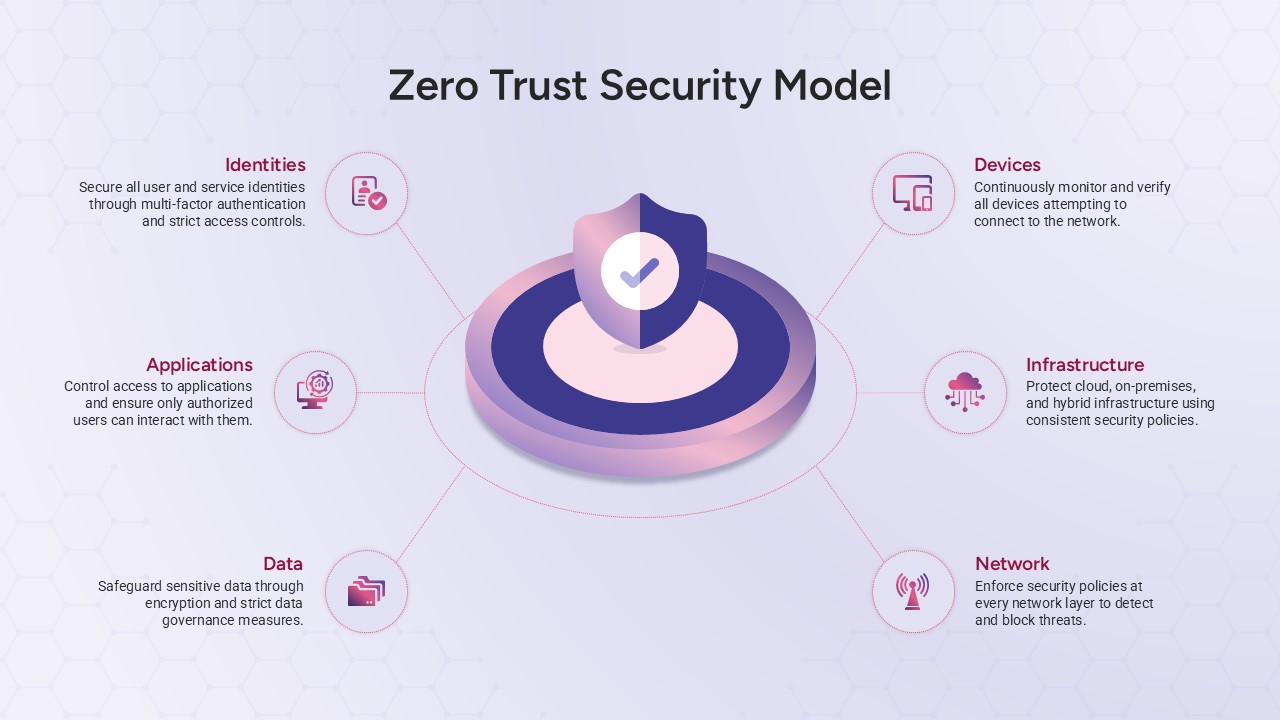
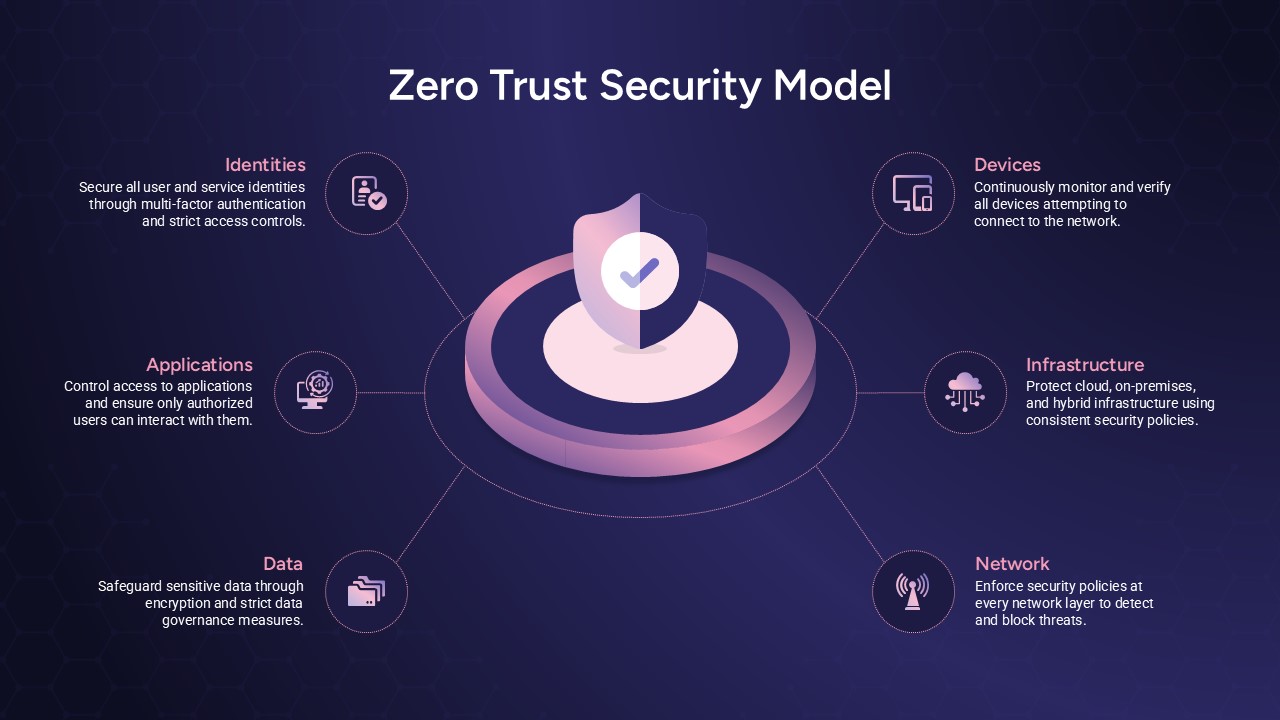
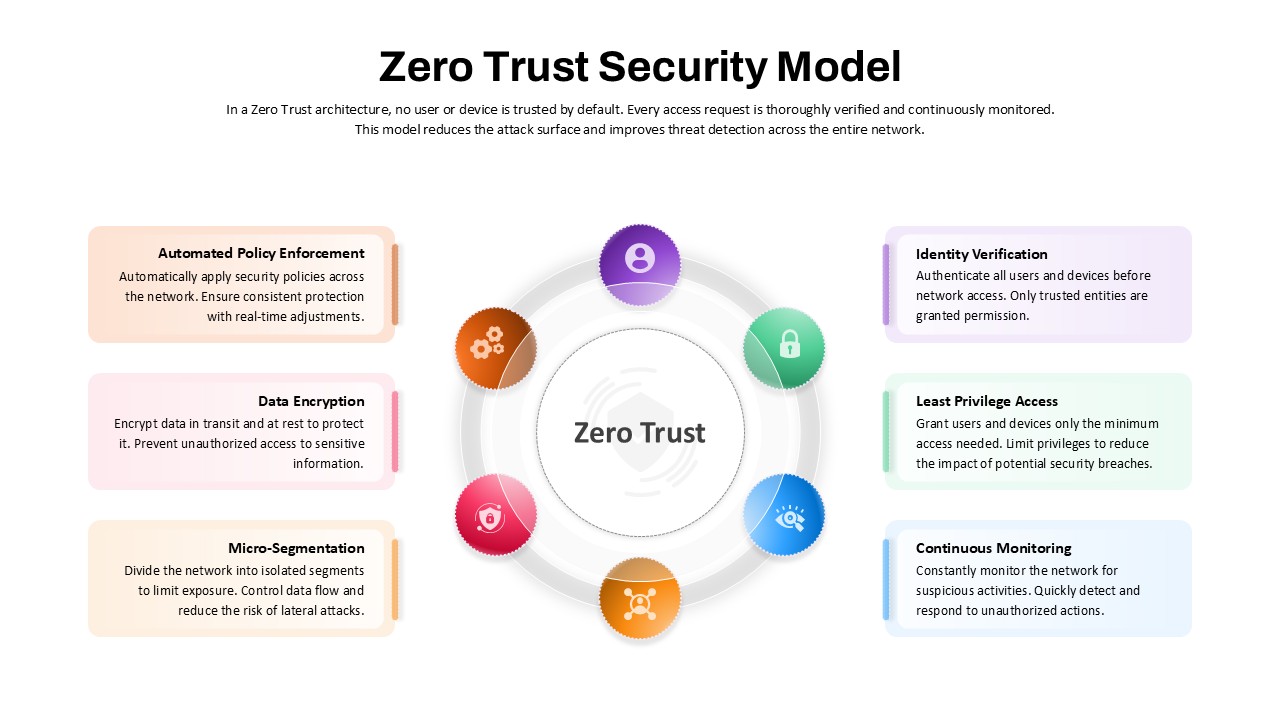
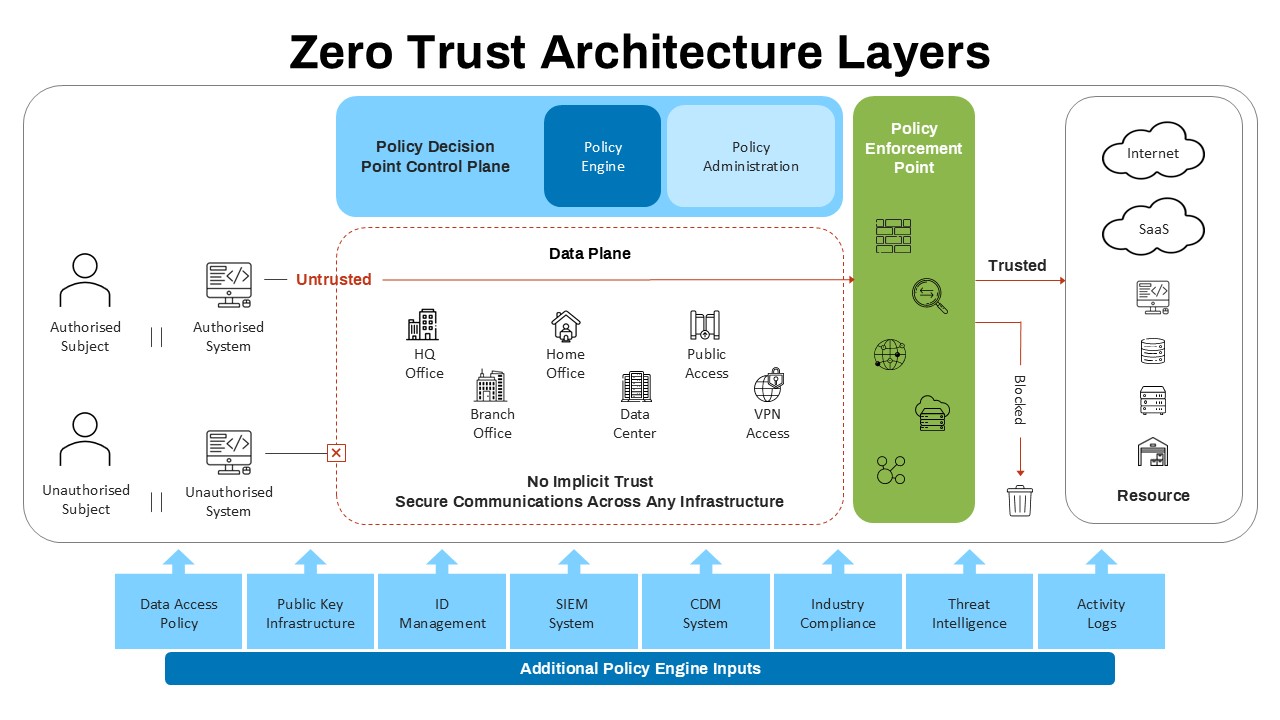
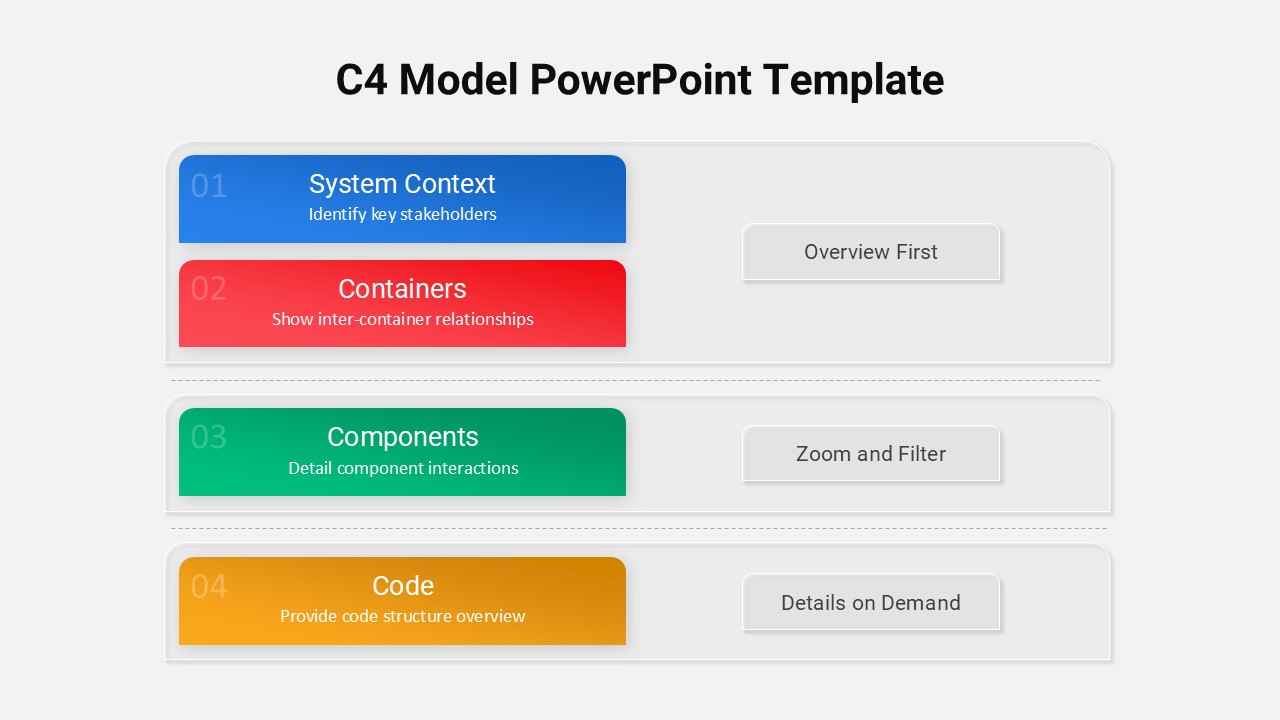
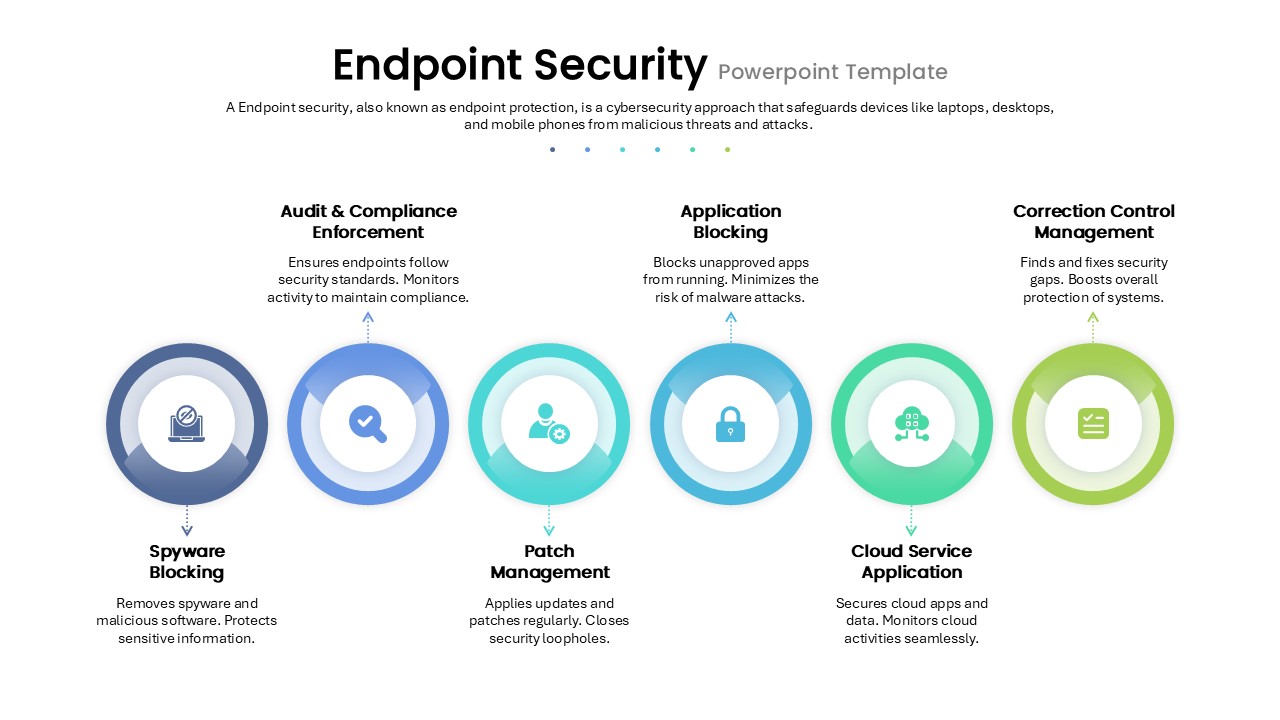
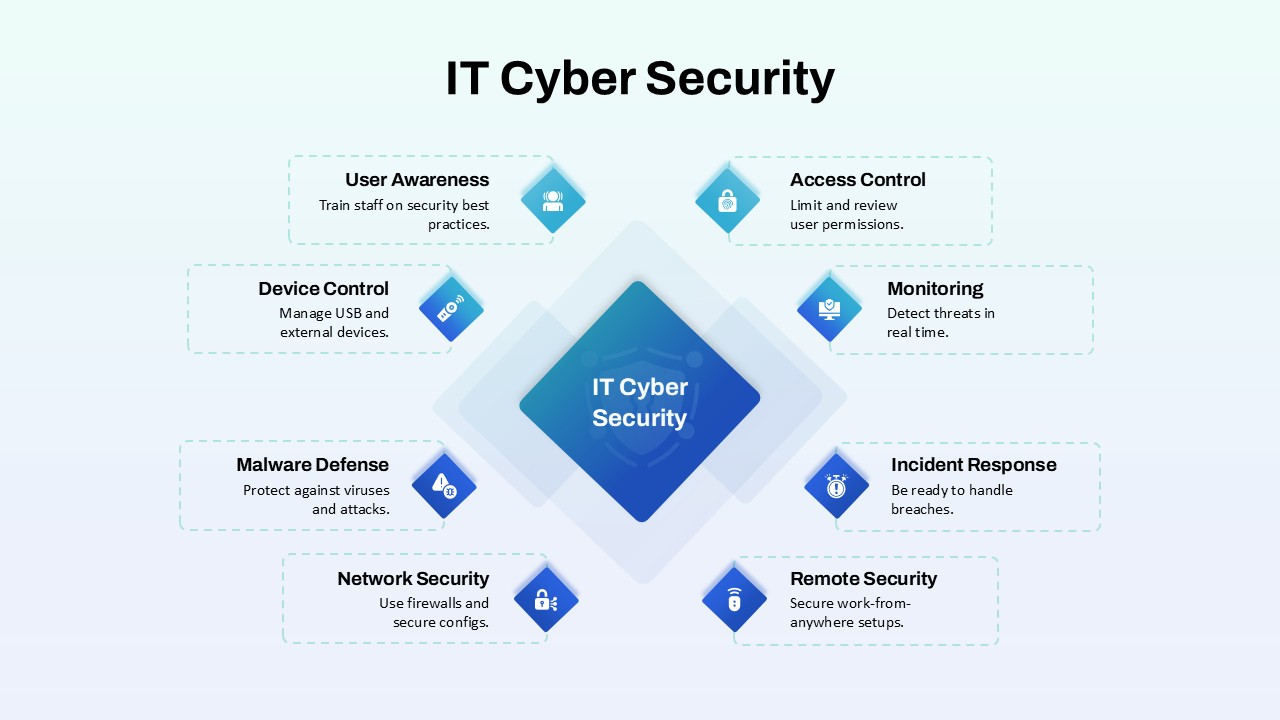
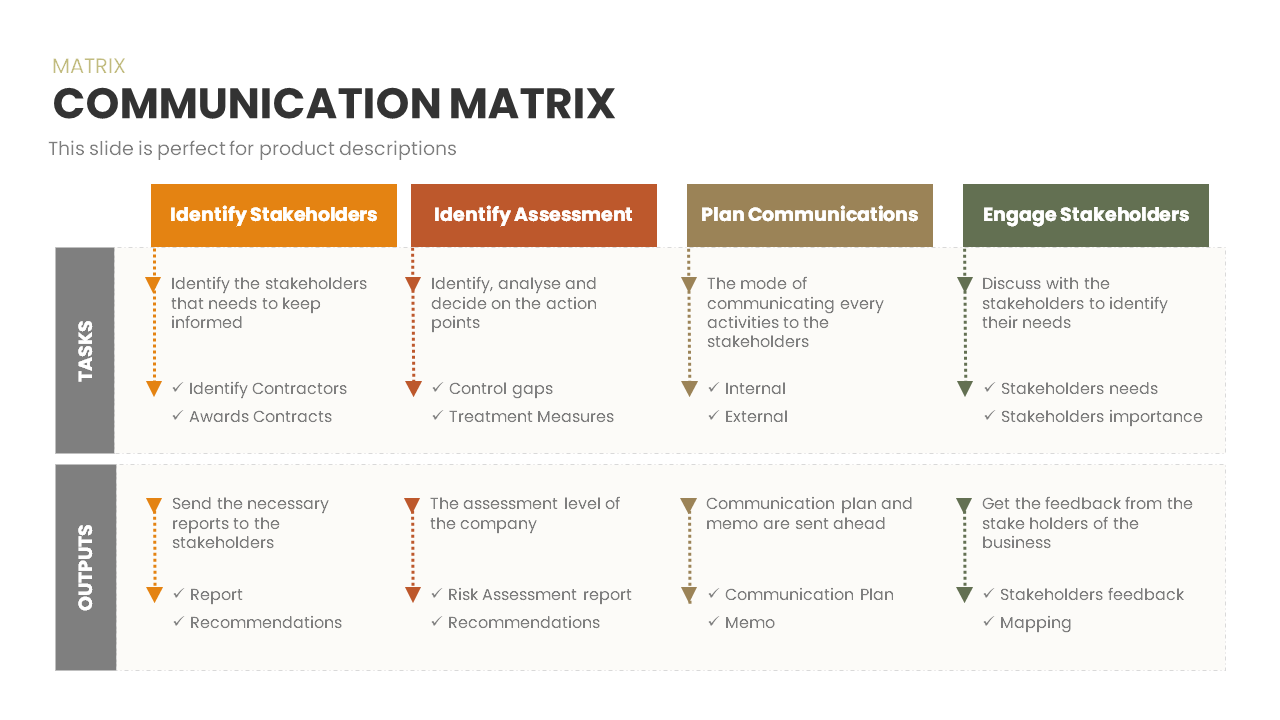
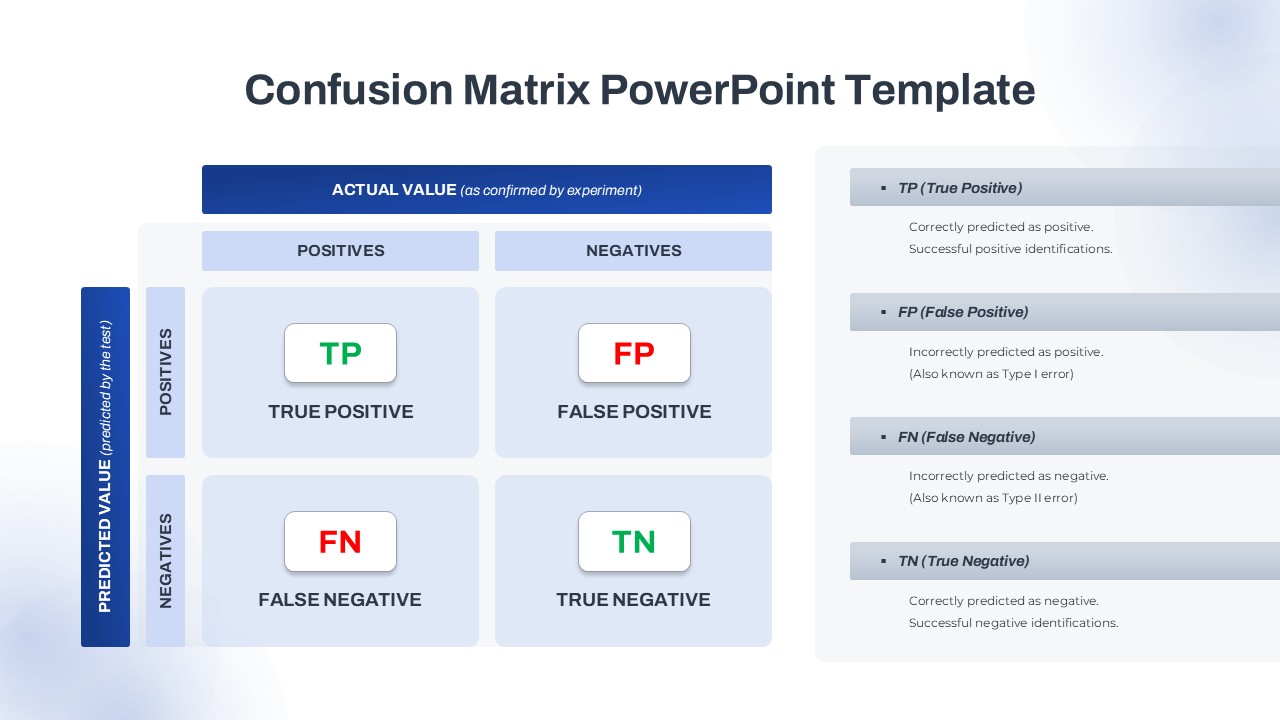
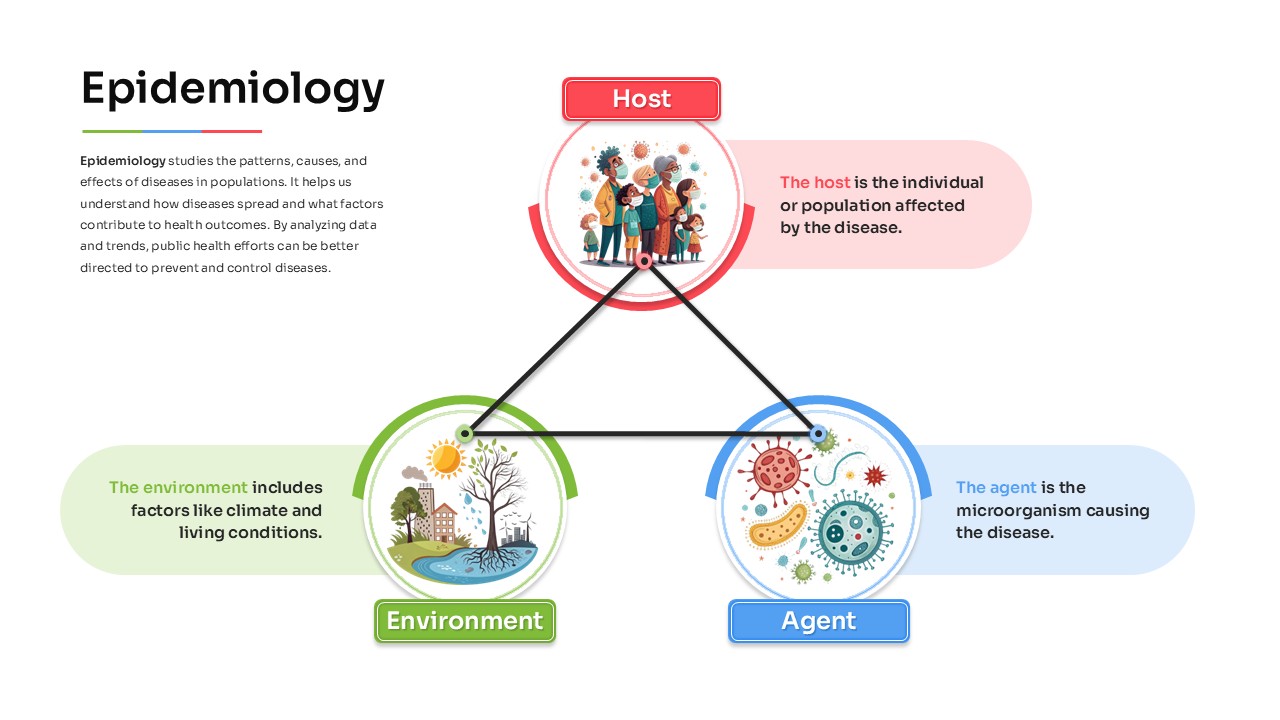
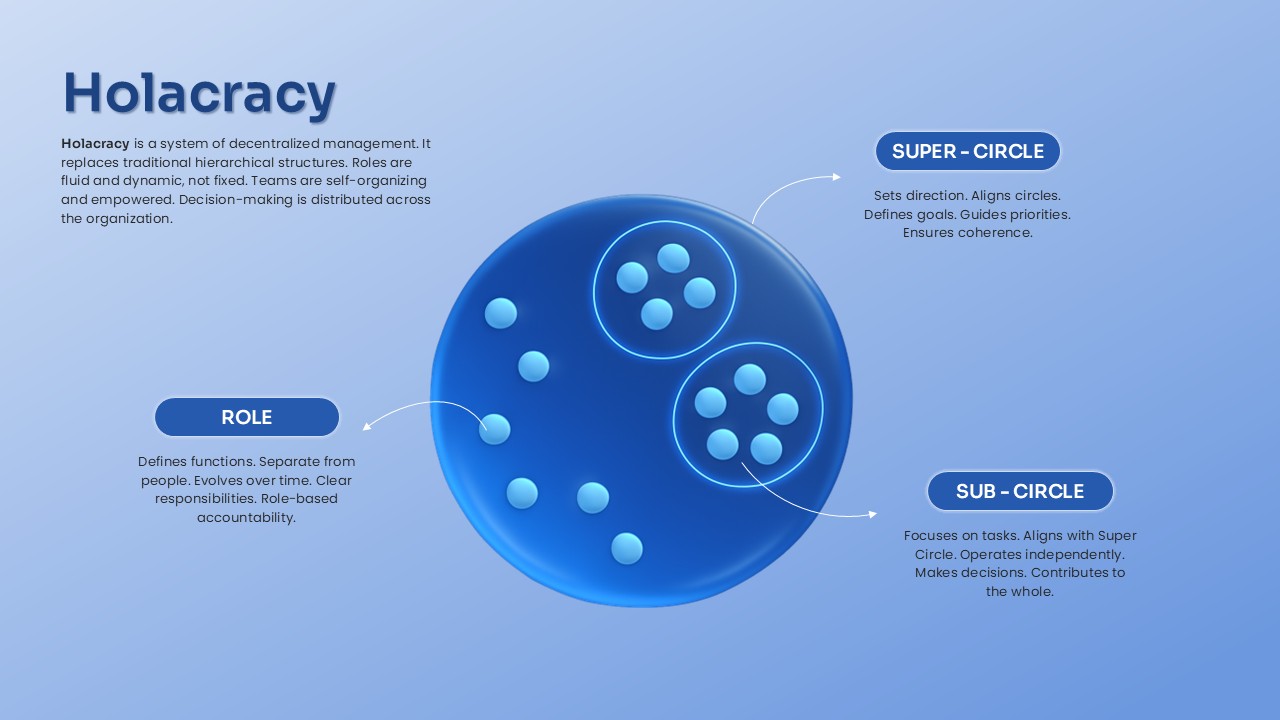
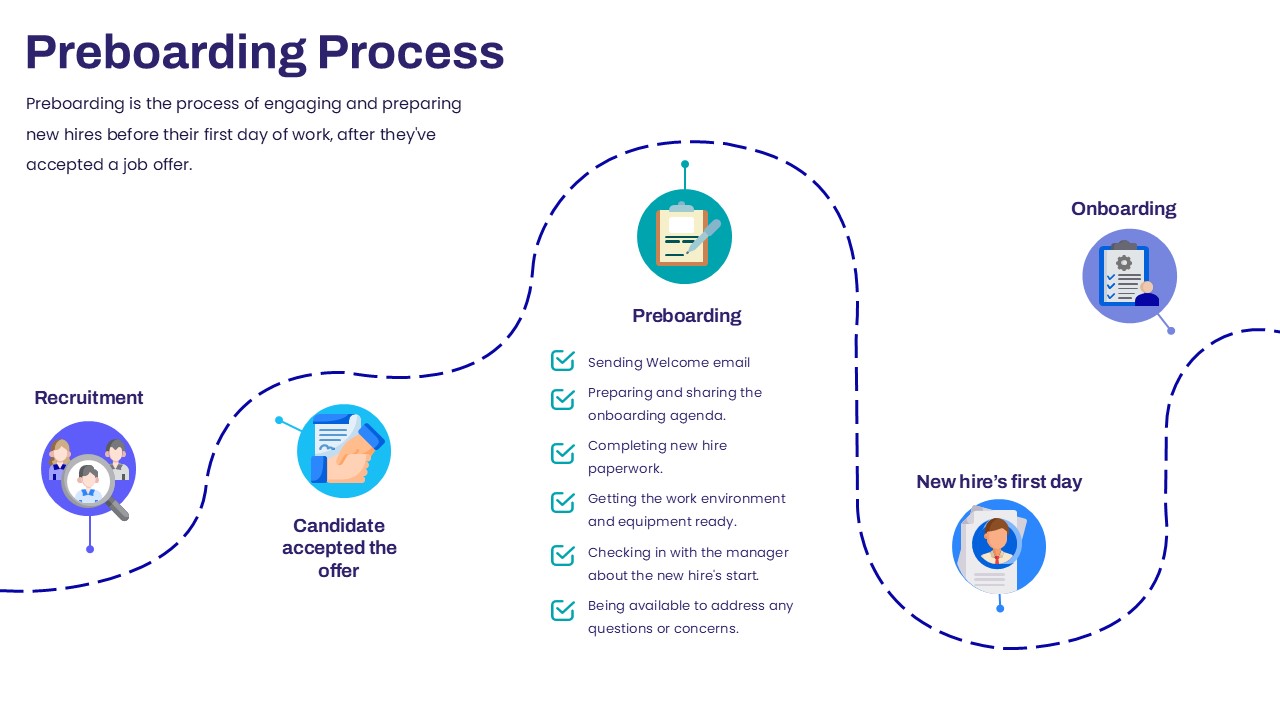
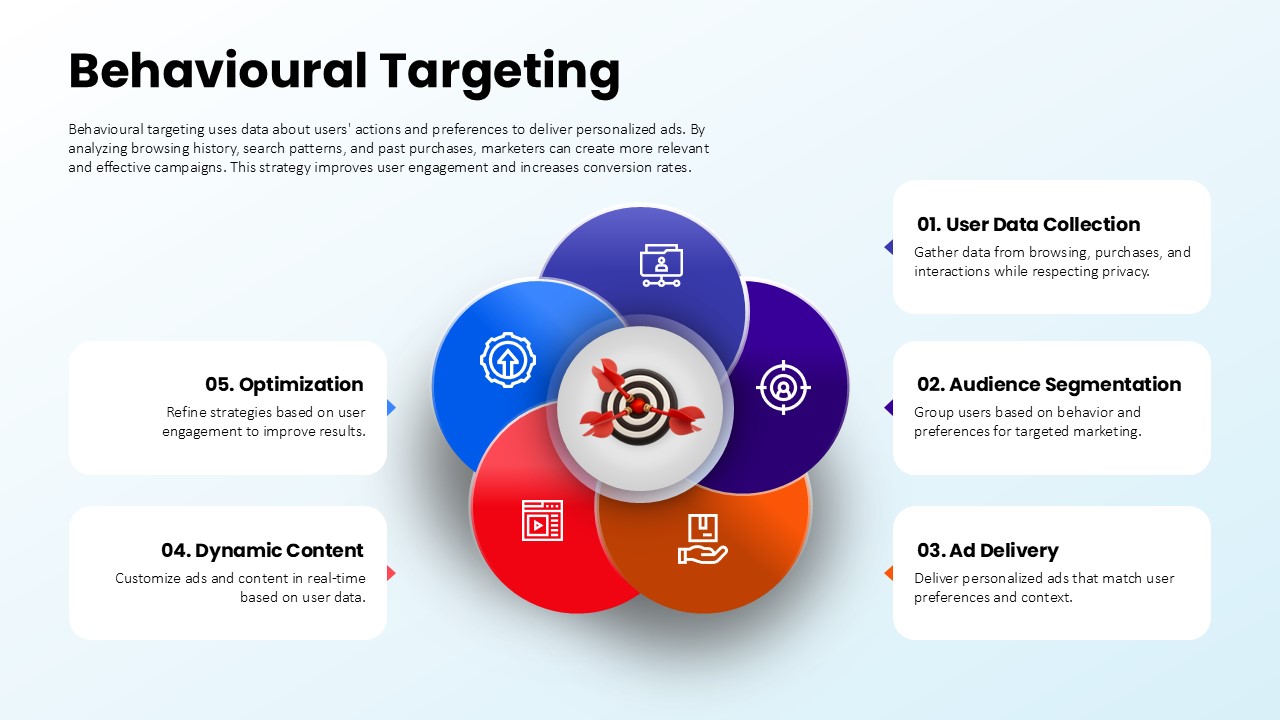
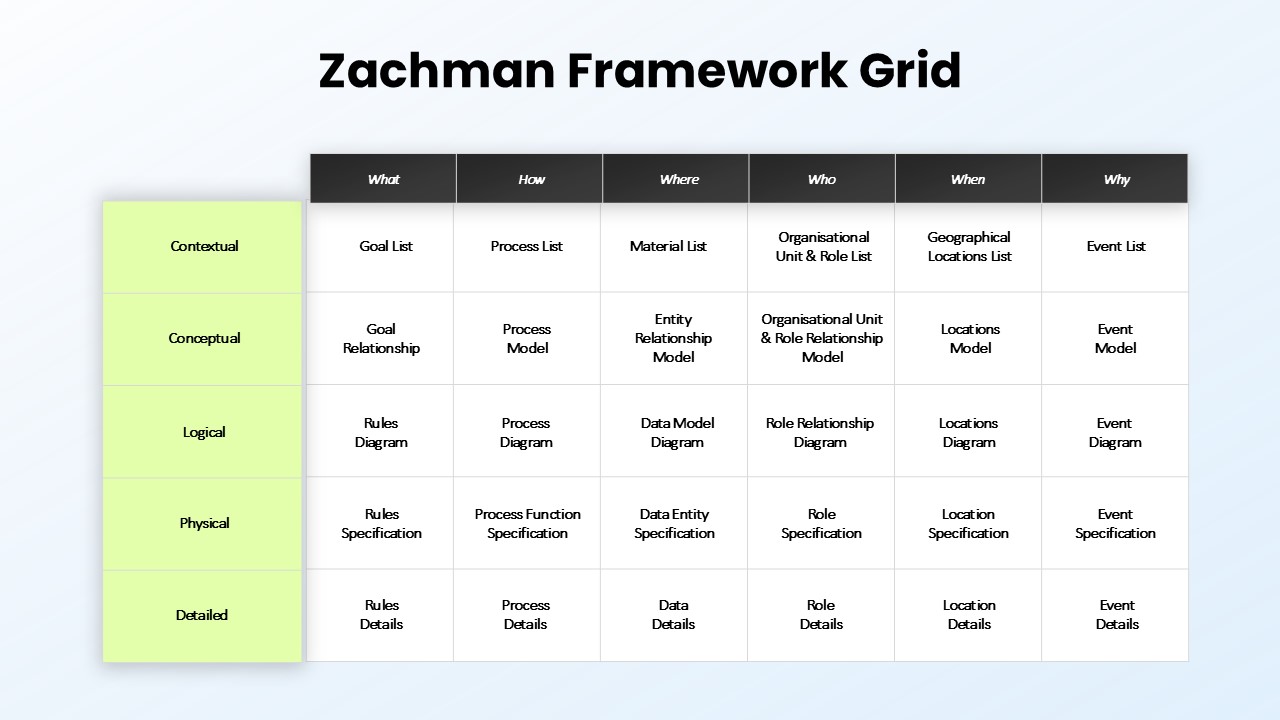
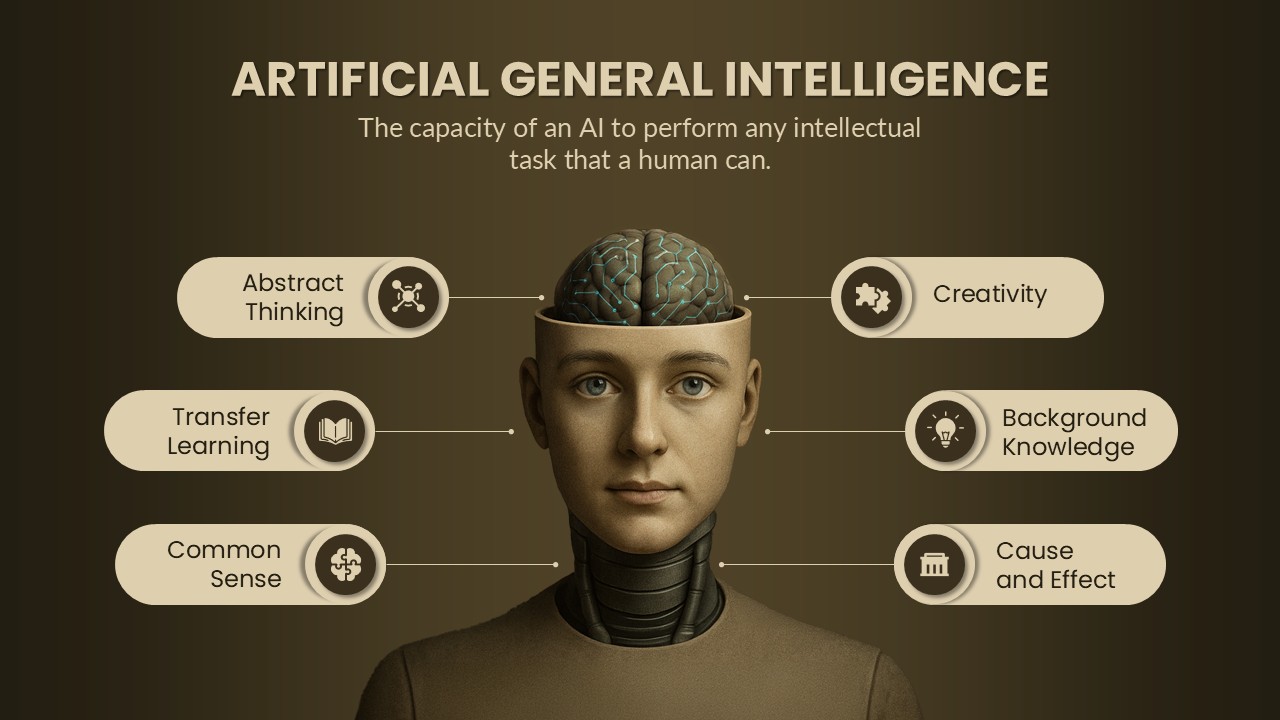
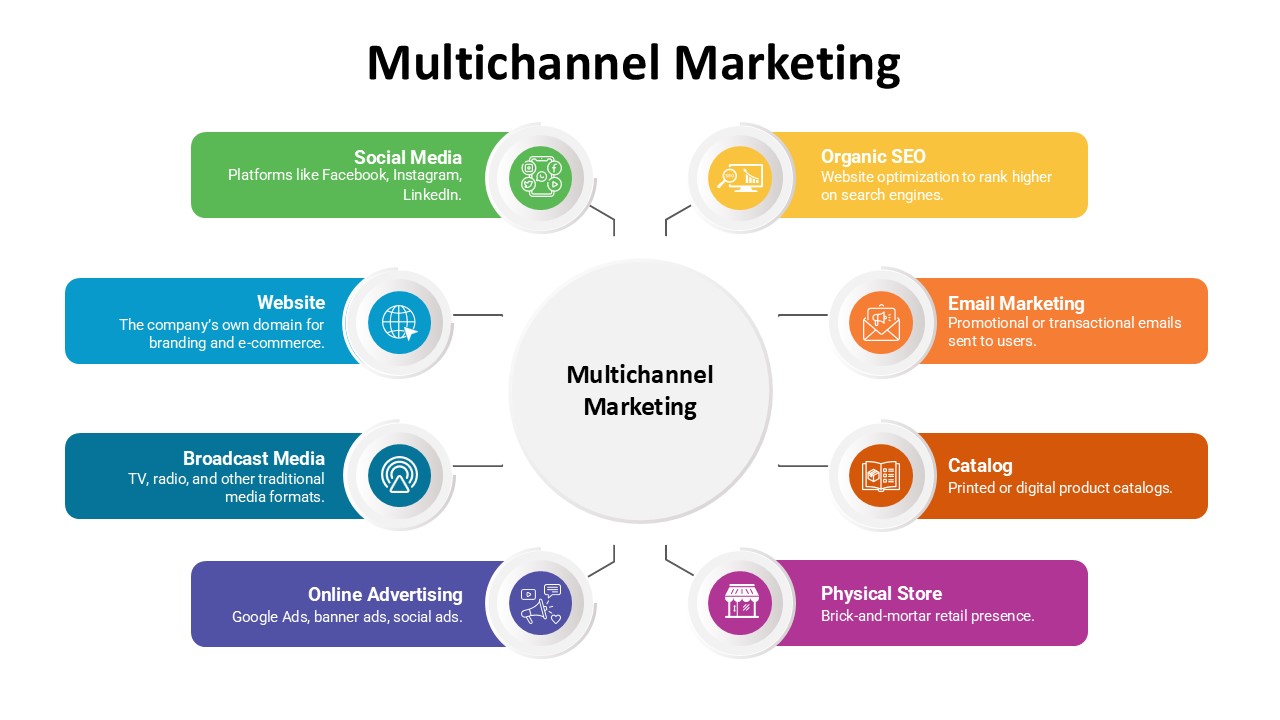
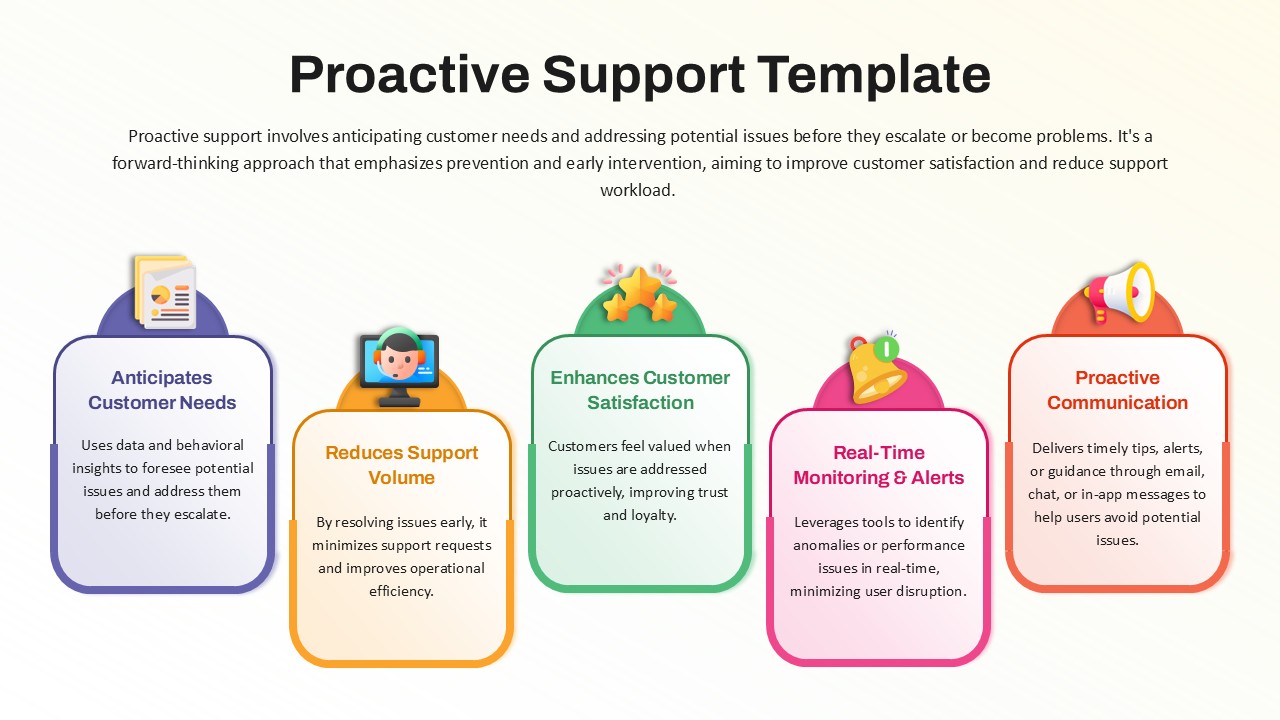
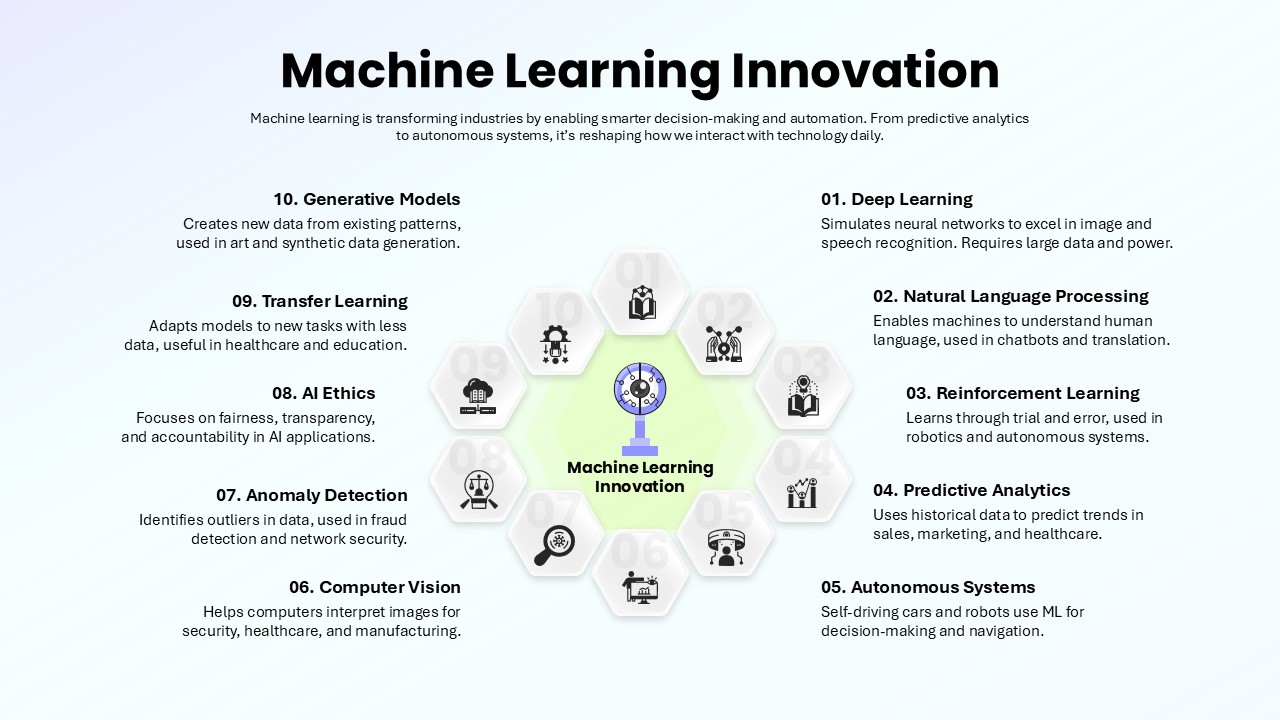
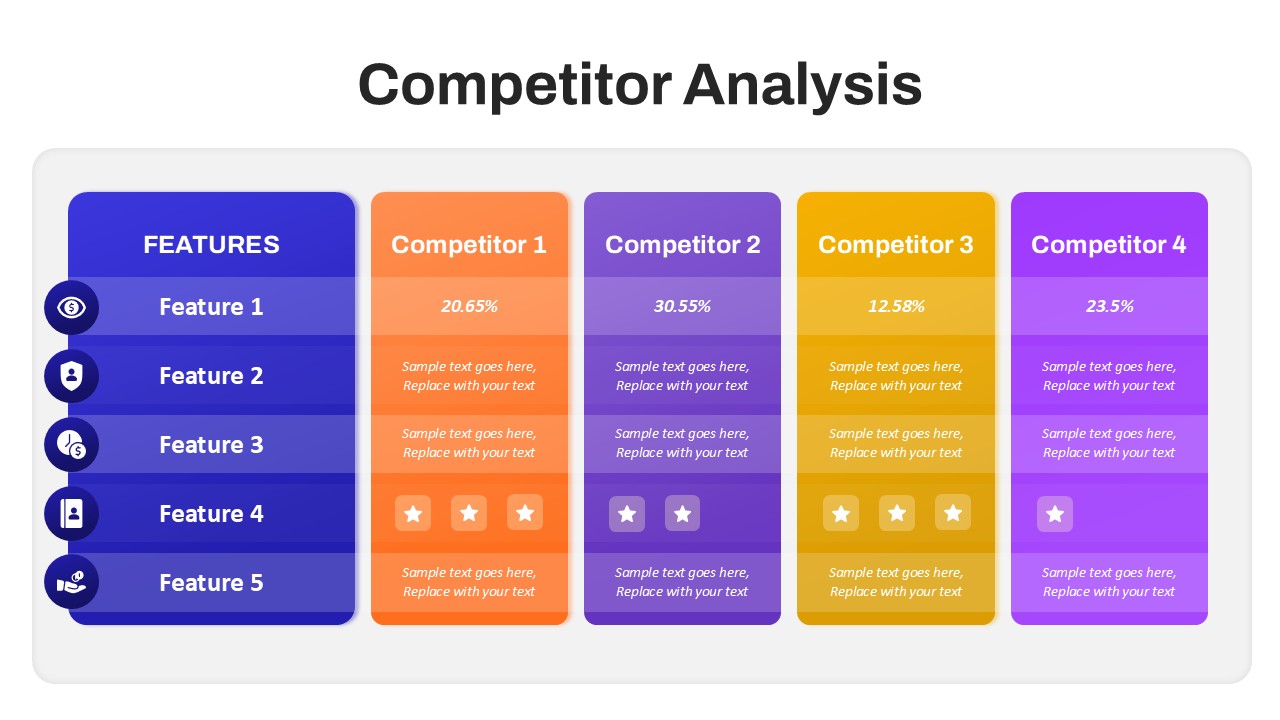
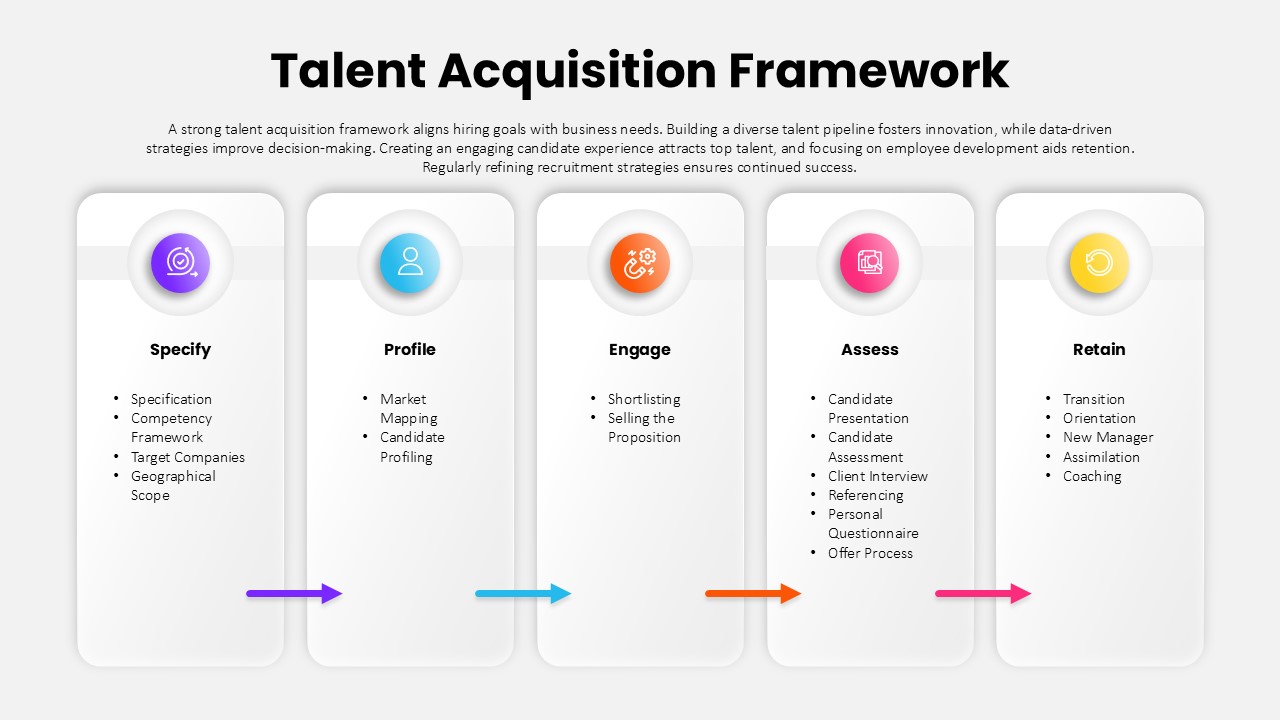
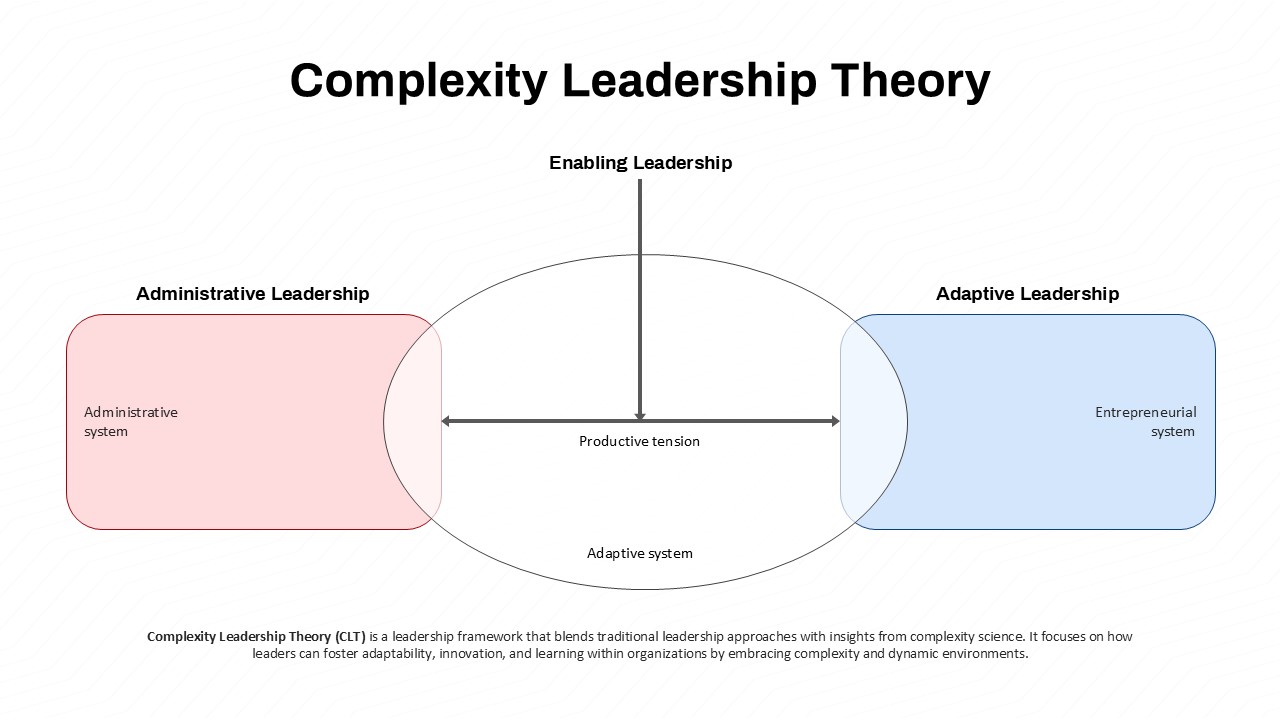
This slide provides a clear and visually appealing breakdown of the Zero Trust Security Model, illustrating the core components of a robust cybersecurity strategy. It highlights five key areas: Identities, Applications, Devices, Infrastructure, and Network, each associated with an icon and brief, actionable text explaining its role in safeguarding systems. The central shield symbolizes the core principle of Zero Trust, which asserts that trust is never assumed, even inside the network. This modern design uses a clean, geometric background with a purple and pink color palette, enhancing the slide’s clarity and engagement.
The slide is designed for easy customization, allowing you to adjust text and visuals to align with your company’s branding or specific cybersecurity policies. The sleek, minimalistic aesthetic makes it suitable for corporate presentations, security training sessions, or IT strategy meetings. Whether you’re outlining security protocols to executives, educating teams on cybersecurity, or presenting to clients, this slide offers a concise and effective way to communicate the principles of Zero Trust.
Who is it for
This template is ideal for cybersecurity professionals, IT managers, network security experts, and executives responsible for data protection. It is perfect for tech-oriented teams, security consultants, and organizations looking to present their Zero Trust implementation strategies to stakeholders or clients.
Other Uses
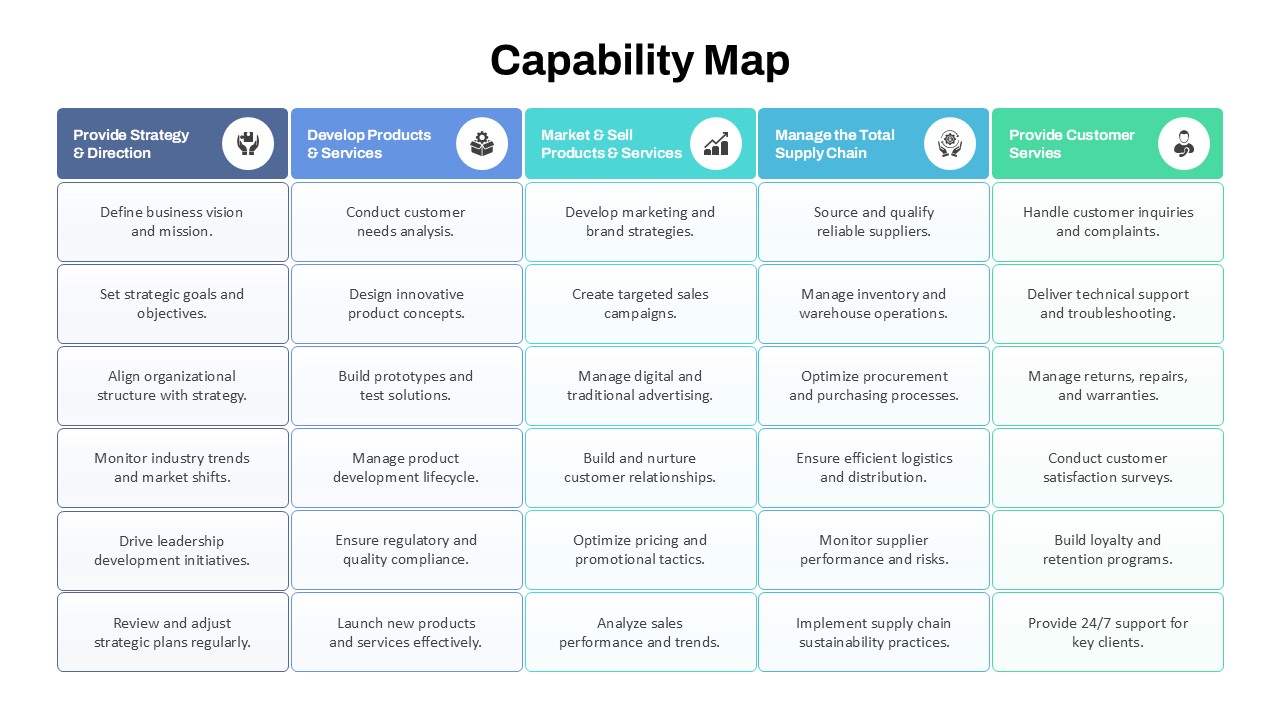
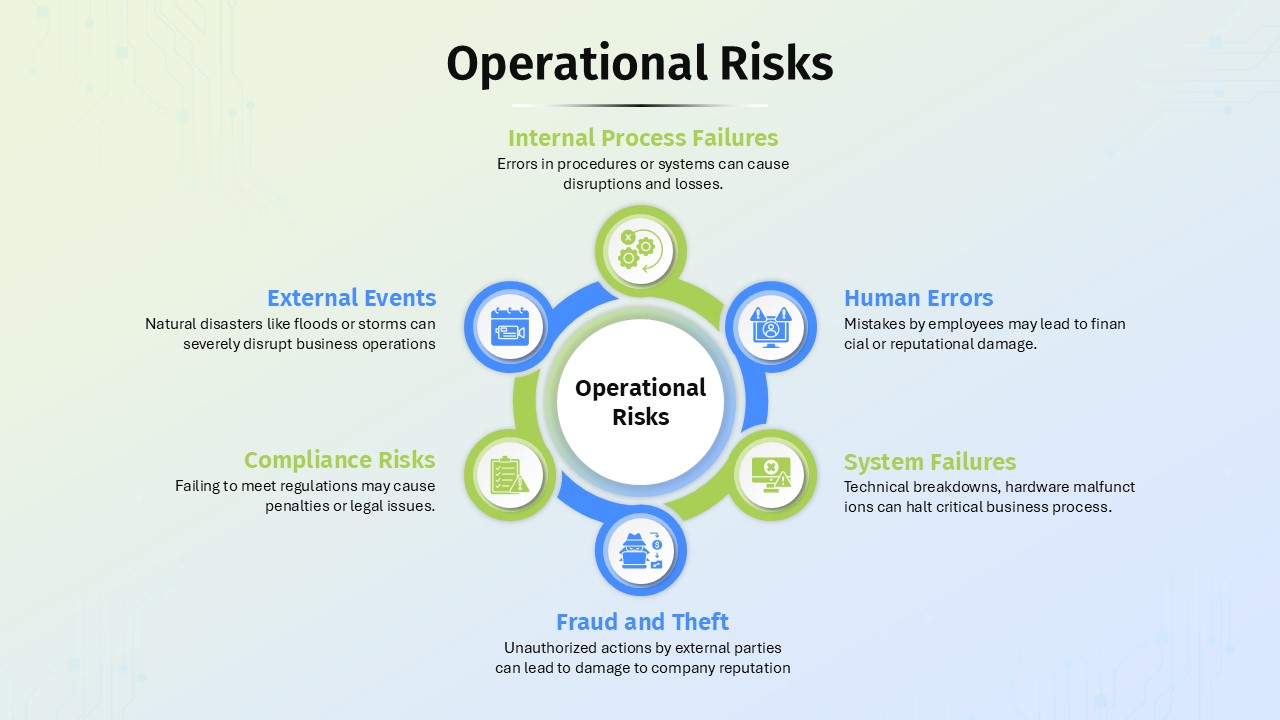
Besides cybersecurity, this slide can be repurposed for explaining other complex security frameworks or any process model involving layered protection or access control. Use it in educational contexts to teach about digital security, encryption, and privacy. It can also serve in organizational risk management reviews or any business context requiring a focus on secure systems and protocols.
Login to download this file