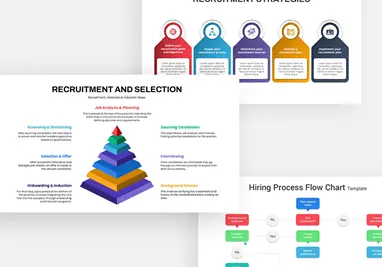
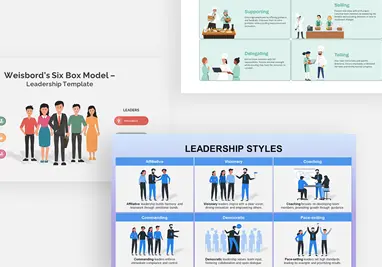
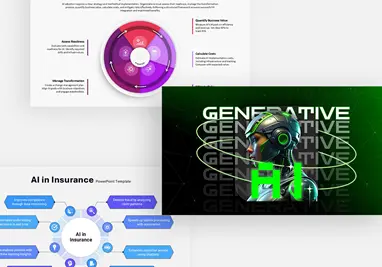
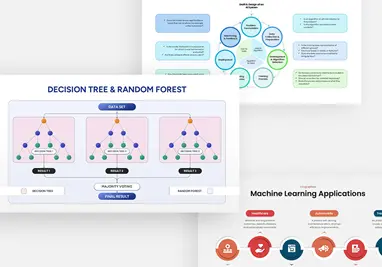
Cybersecurity Shield Hexagon Tech Template for PowerPoint & Google Slides
Description
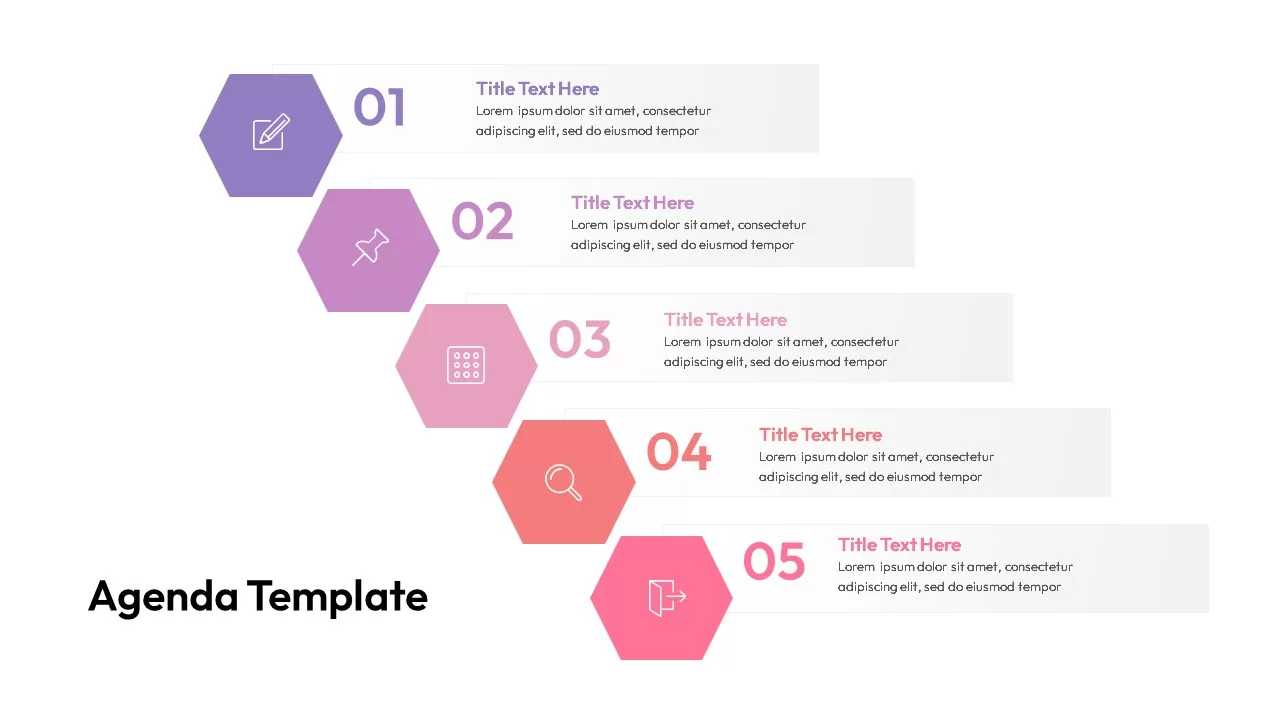
Leverage this cutting-edge cybersecurity template to convey digital protection strategies with striking neon accents and sleek geometric layouts. The dark navy background sets a professional tone, while glowing cyan orbs and subtle circuit-board patterns establish a high-tech atmosphere. Begin with a bold title slide featuring a shield icon encircled by digital telemetry rings, then transition into an agenda slide that pairs crisp bullet points with a hexagonal image frame for visual emphasis.
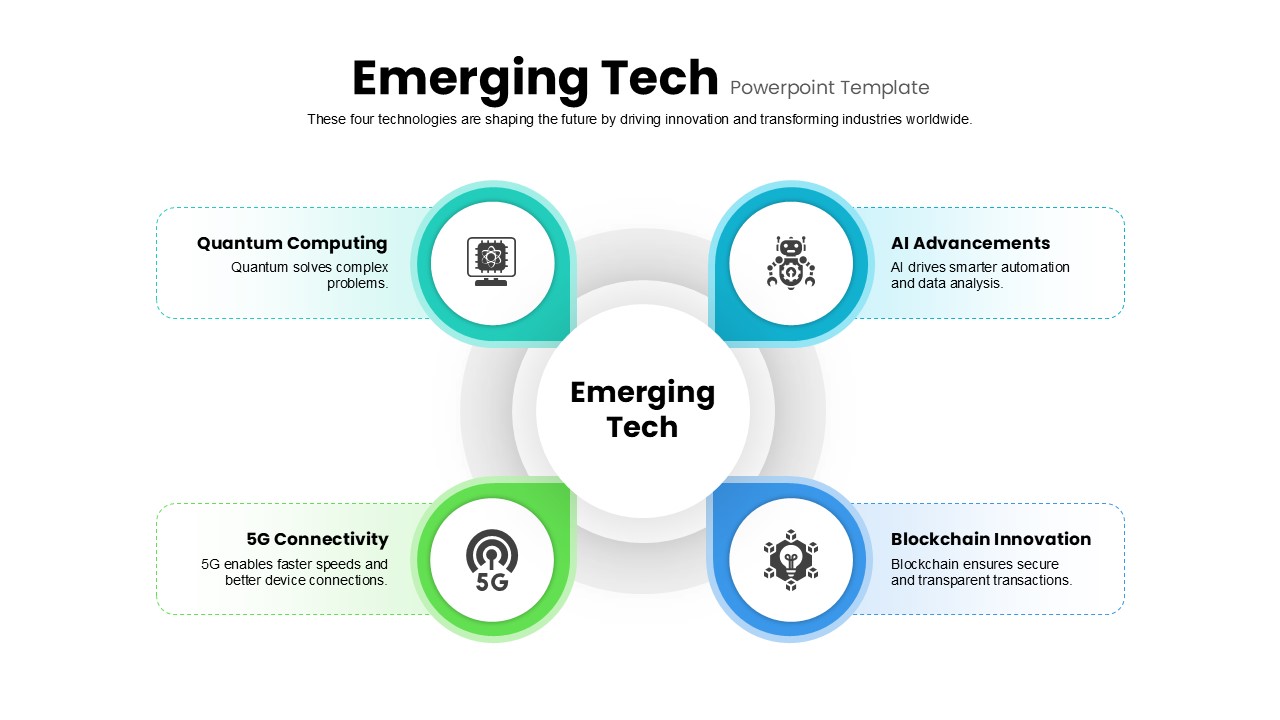
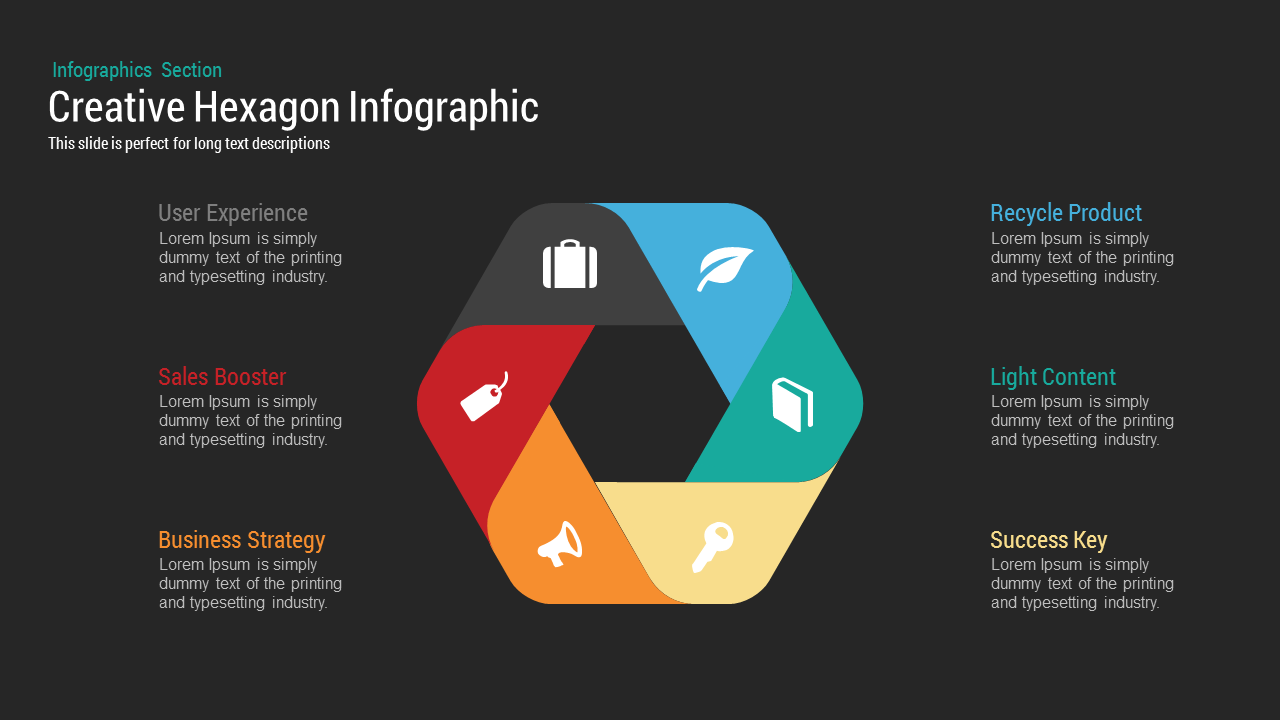
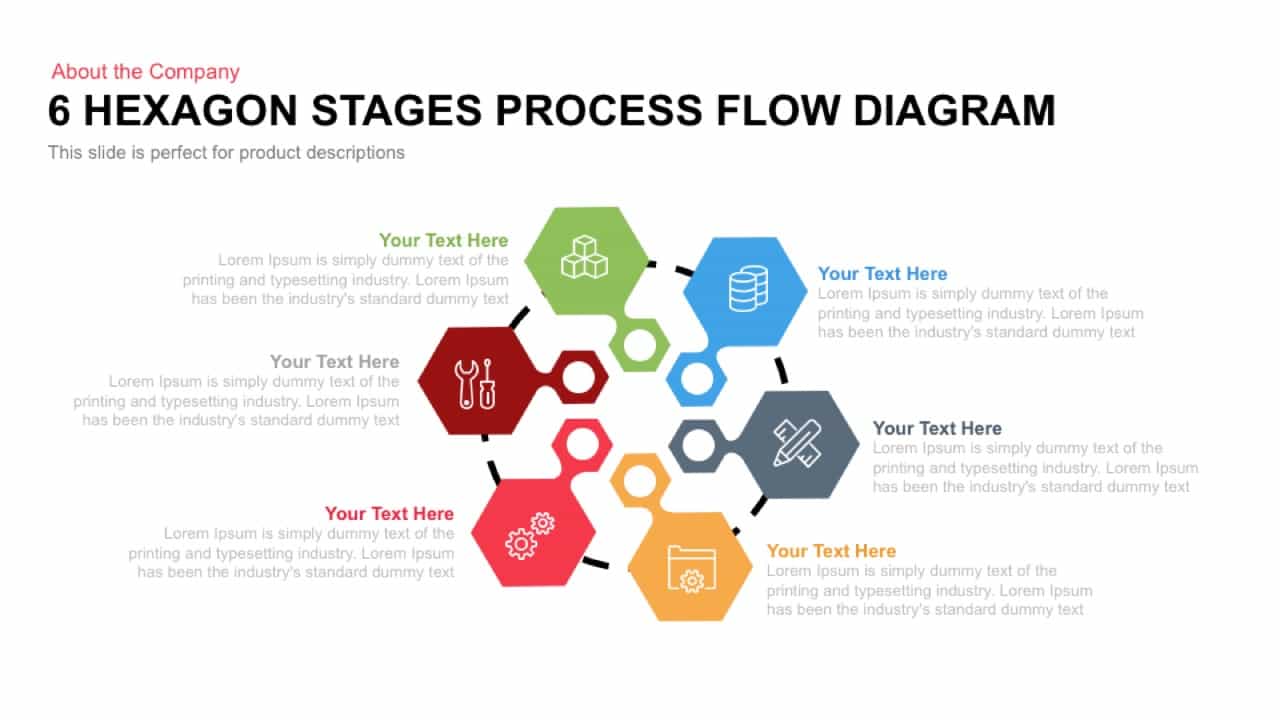
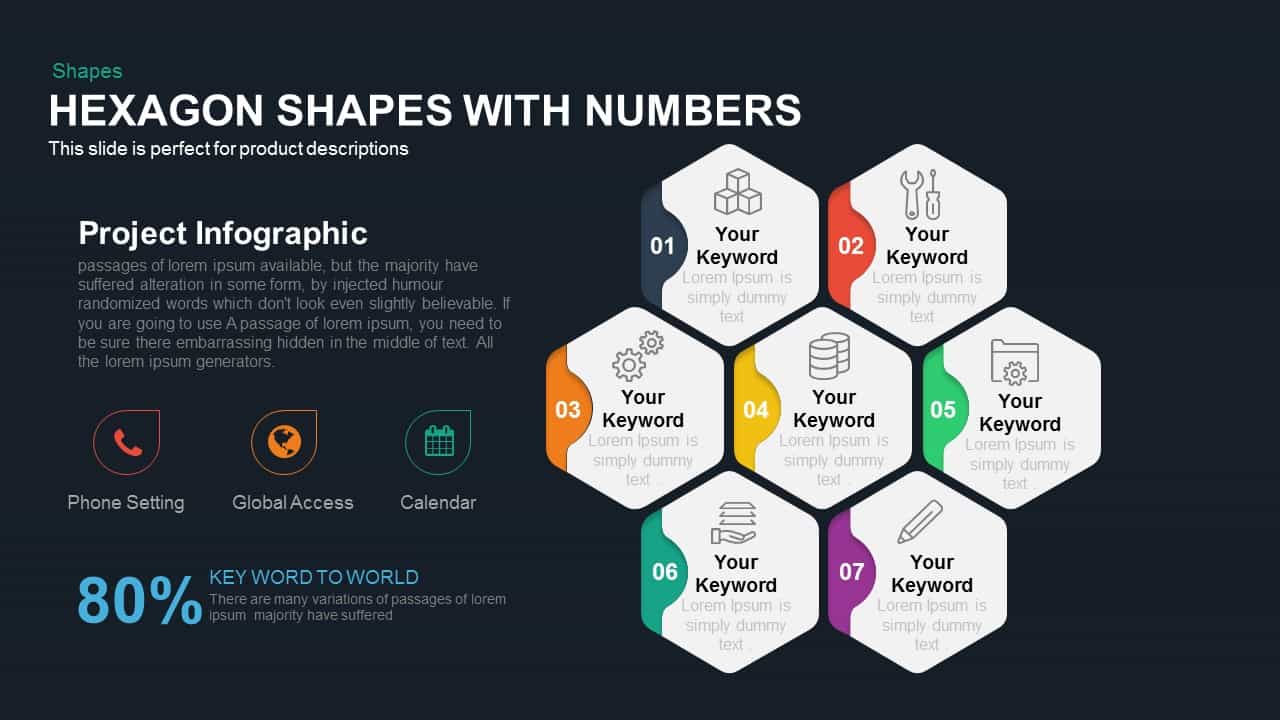
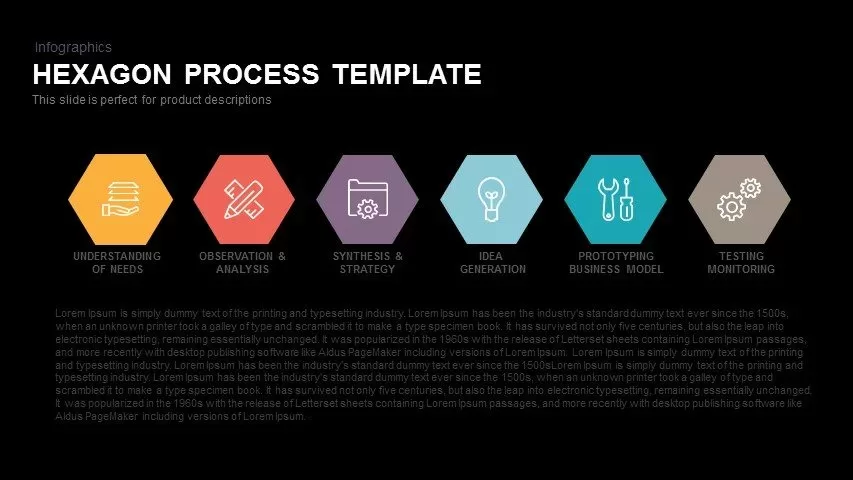
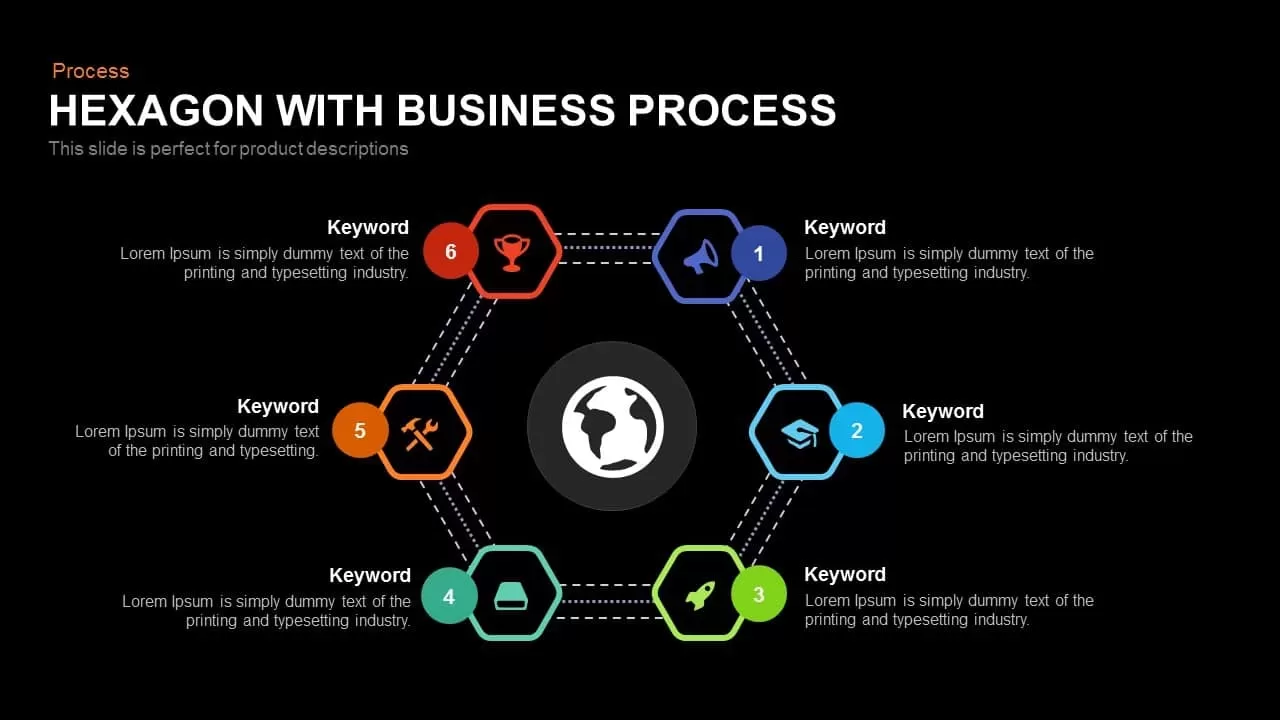
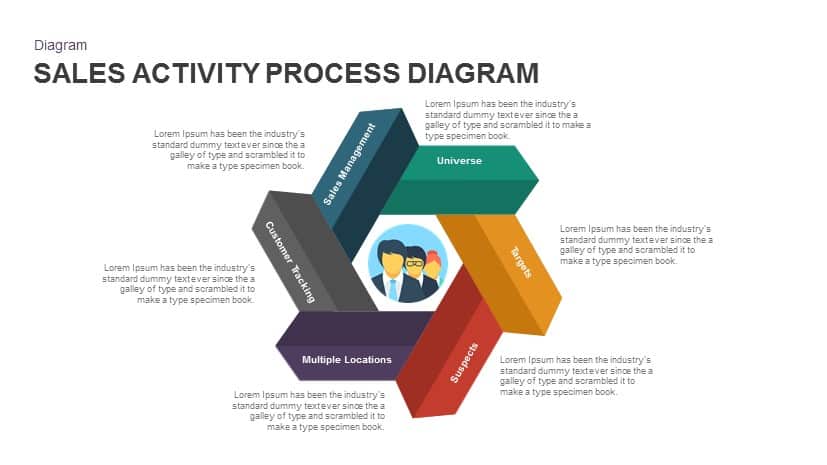
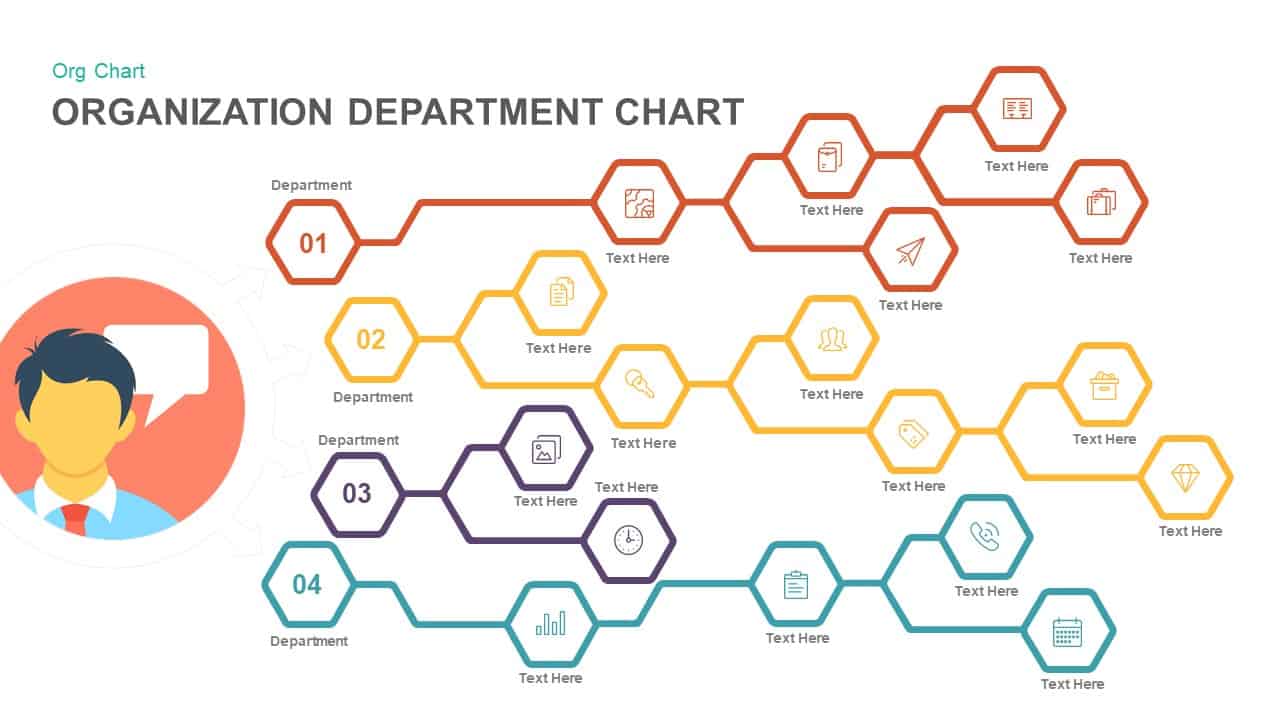
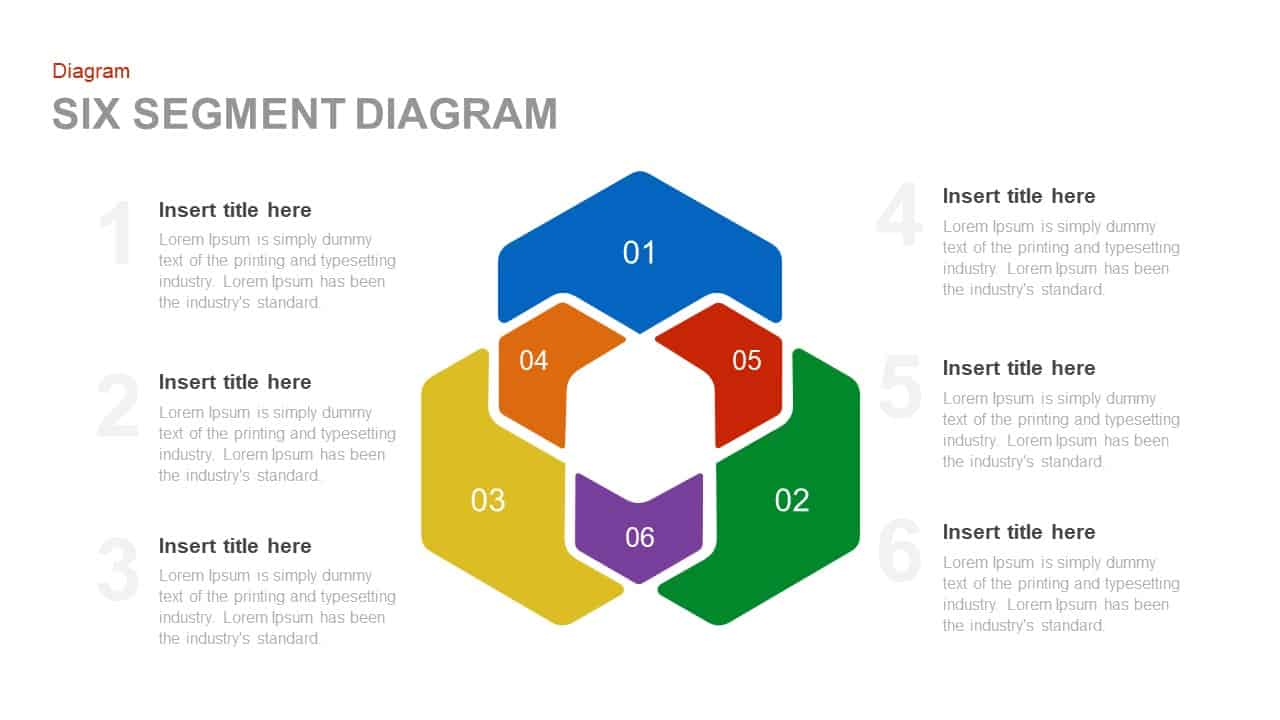
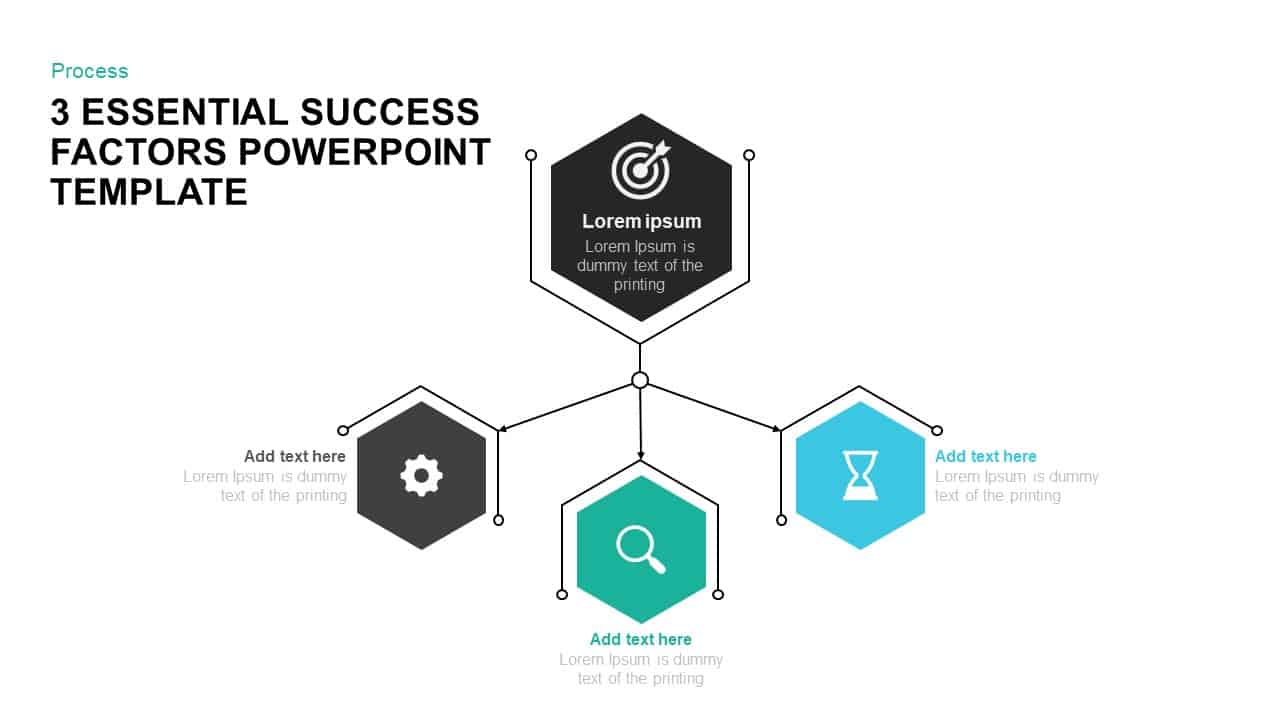
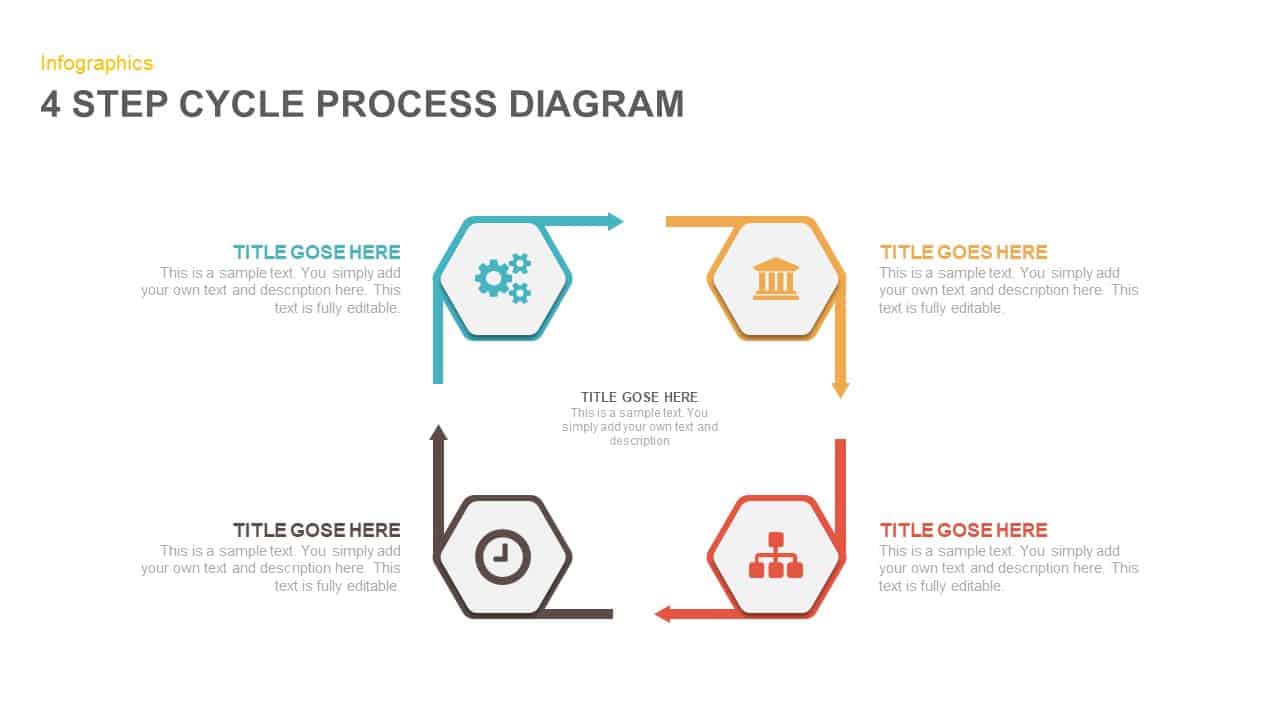
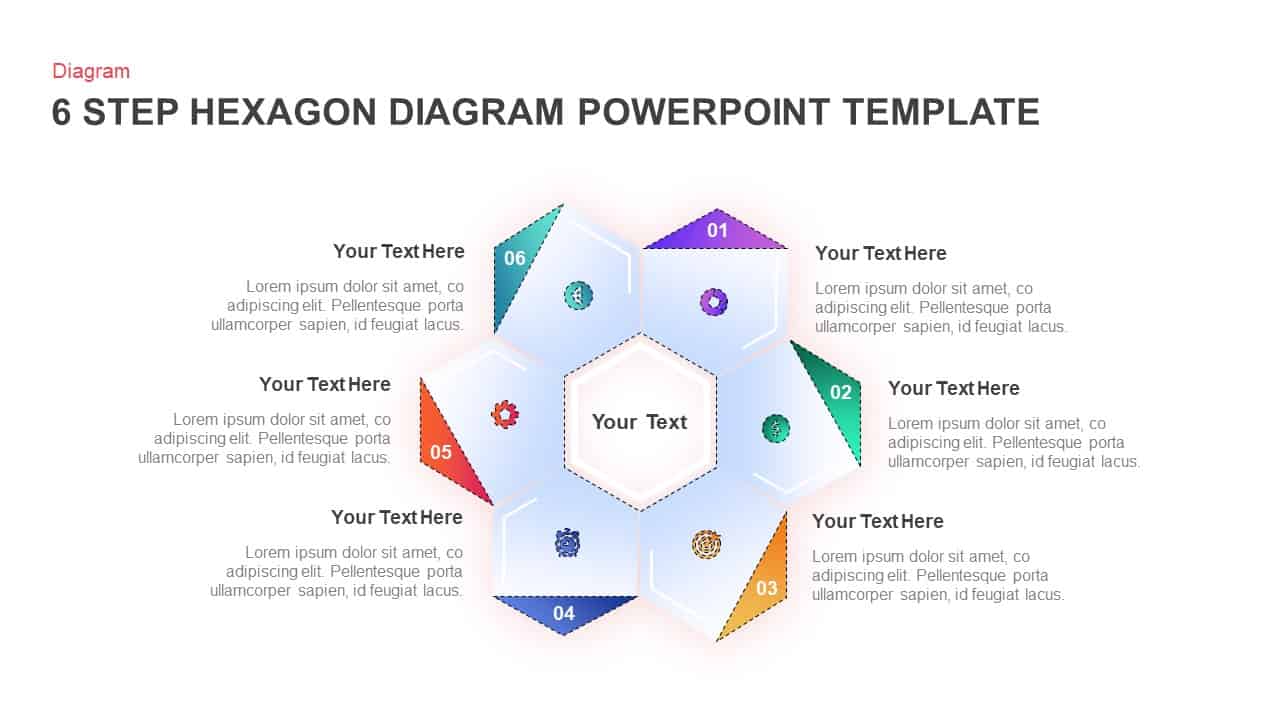
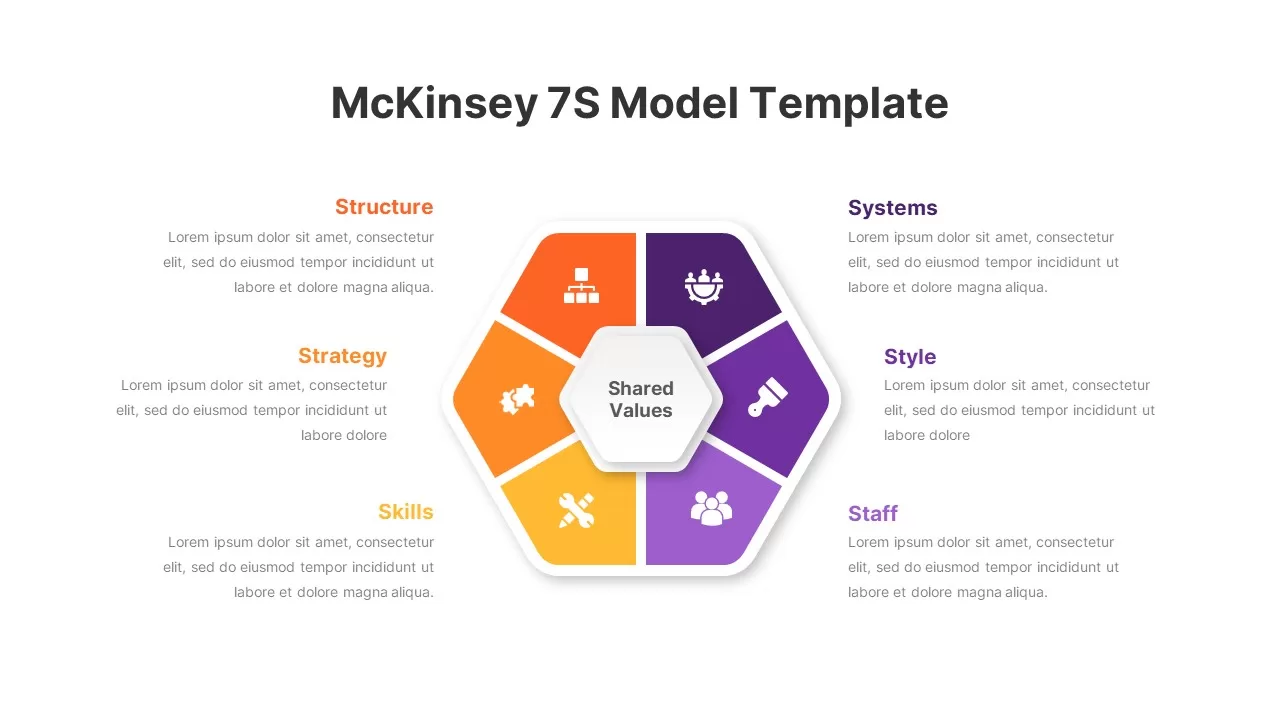
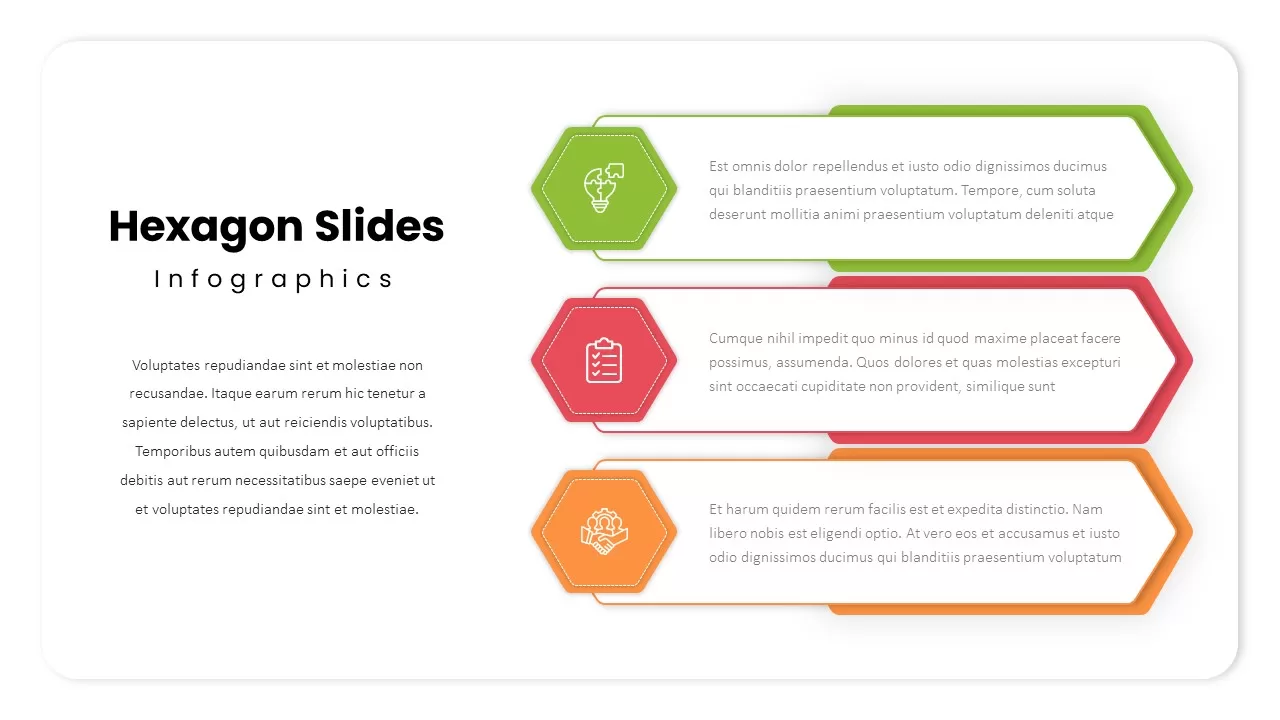
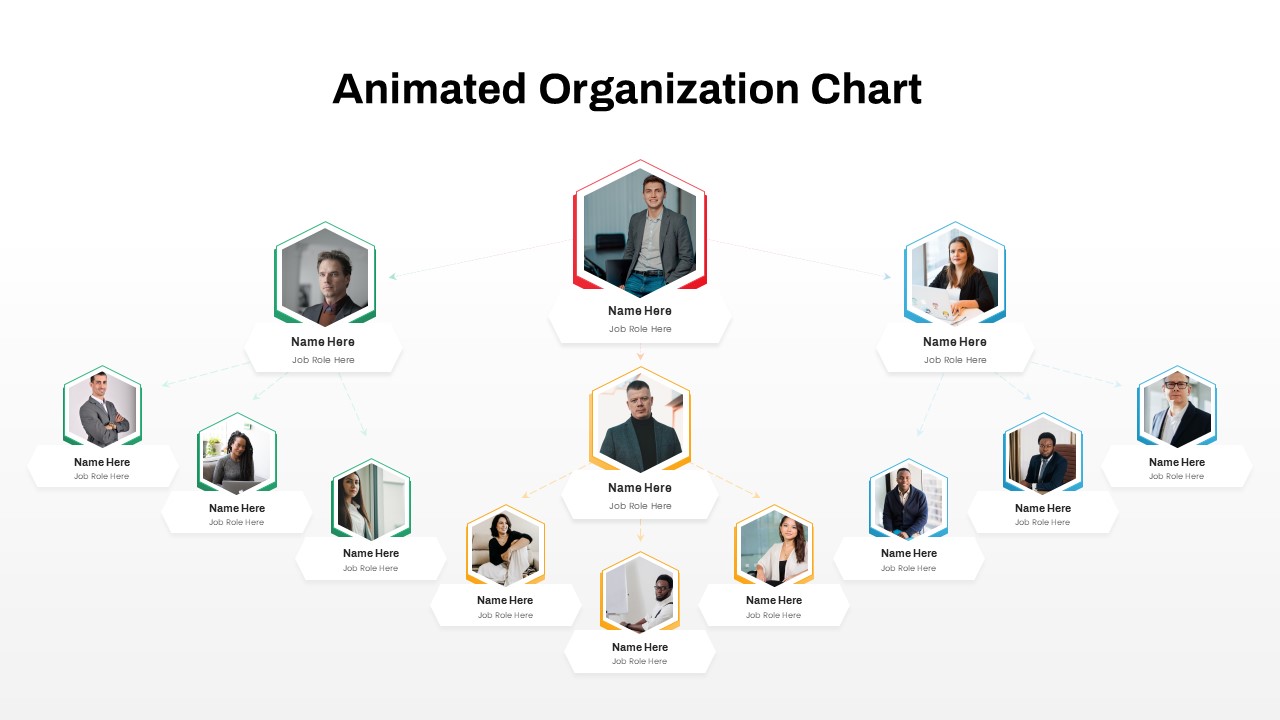
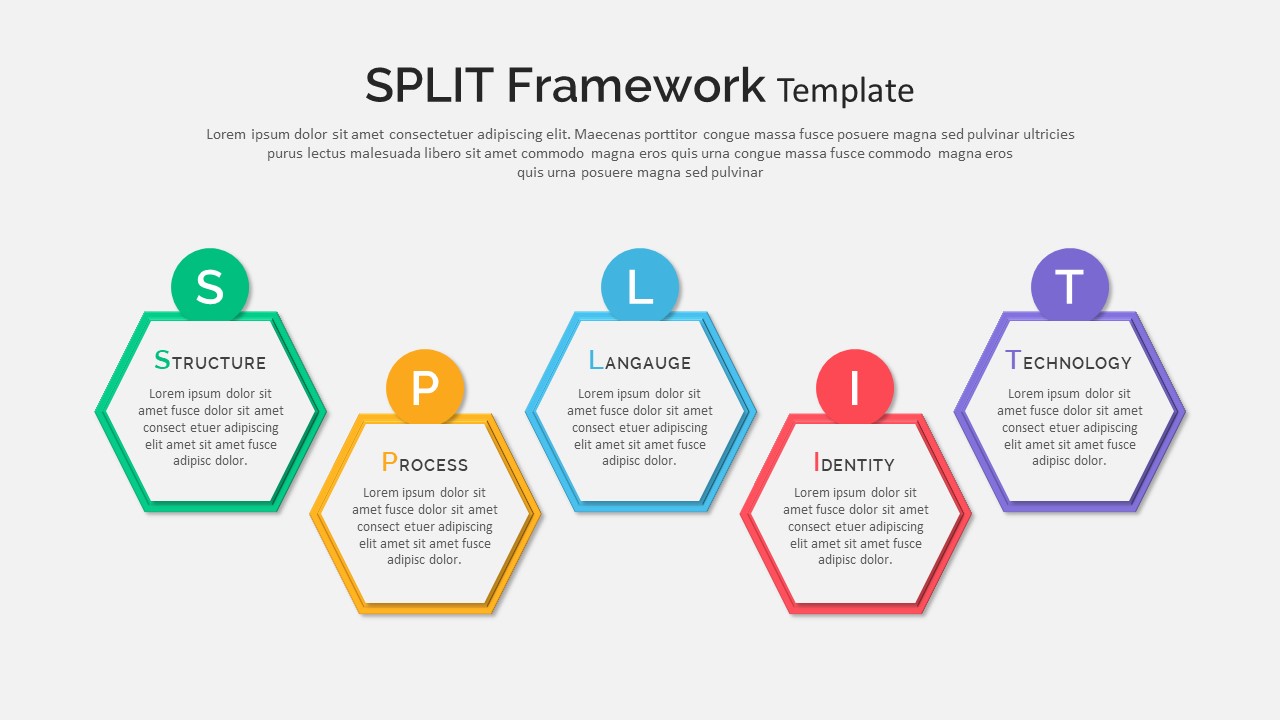
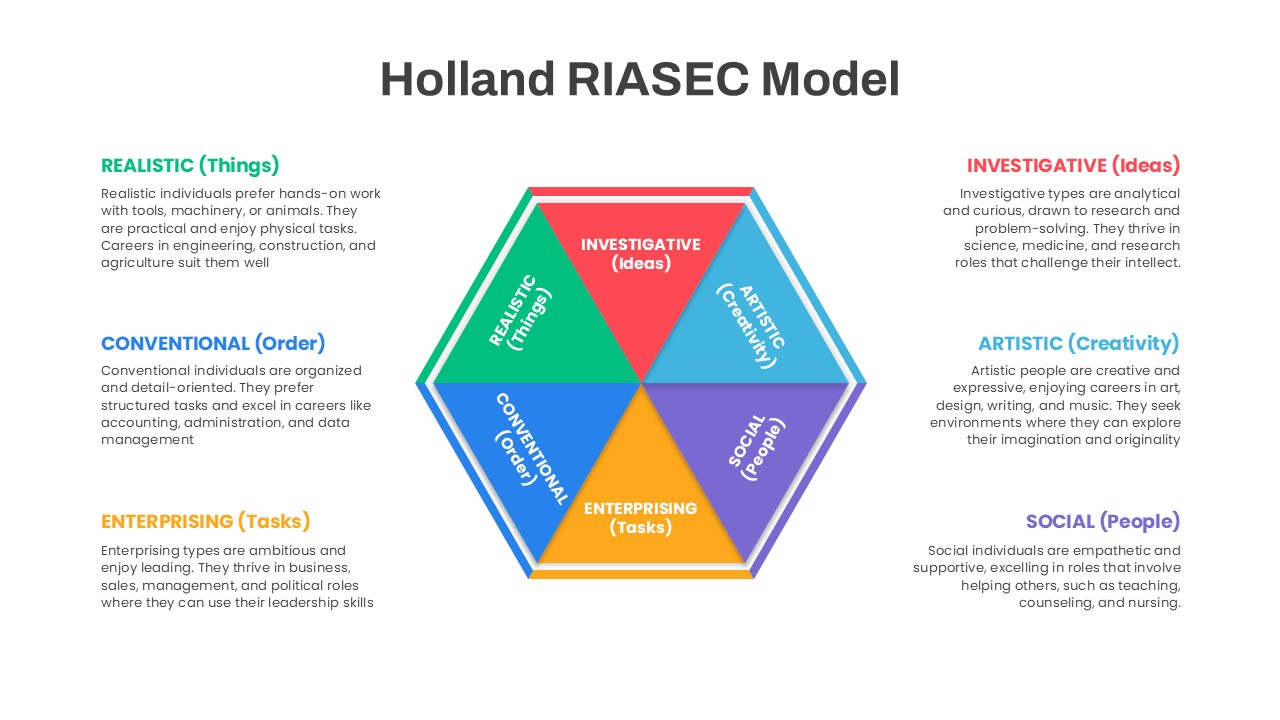
Subsequent content slides offer versatile split layouts: showcase key insights alongside thematic icons and translucent hexagon overlays, or position large multimedia graphics within angular panels to reinforce critical messaging. Highlight up to three core services or solutions on a dedicated feature slide, each presented in its own hexagon-topped panel with customizable iconography and bullet callouts.
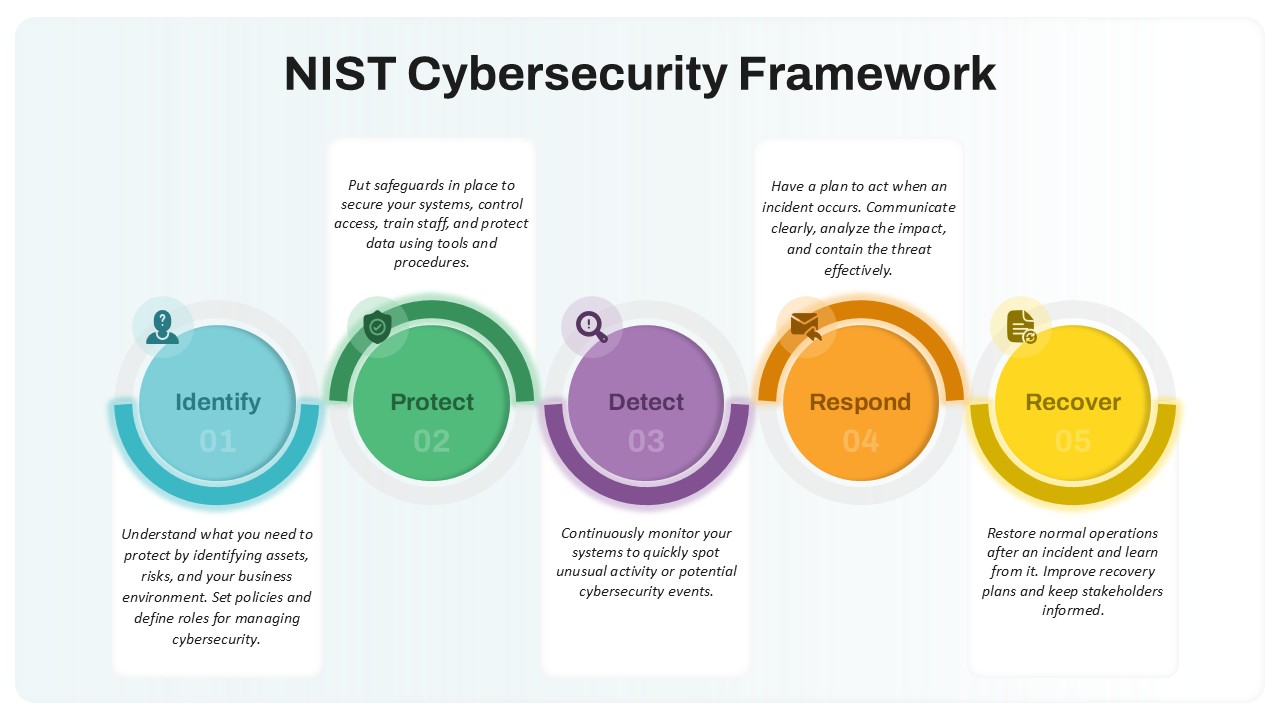
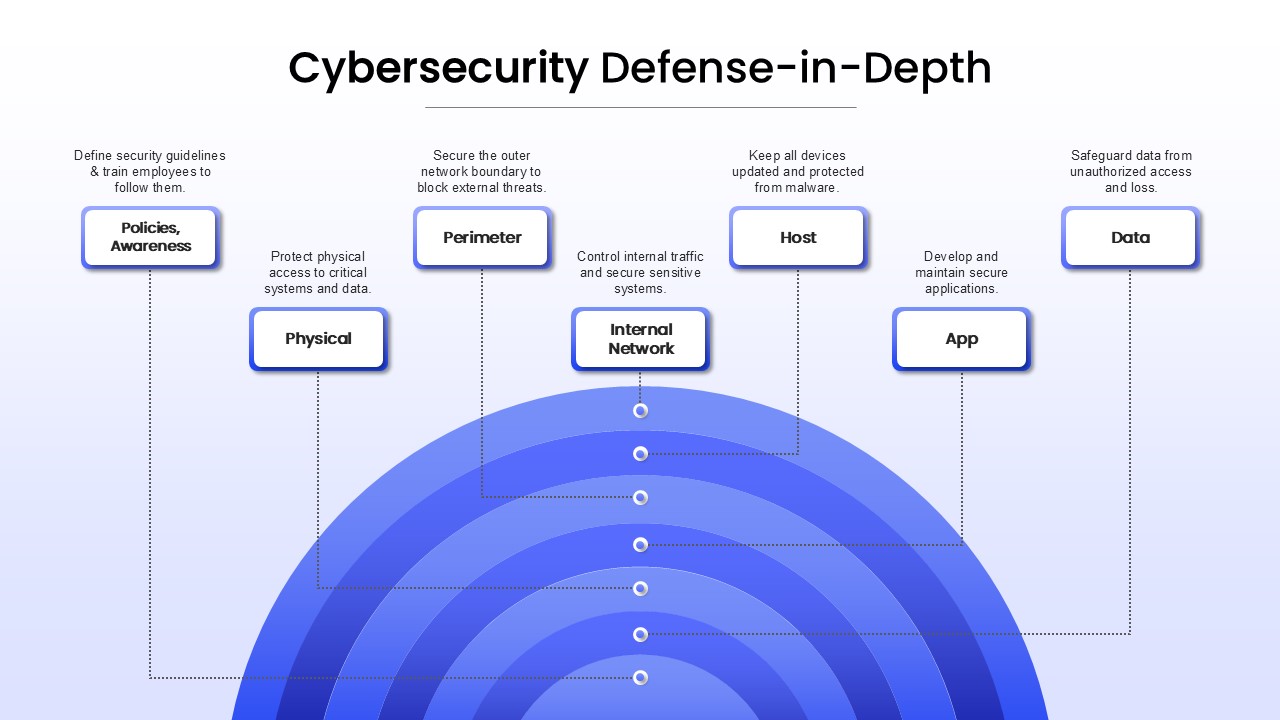
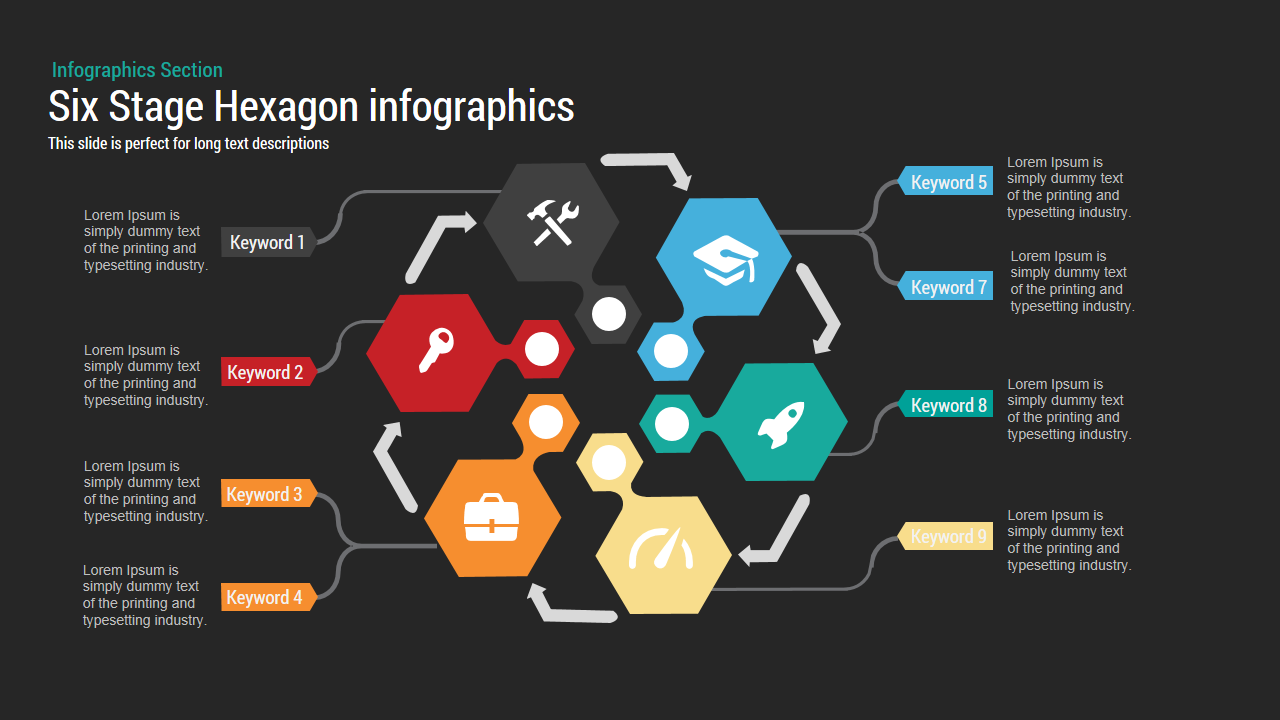
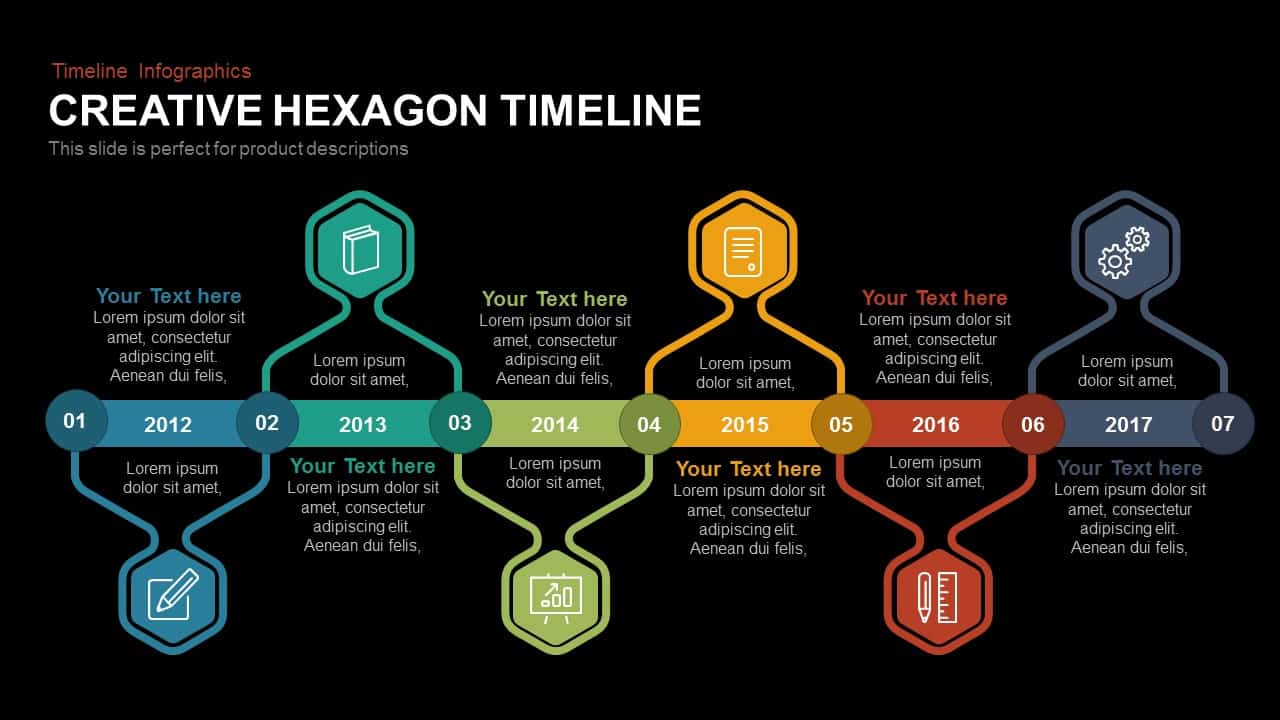
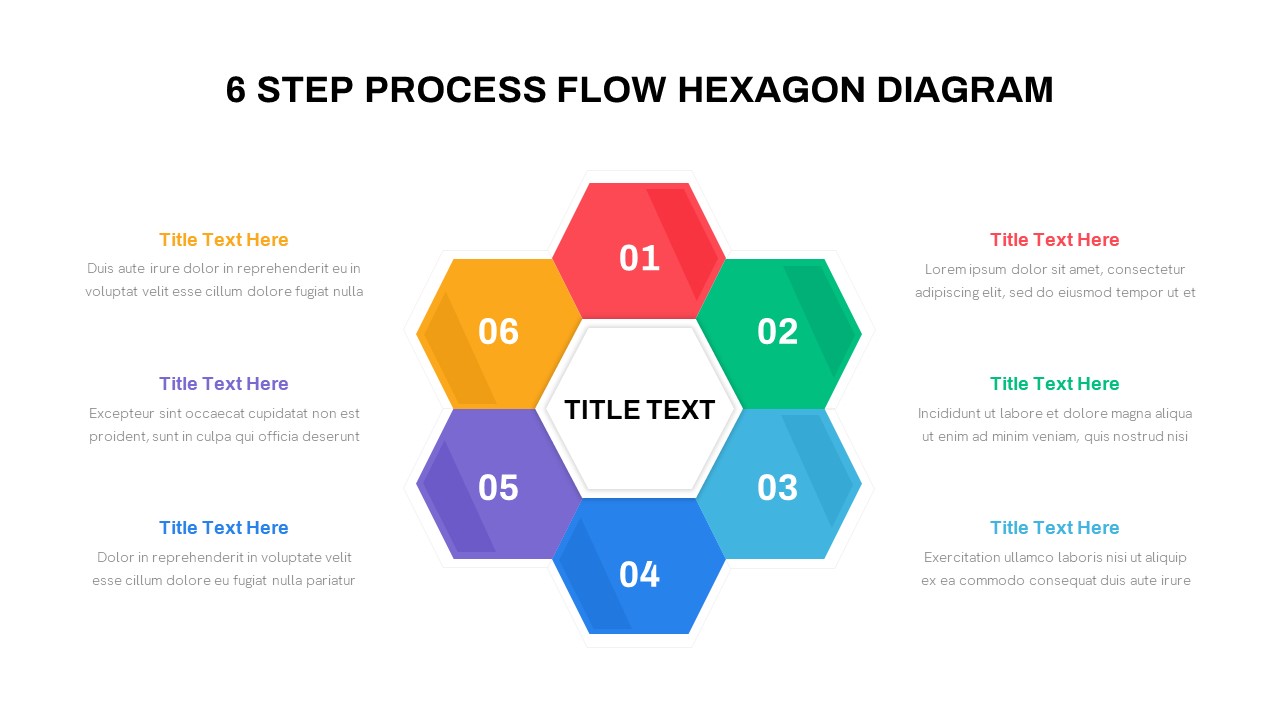
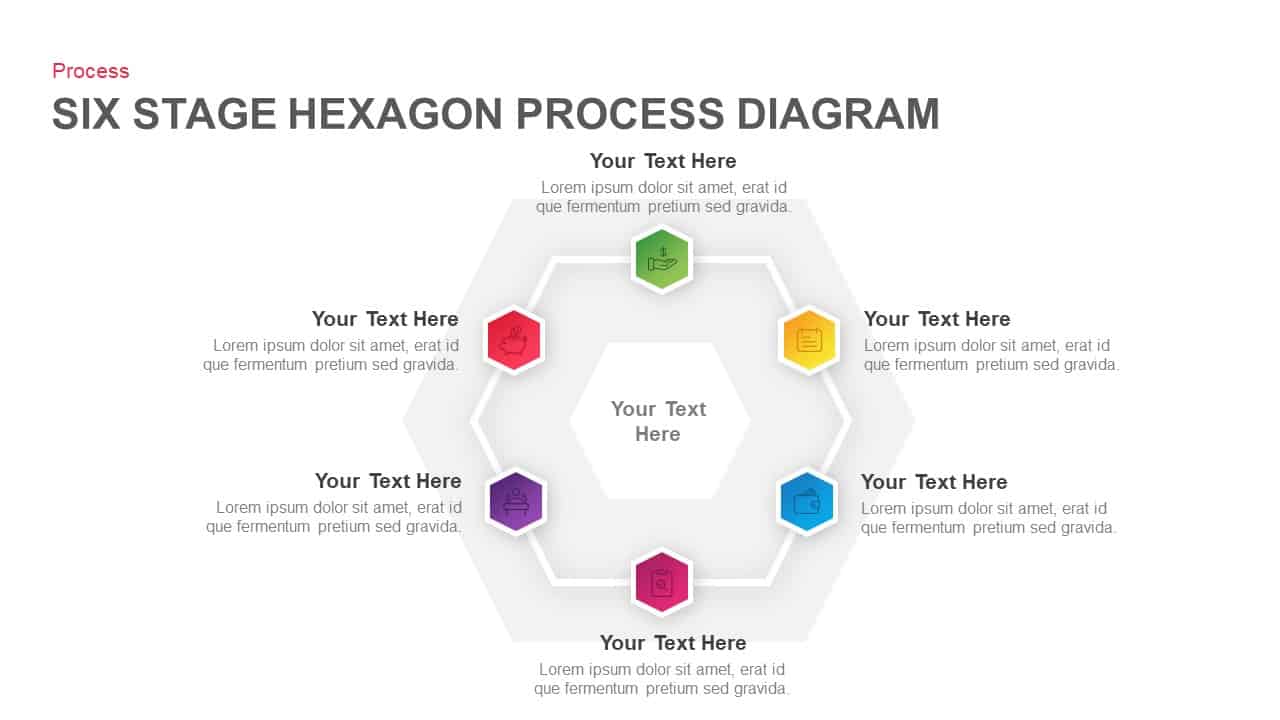
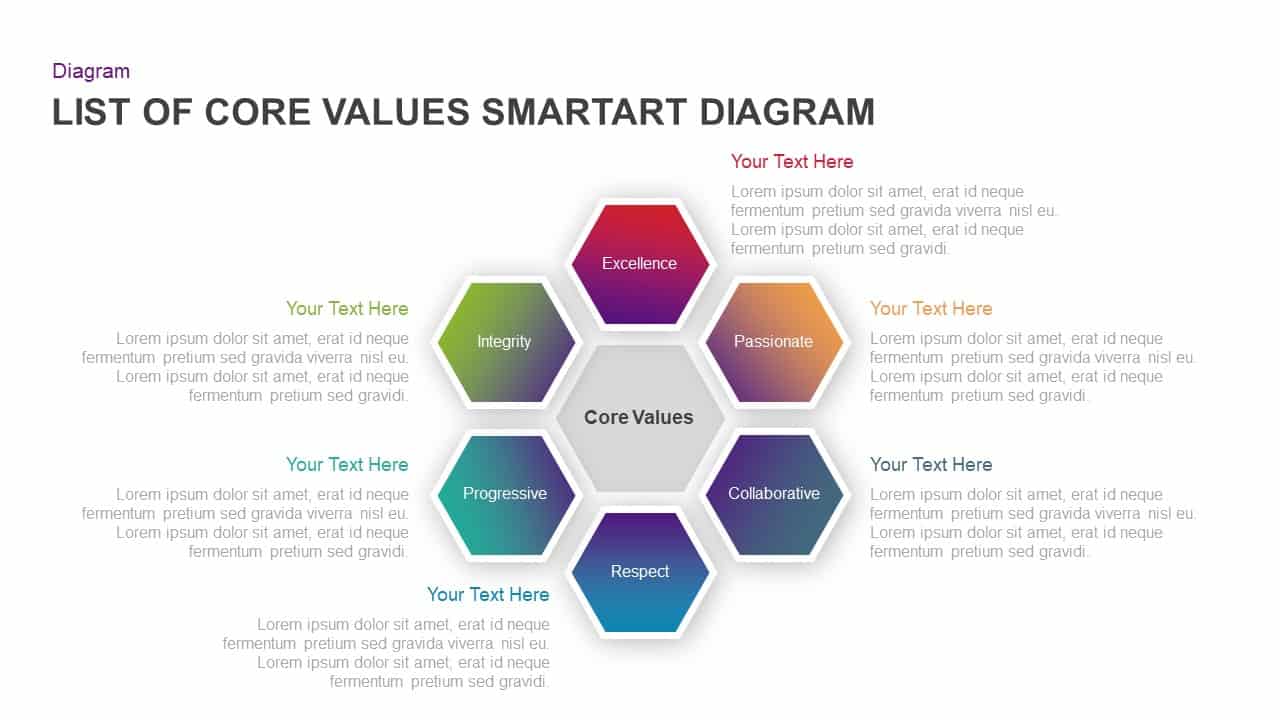
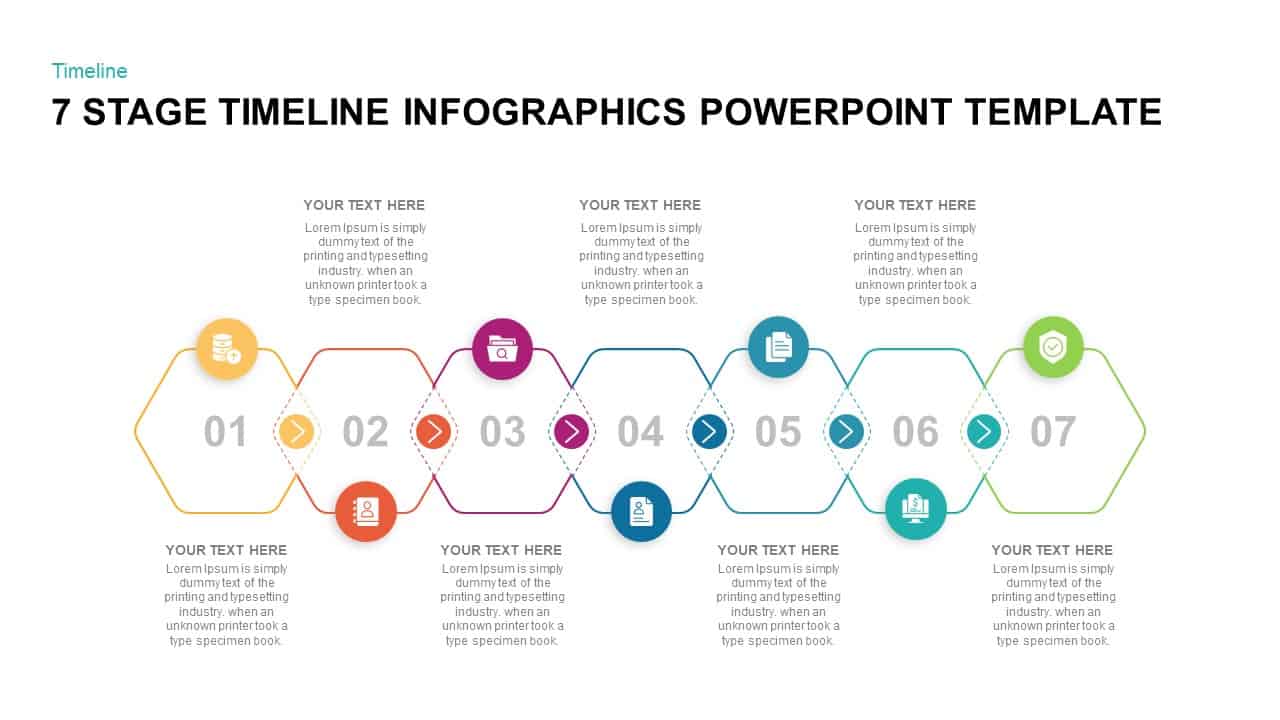
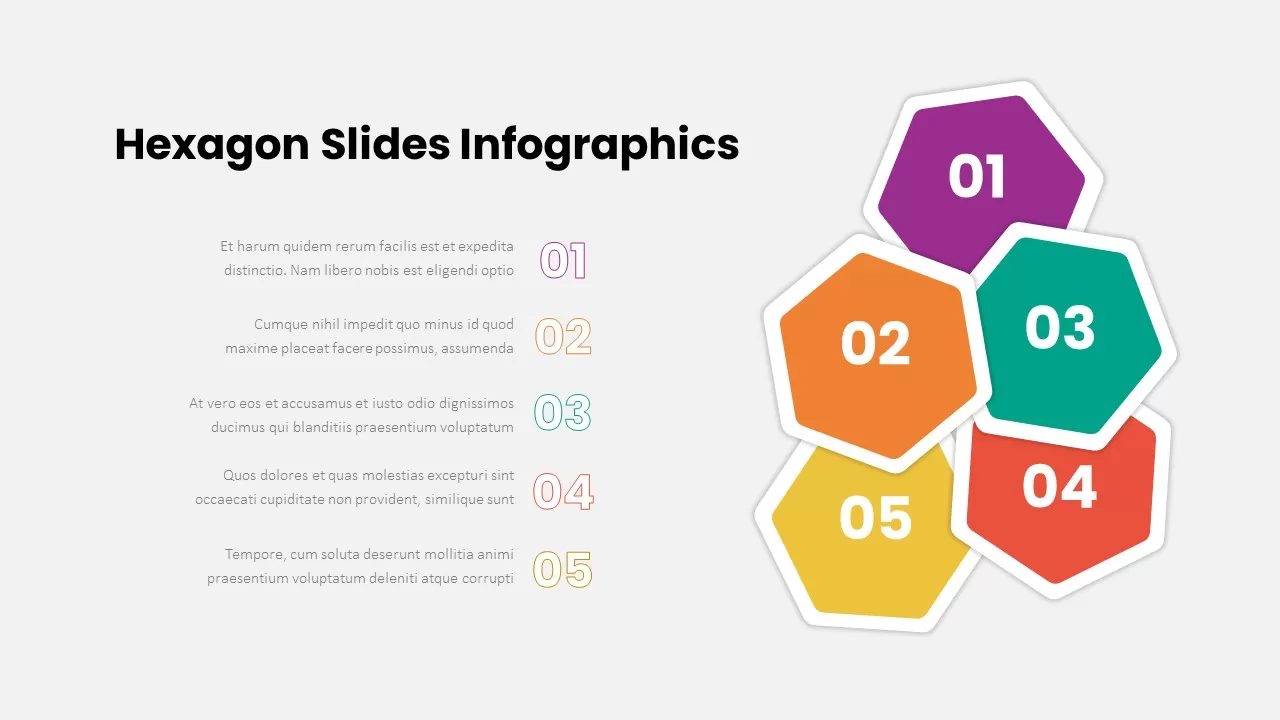
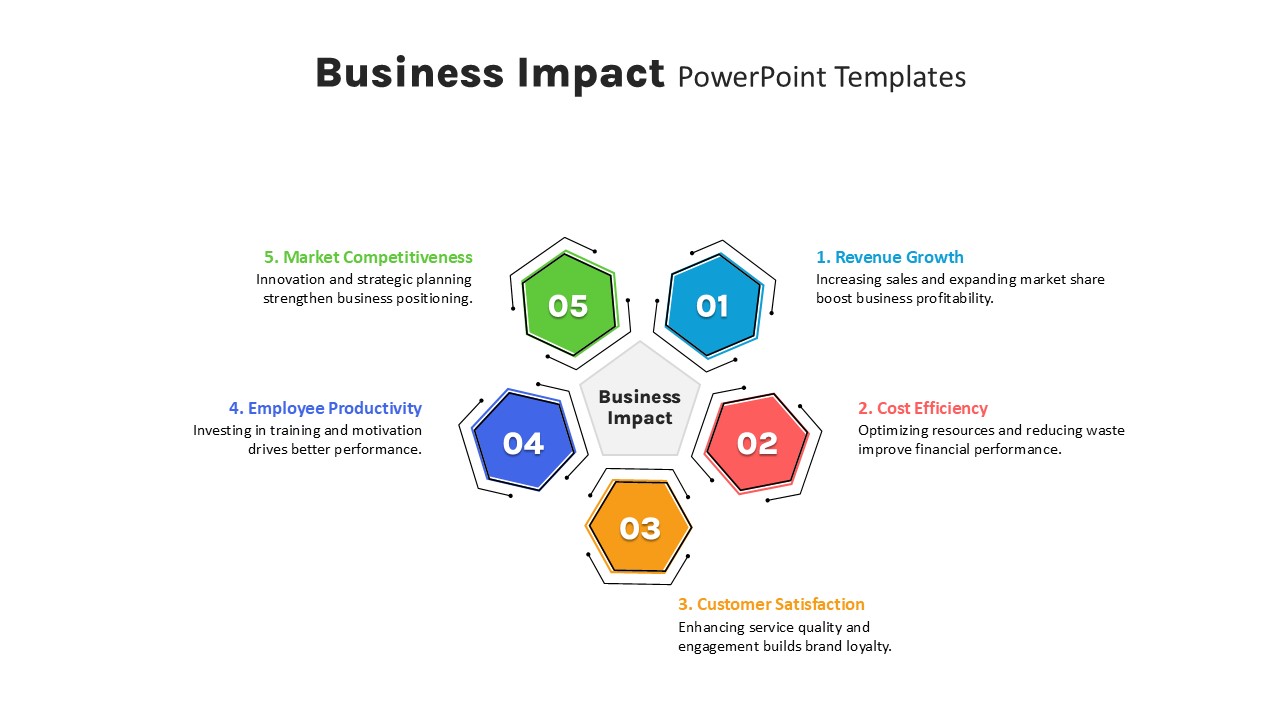
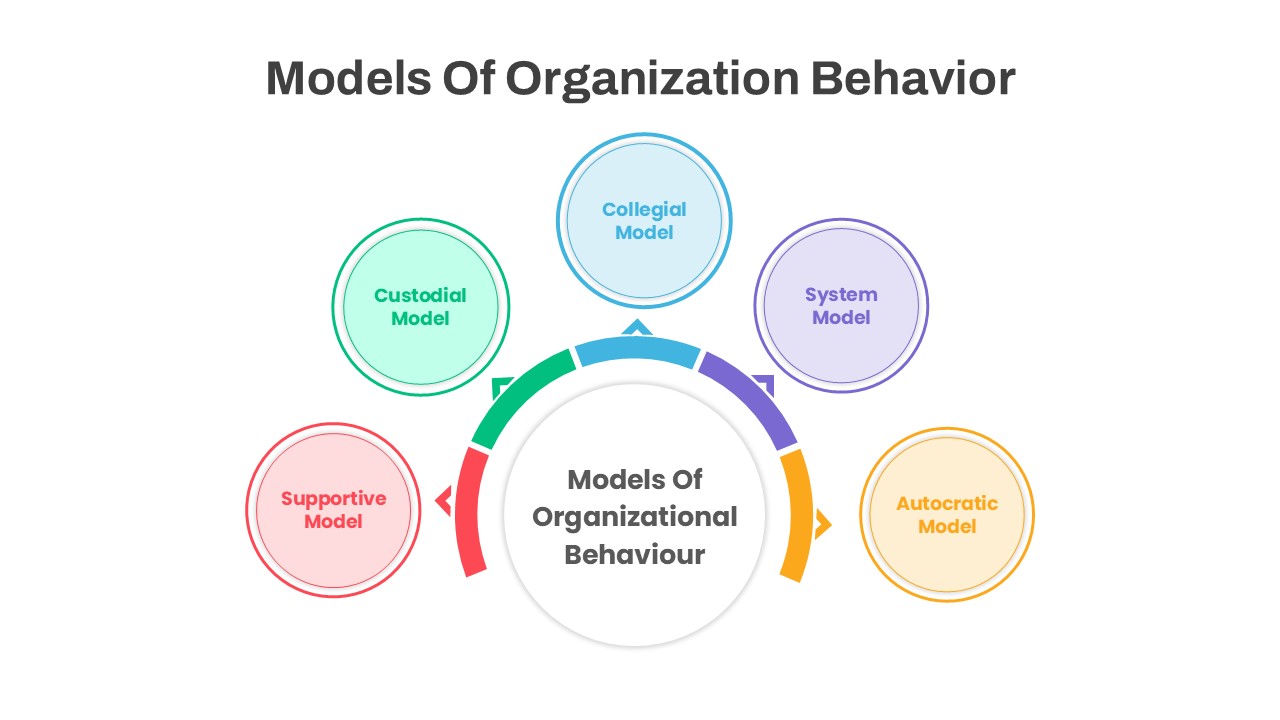
Use the arresting break slide to signal session pauses, featuring enlarged techno-font text and a rendered security emblem. The full-screen infographic slide provides a soft-shaded hexagon canvas ready for process flows, network diagrams, or data visualizations—ensuring seamless integration of custom charts and visuals.
Conclude with a hexagon-based thank-you slide, where three distinct contact panels (phone, email, address) sit above a bold closing header. All slide elements are built on master layouts: easily swap colors, edit fonts, move shapes, or replace icons to reflect your brand’s identity. Vector-based design ensures consistent clarity at any resolution. Whether you’re presenting threat assessments, compliance roadmaps, or risk mitigation plans, this template drives audience engagement and strengthens your narrative with professional polish.
Who is it for
• IT security managers, network administrators, and compliance officers presenting risk analyses or audit findings
• Technology consultants, managed-service providers, and cybersecurity vendors pitching solutions or managed defenses
• C-suite executives and board members reviewing incident-response plans, governance frameworks, or investment proposals
Other Uses
Beyond threat briefings and security workshops, repurpose this deck for data-privacy training, penetration-testing reports, compliance certifications, vendor evaluations, and enterprise architecture overviews.
Login to download this file