Cyber Security Dark Blue Gradient Template for PowerPoint & Google Slides
Description
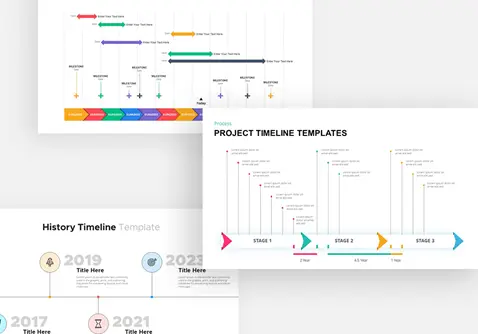
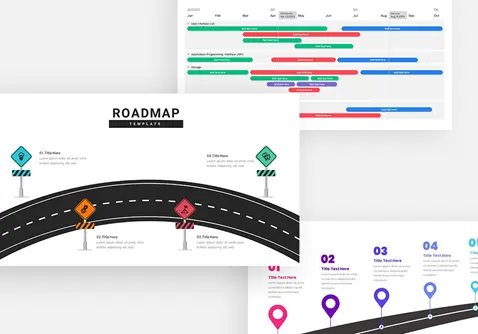
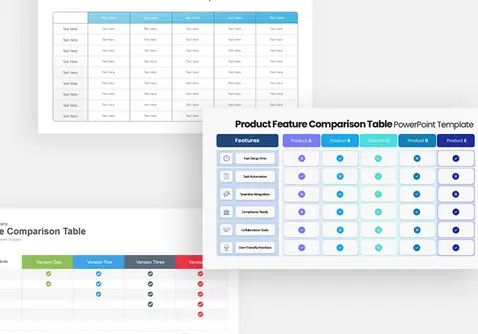
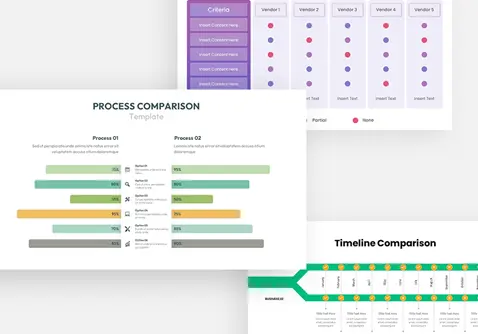
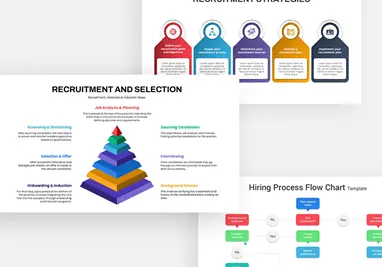
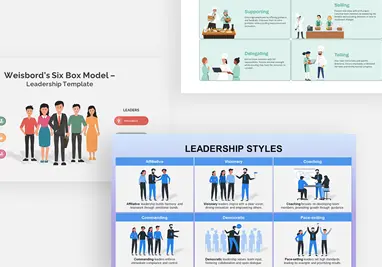
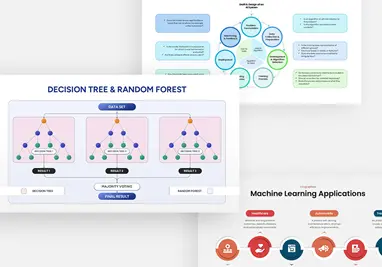
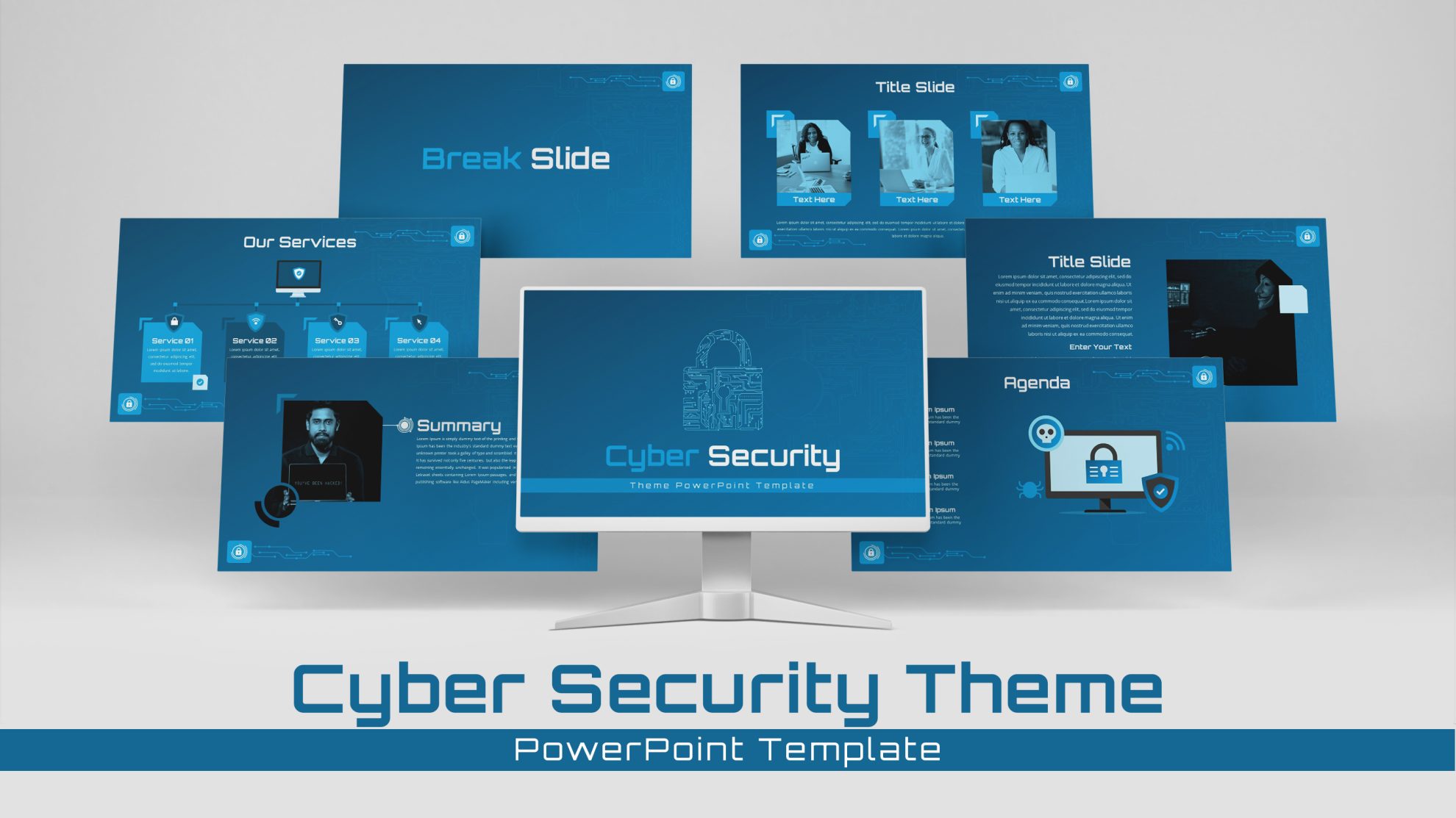
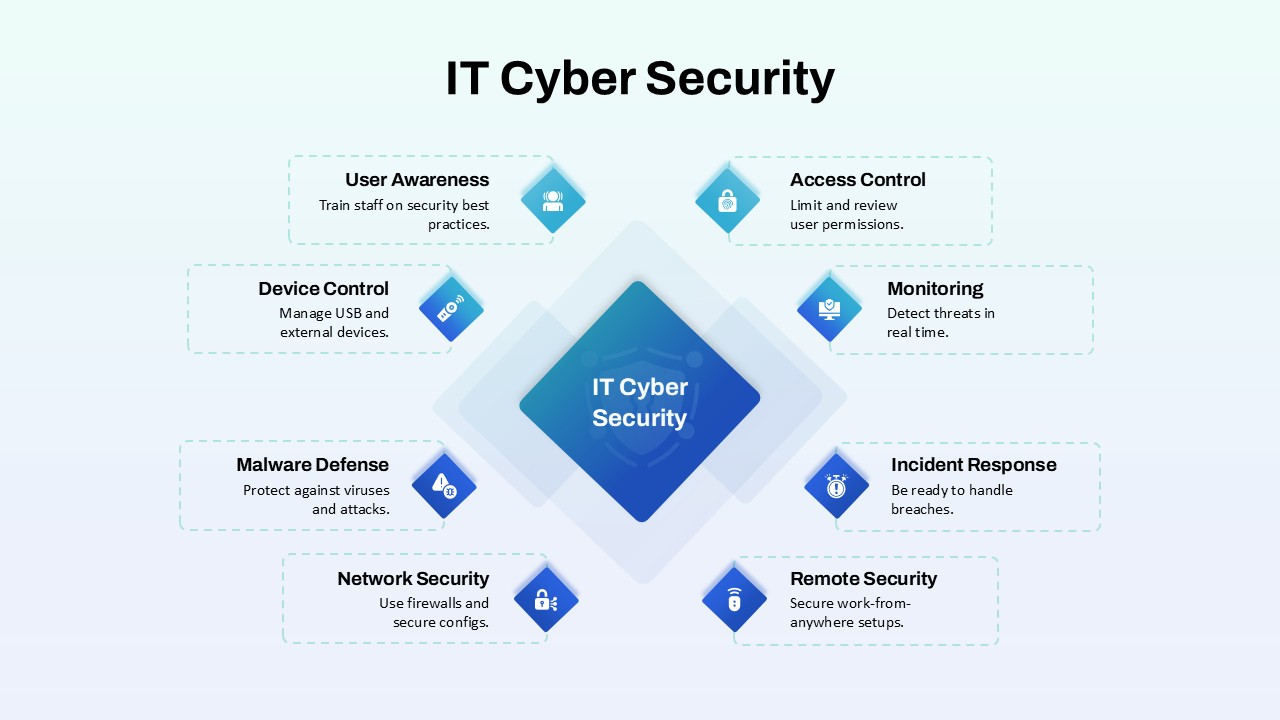
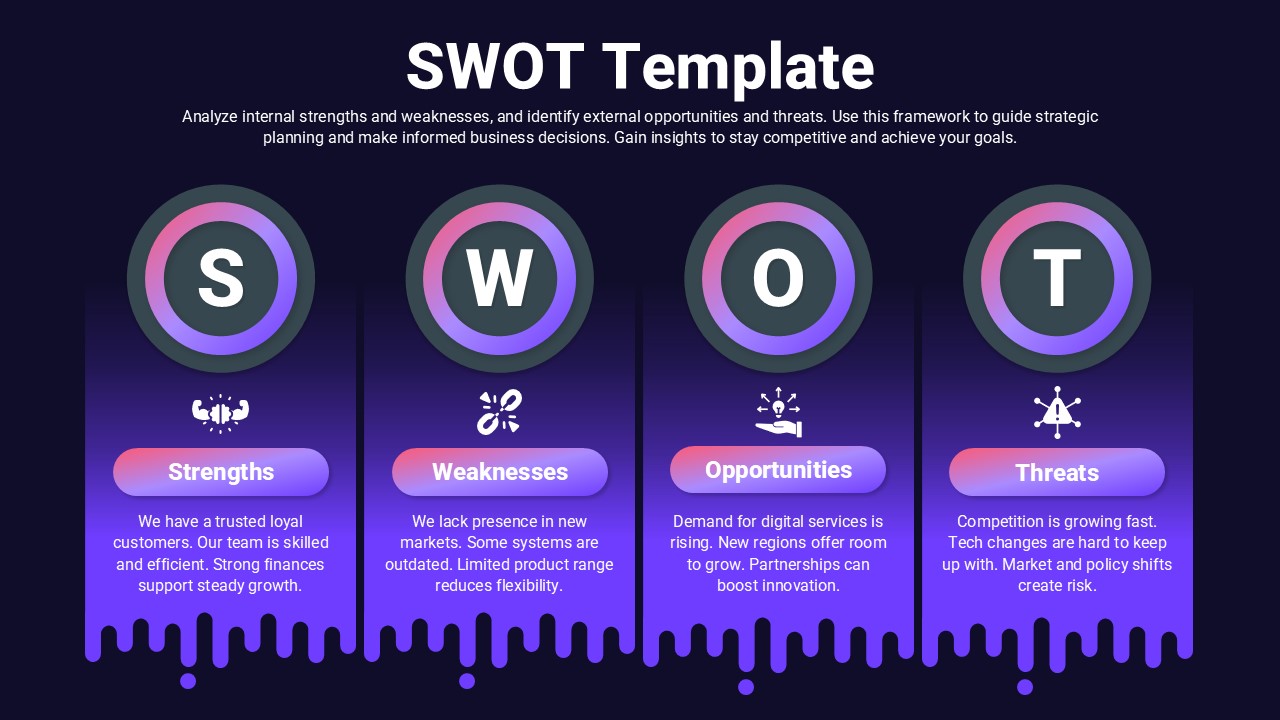
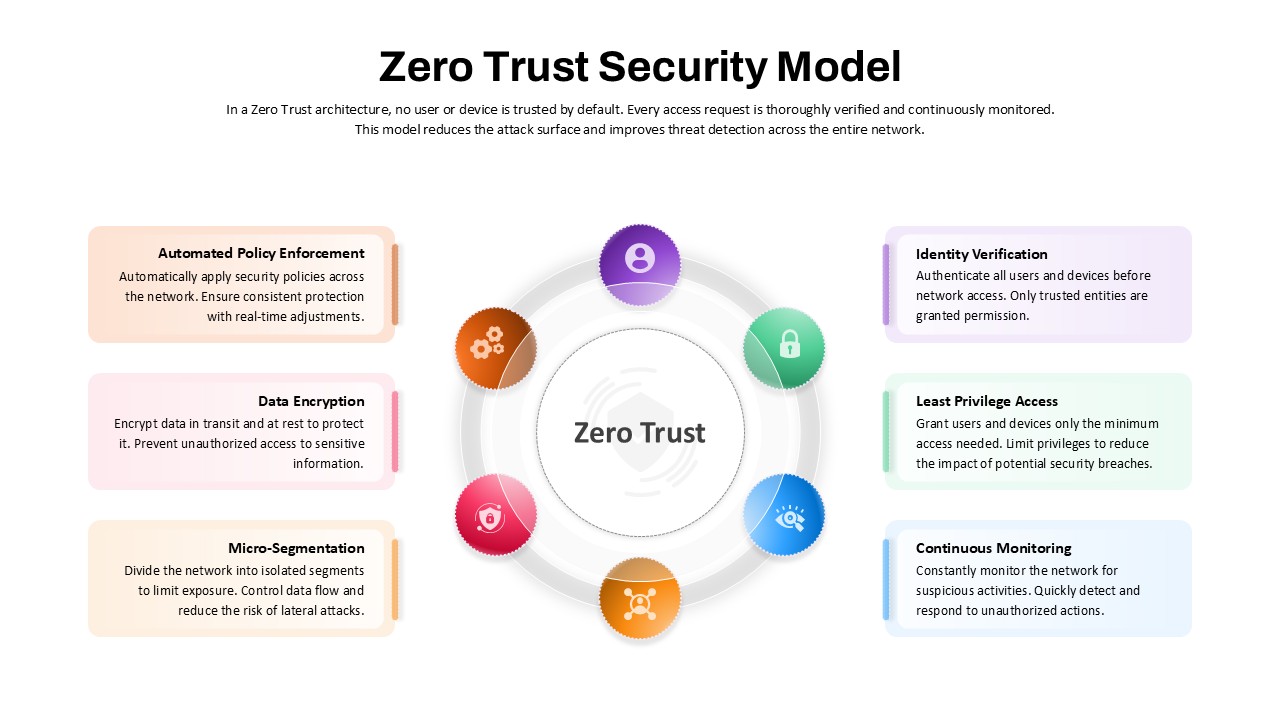
Protect your narrative with this Cyber Security template, featuring a rich dark-blue gradient backdrop layered over subtle circuit-board motifs and shield icons. The deck opens with a striking title slide that blends futuristic typography with a secure-lock watermark, setting a confident tone. Core layouts include a versatile title‐and‐image grid for showcasing threat landscapes, a break slide for visual pauses, and a configurable agenda slide with checkbox bullets alongside a hi-res shield graphic. Detailed content slides balance text blocks with corner-cut image placeholders—ideal for illustrating access controls, network mapping, or incident-response workflows. An “Add Infographics” master slide offers a crisp white canvas trimmed with angular corners for seamless data visualization integration.
Every element is fully editable in both PowerPoint and Google Slides: swap out images, adjust the gradient angle, modify font weights, or reposition graphic accents via built-in master layouts. The unified color scheme and consistent iconography streamline slide assembly, enabling teams to maintain brand compliance while emphasizing security best practices. Whether you’re briefing executives on risk mitigation, training staff on secure protocols, or pitching managed-security services, this template accelerates production and ensures a polished, professional delivery without sacrificing clarity or impact.
Who is it for
IT security managers, network architects, compliance officers, and cyber-risk consultants will find this template invaluable for boardroom briefings, technical roadshows, and client proposals. Operations teams and incident-response leaders can also leverage its structured layouts to document threats, outline remediation plans, and report metrics.
Other Uses
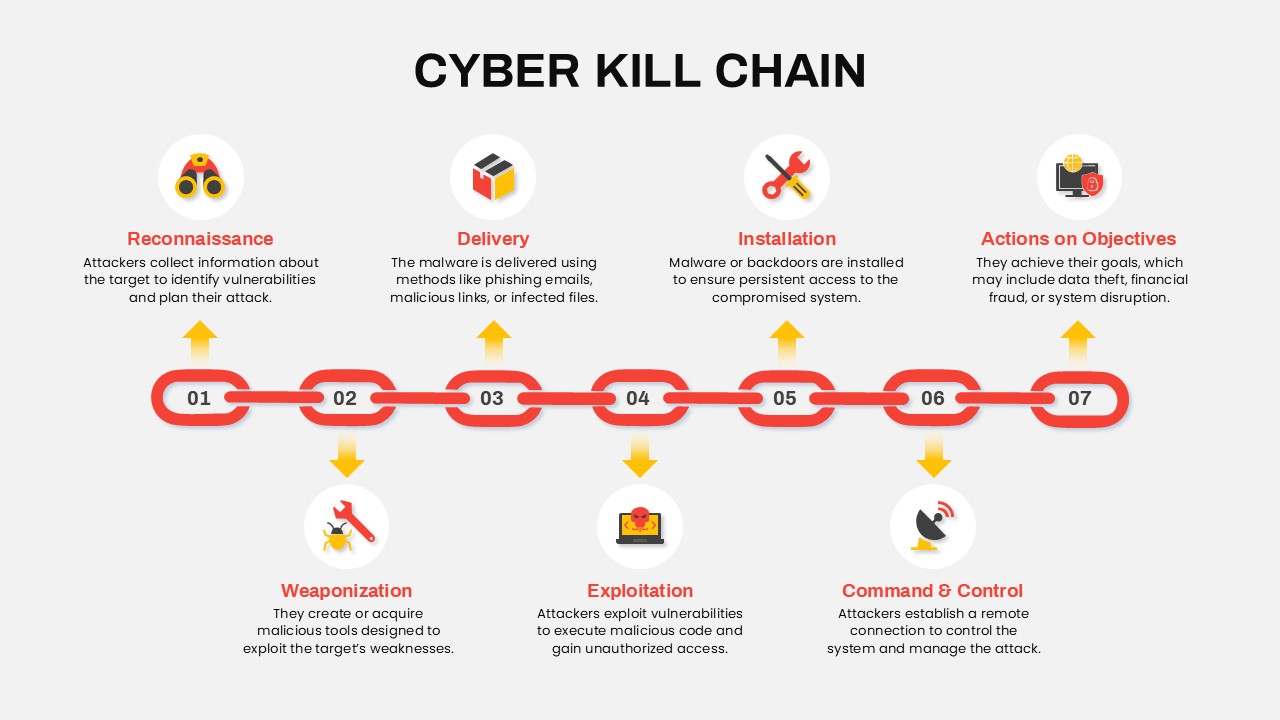
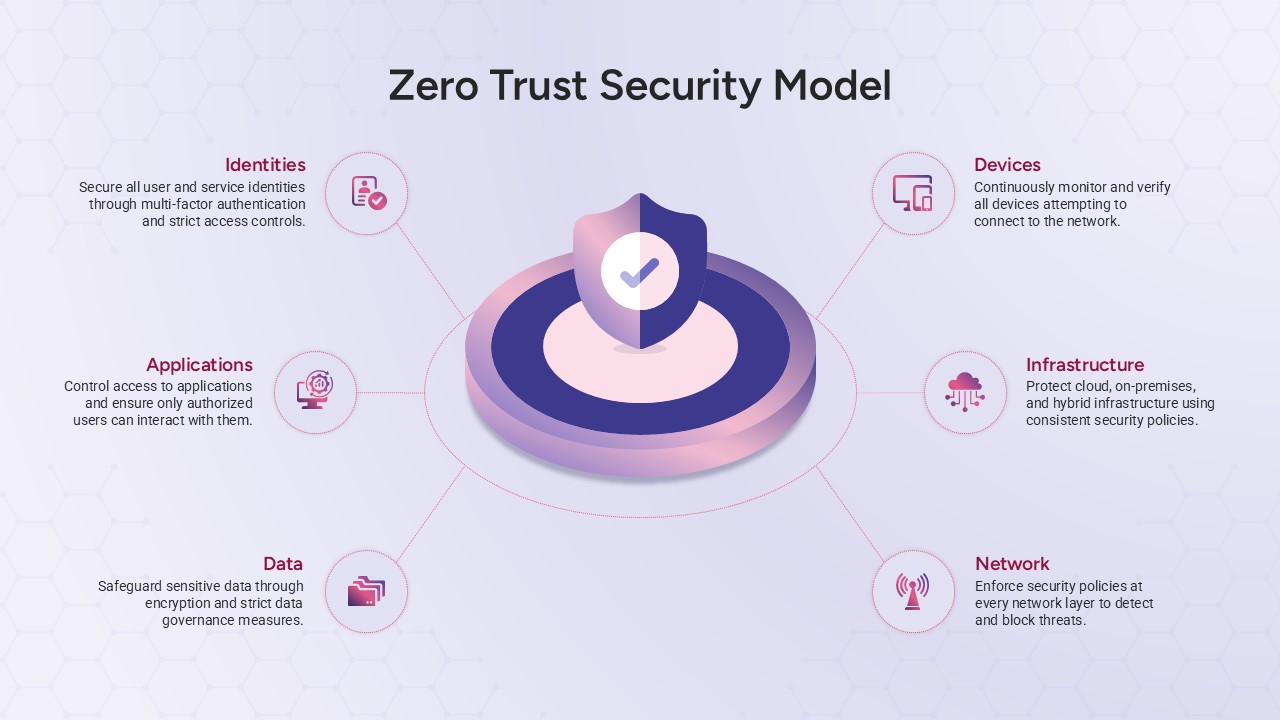
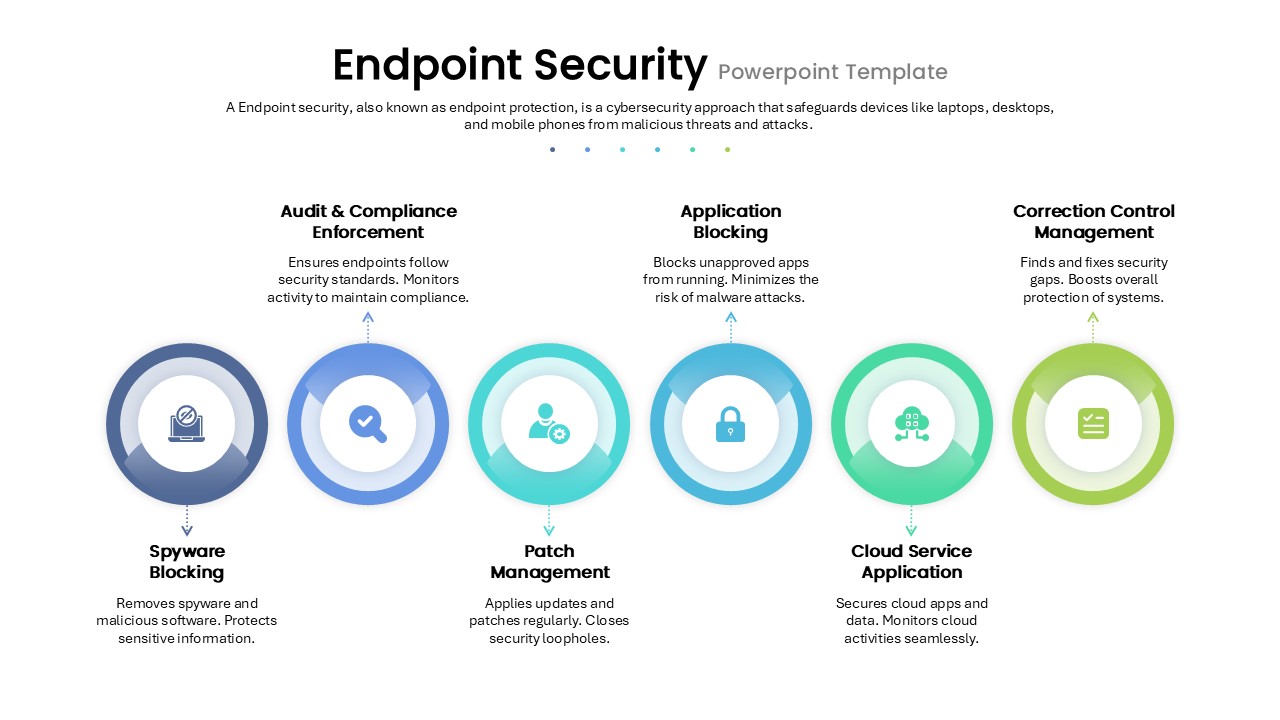
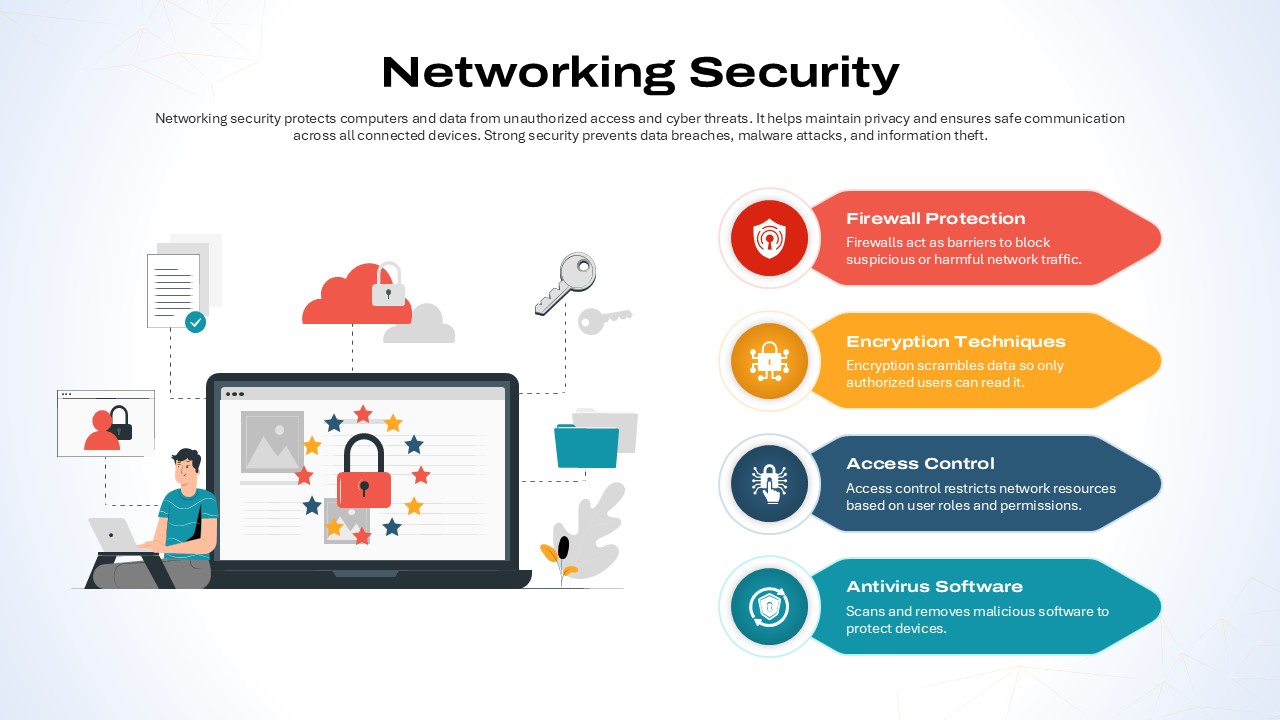
Repurpose slides for vulnerability assessments, penetration-test reports, security-awareness workshops, or vendor comparisons. Use the infographics slide to visualize firewall status, threat-actor kill chains, or compliance checklists.
Login to download this file