Cyber Security Metaphor Diagram Template for PowerPoint & Google Slides
Description
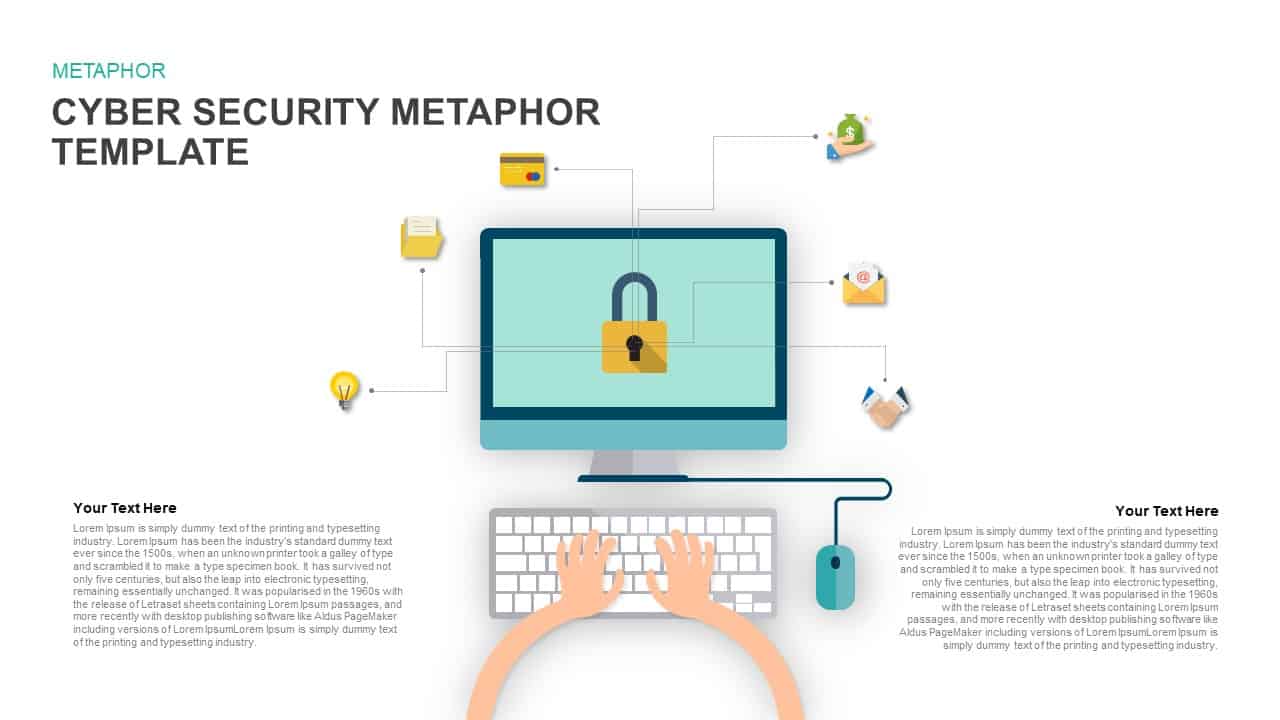
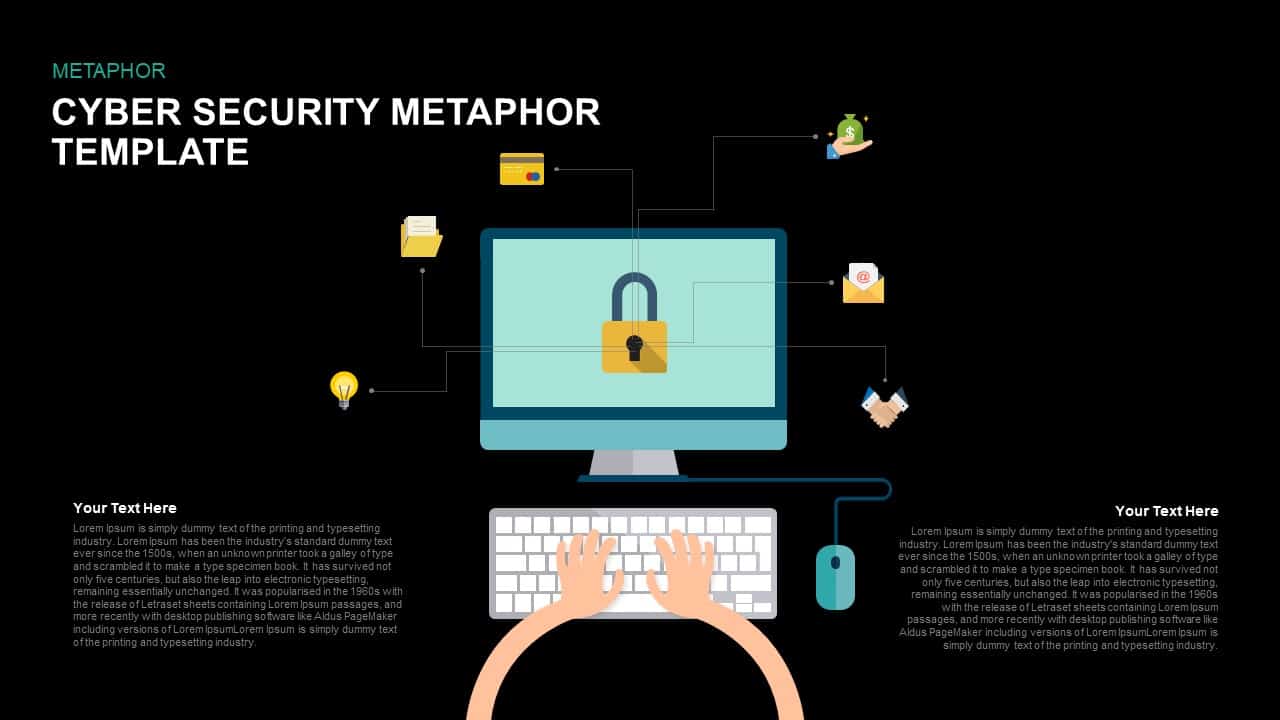
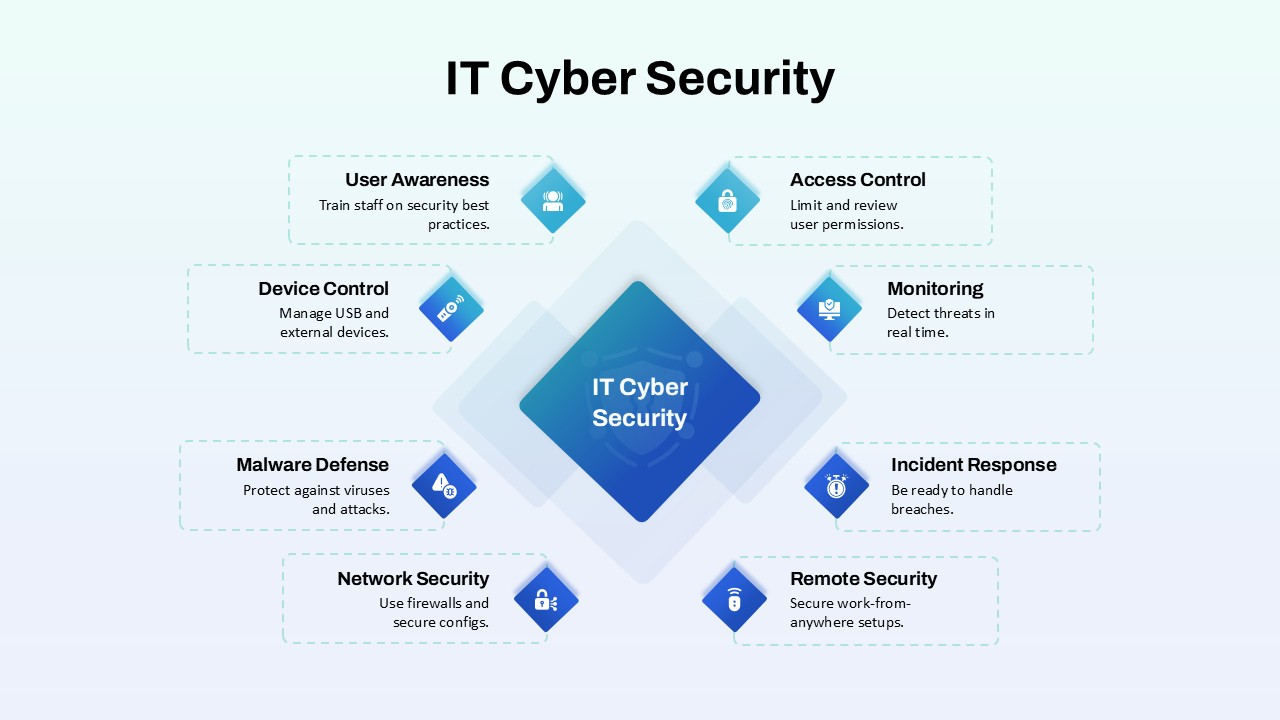
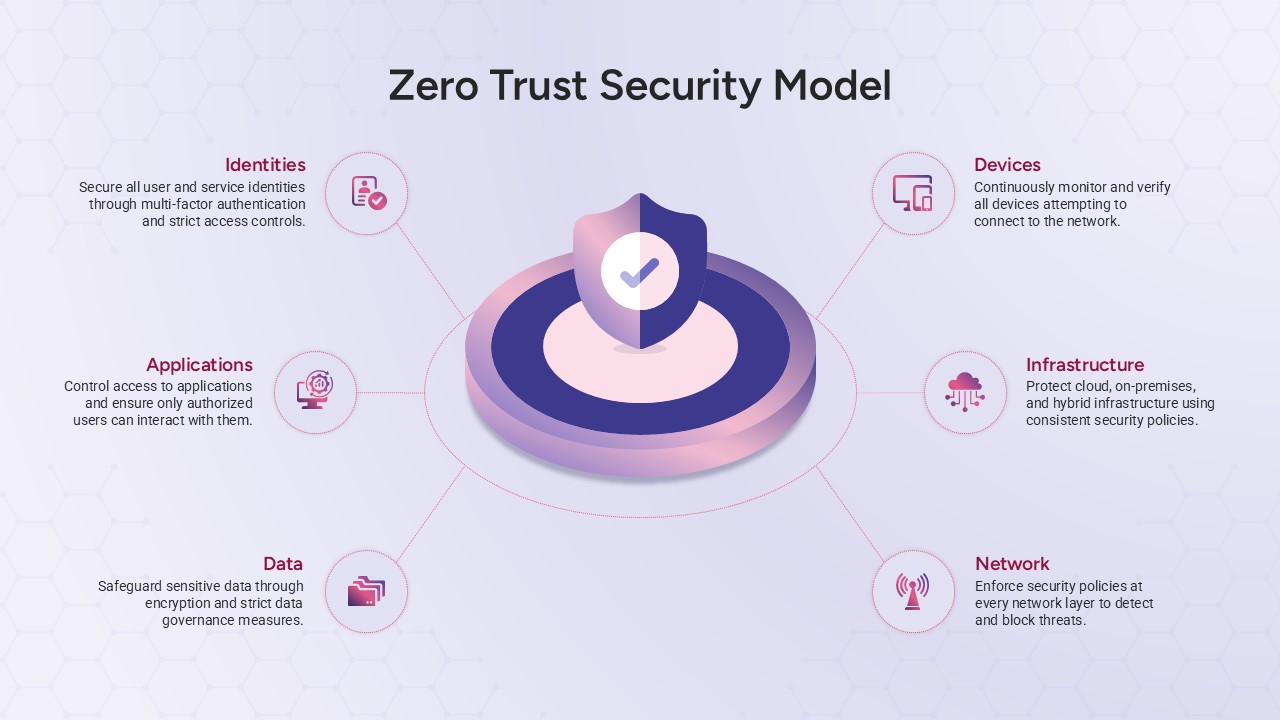
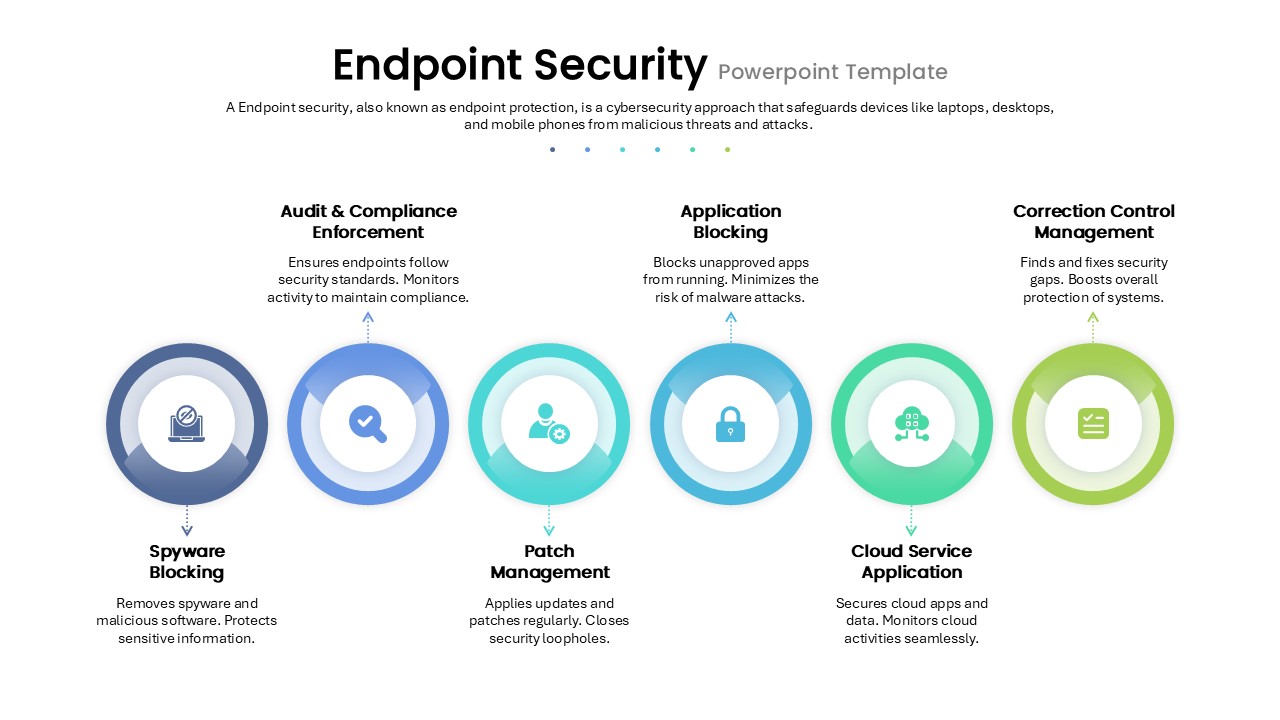
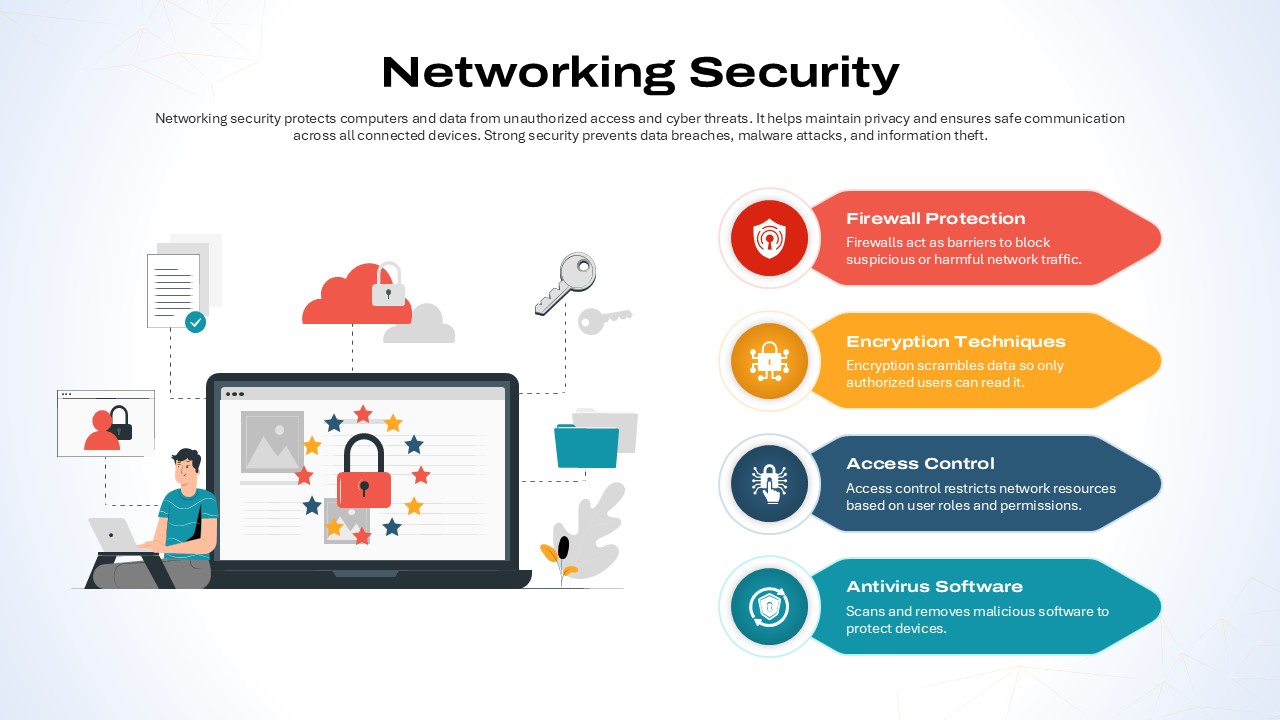
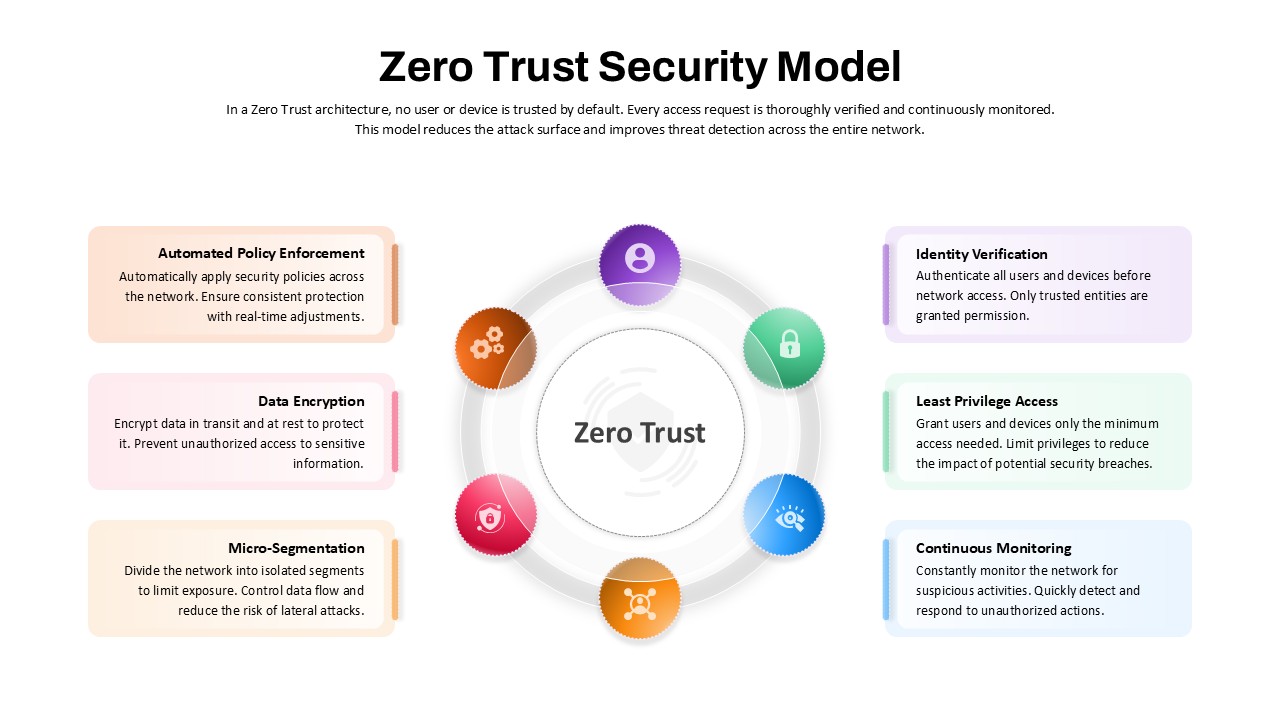
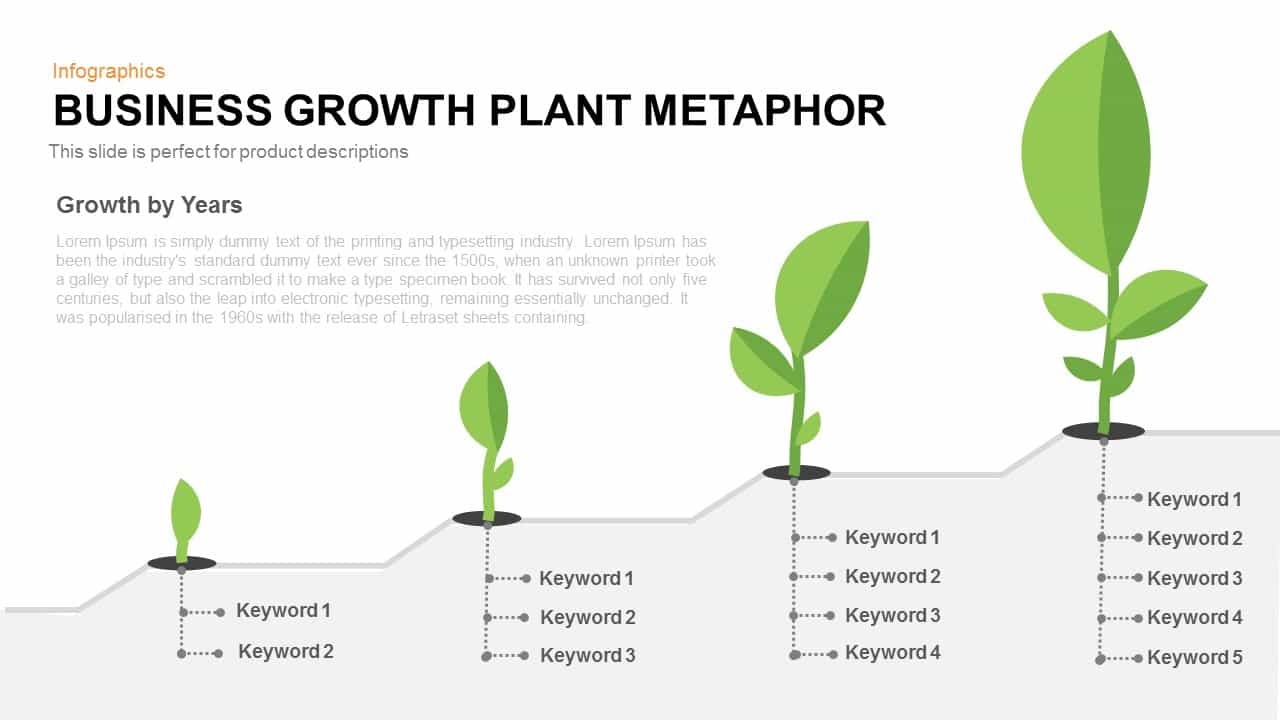
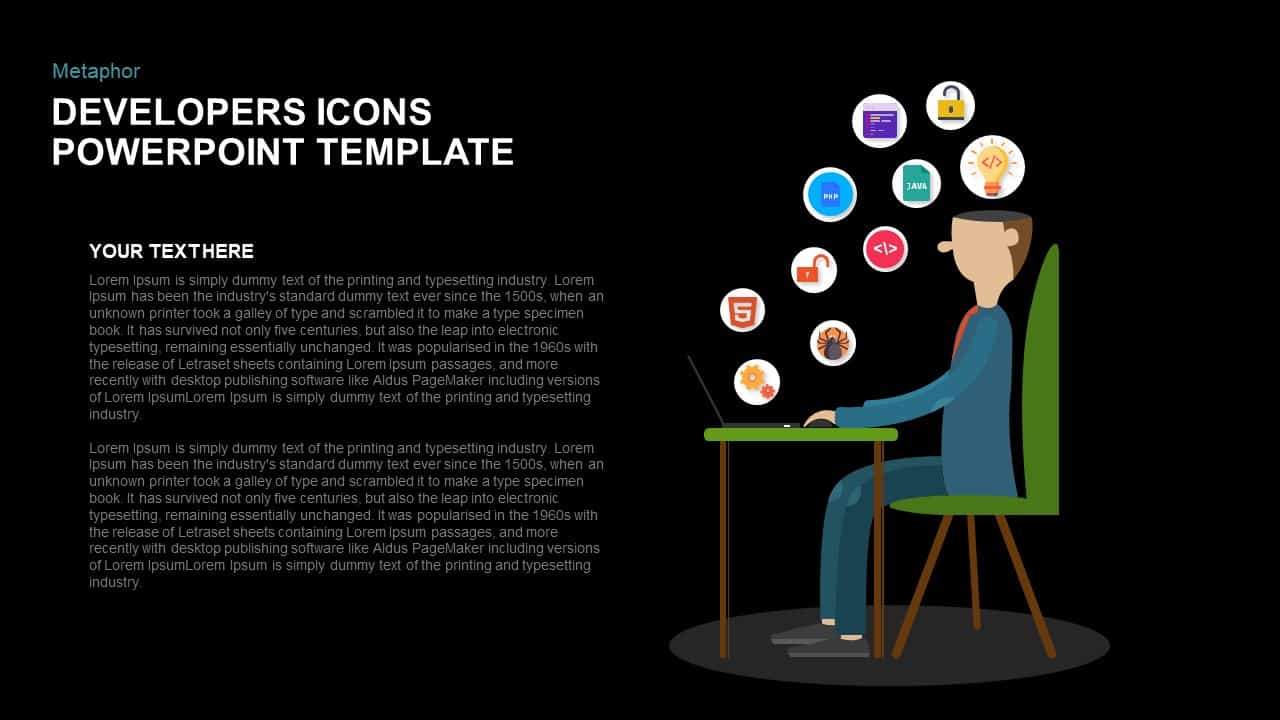
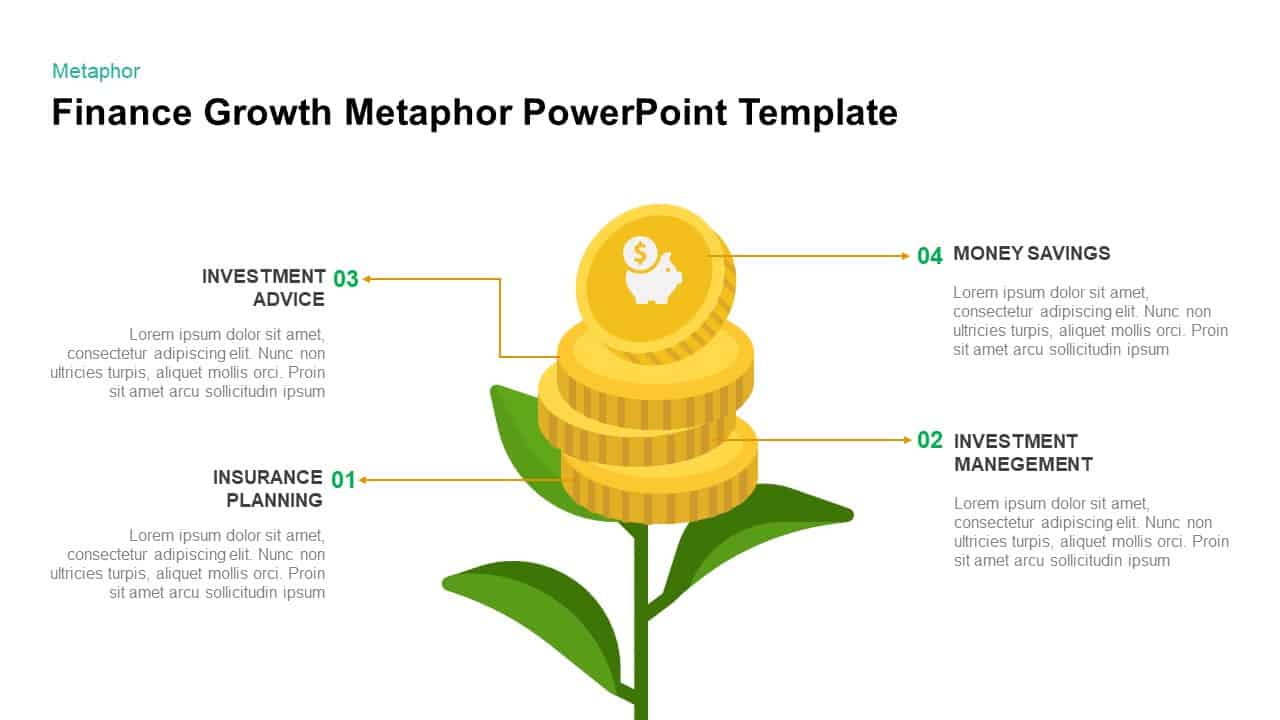
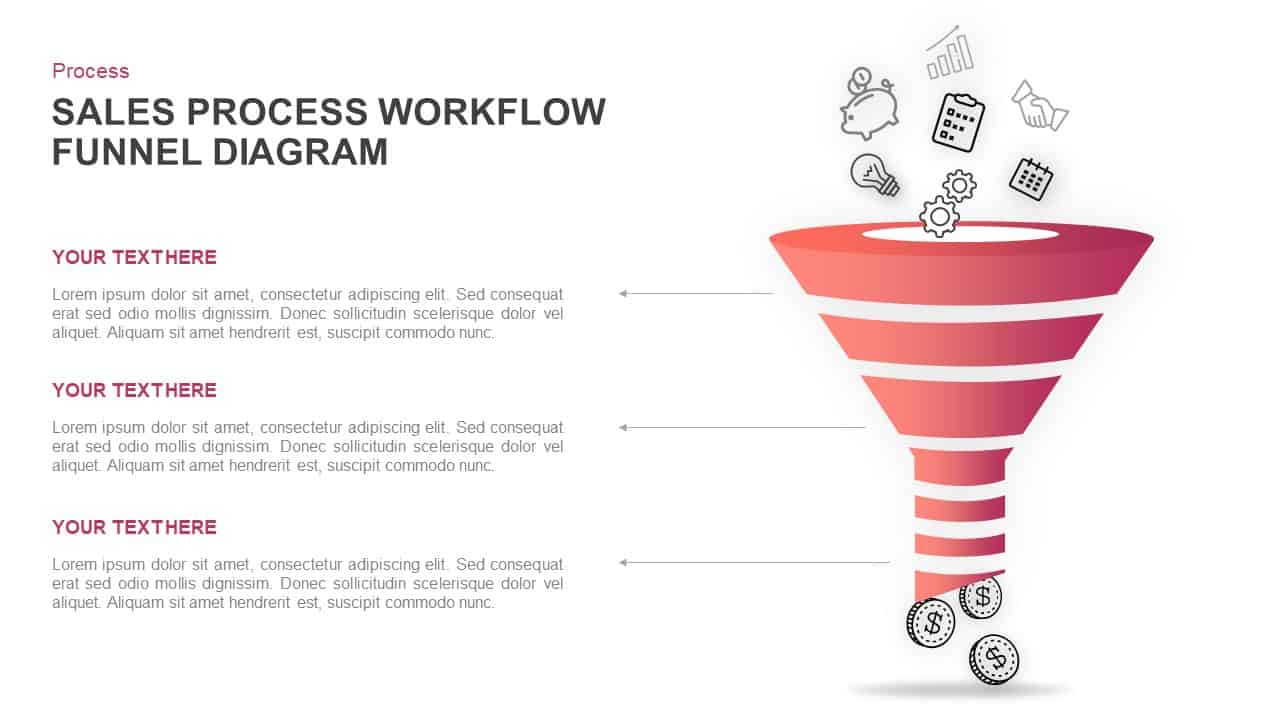
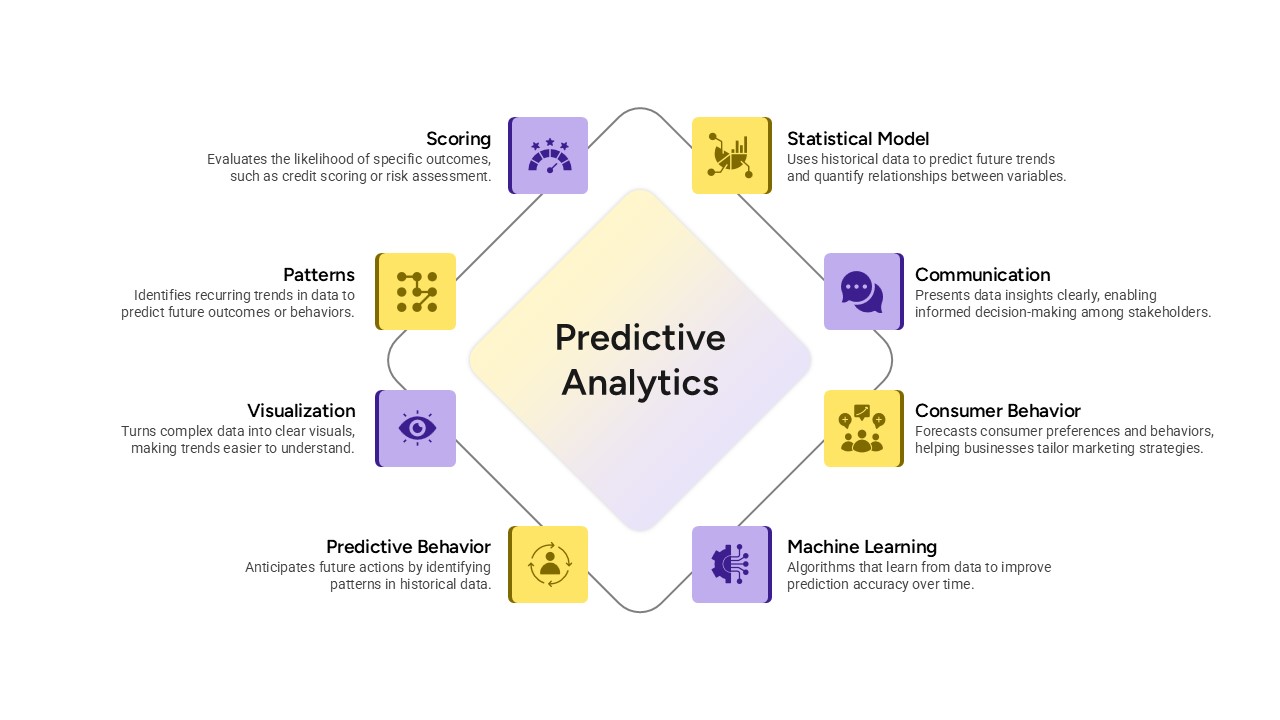
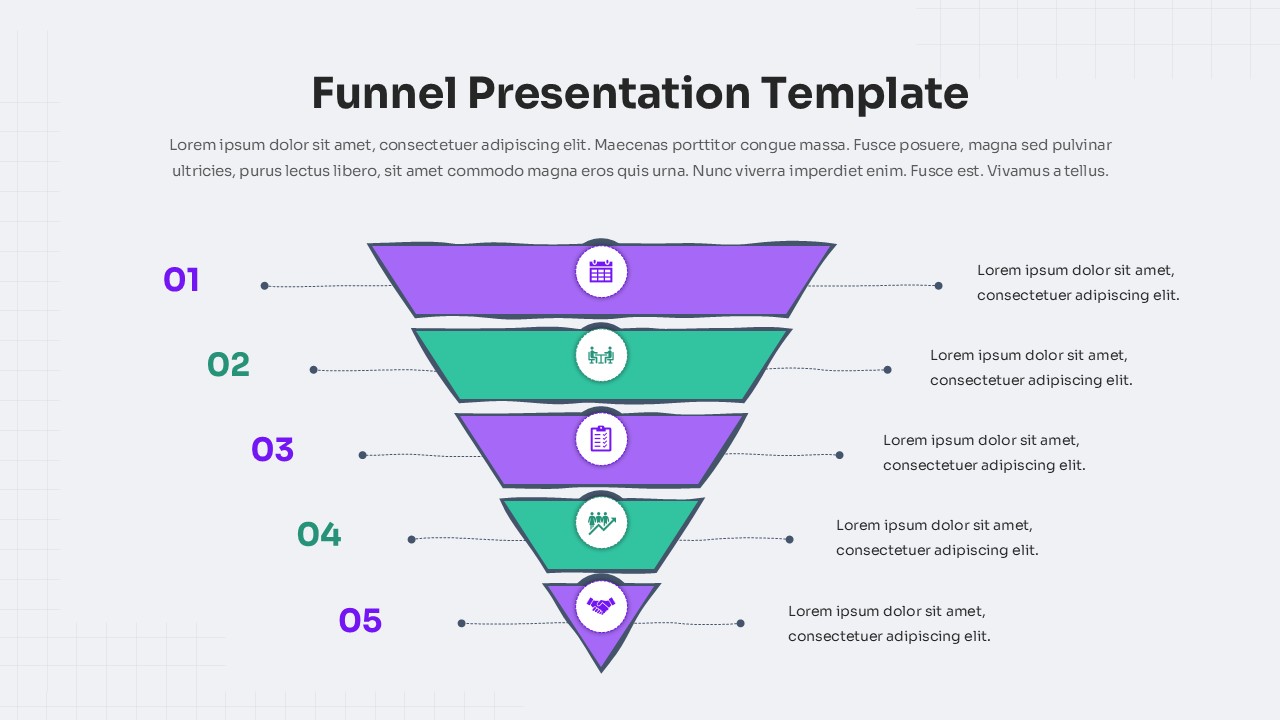
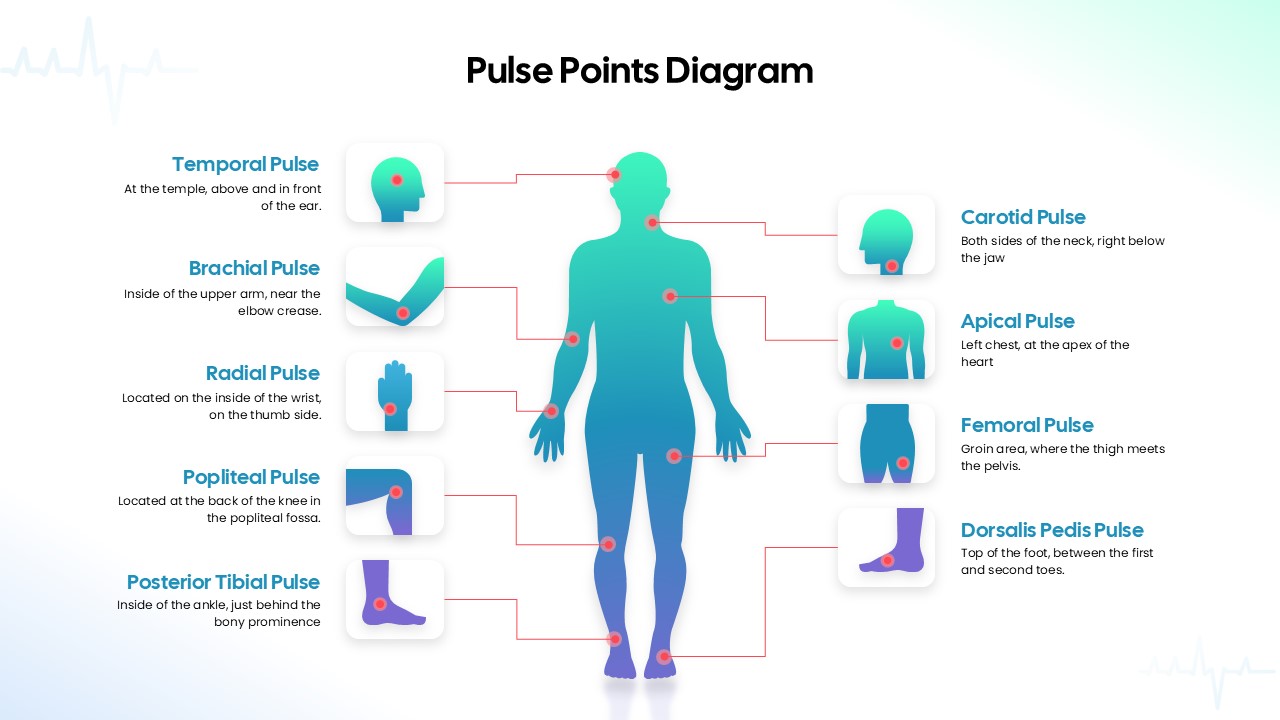
Illustrate your organization’s cybersecurity framework with this editable metaphor diagram slide, centered on a secured workstation graphic. A flat-vector lock icon sits atop a computer monitor, symbolizing robust protection, while eight surrounding asset icons—credit card, file folders, email, handshake, money bag, lightbulb, document stack, and more—connect via fine lines to highlight critical data points and risk vectors. The clean white canvas and subtle drop shadows maintain a professional aesthetic, ensuring your audience focuses on key security elements. Fully built on master slides for both PowerPoint and Google Slides, the template uses high-resolution vector shapes for seamless customization: swap out icons, adjust line colors, or replace the background scene without losing clarity or resolution.
Leverage intuitive placeholders to insert concise text callouts beside each asset icon, detailing threat scenarios, access controls, or mitigation strategies. Text boxes automatically resize to fit multi-line entries, eliminating manual adjustments. Entrance animations—such as fade-in or wipe—can be applied individually to icons and callouts, guiding viewers through your narrative in a controlled, step-by-step fashion. Whether you’re presenting to executives, training IT staff, or briefing non-technical stakeholders, this slide ensures complex cyber threats become clear, actionable insights.
Who is it for
IT security teams, CIOs, and risk management professionals will find this diagram invaluable for mapping vulnerability assessments, compliance frameworks, and incident-response workflows. Consultants, auditors, and corporate trainers can also leverage the metaphor to educate cross-functional teams on best practices and security protocols.
Other Uses
Beyond cybersecurity, repurpose this hub-and-spoke layout to visualize data governance models, privacy compliance touchpoints, or third-party vendor assessments. Customize the central icon and peripheral graphics to suit network topology overviews, cloud-security roadmaps, or digital-transformation initiatives—providing a versatile asset across any technology-focused presentation.
Login to download this file