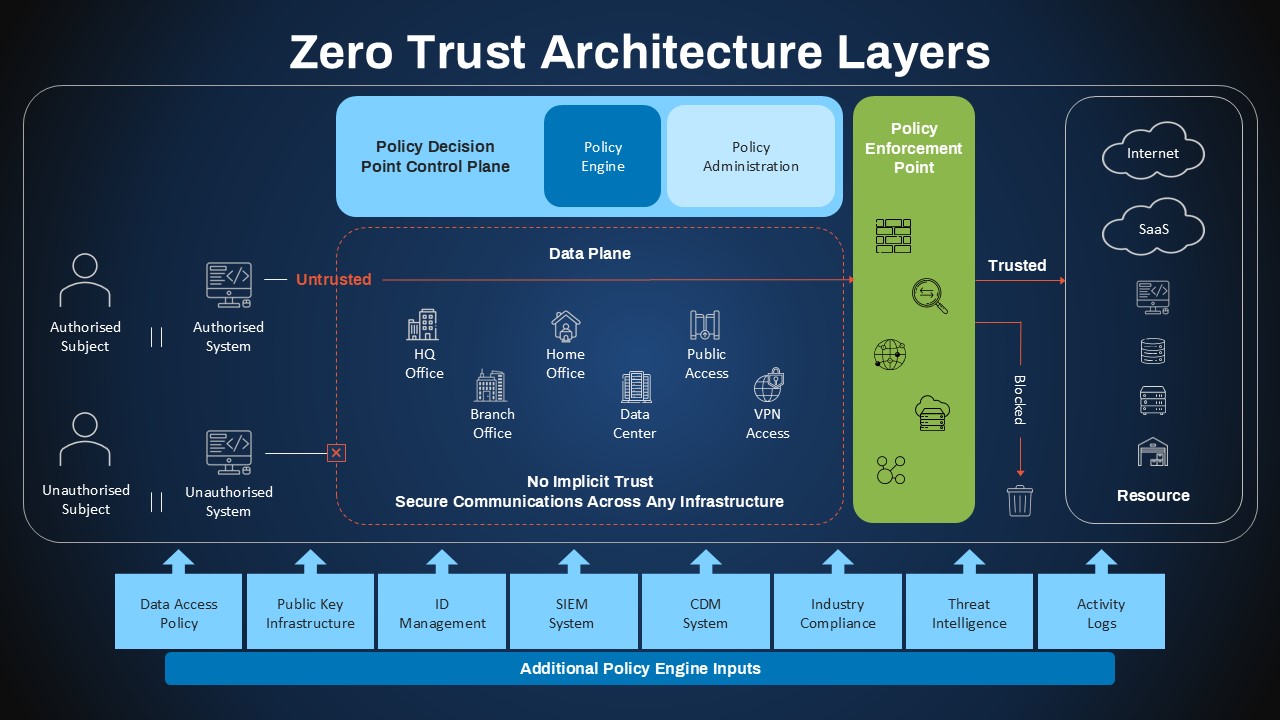
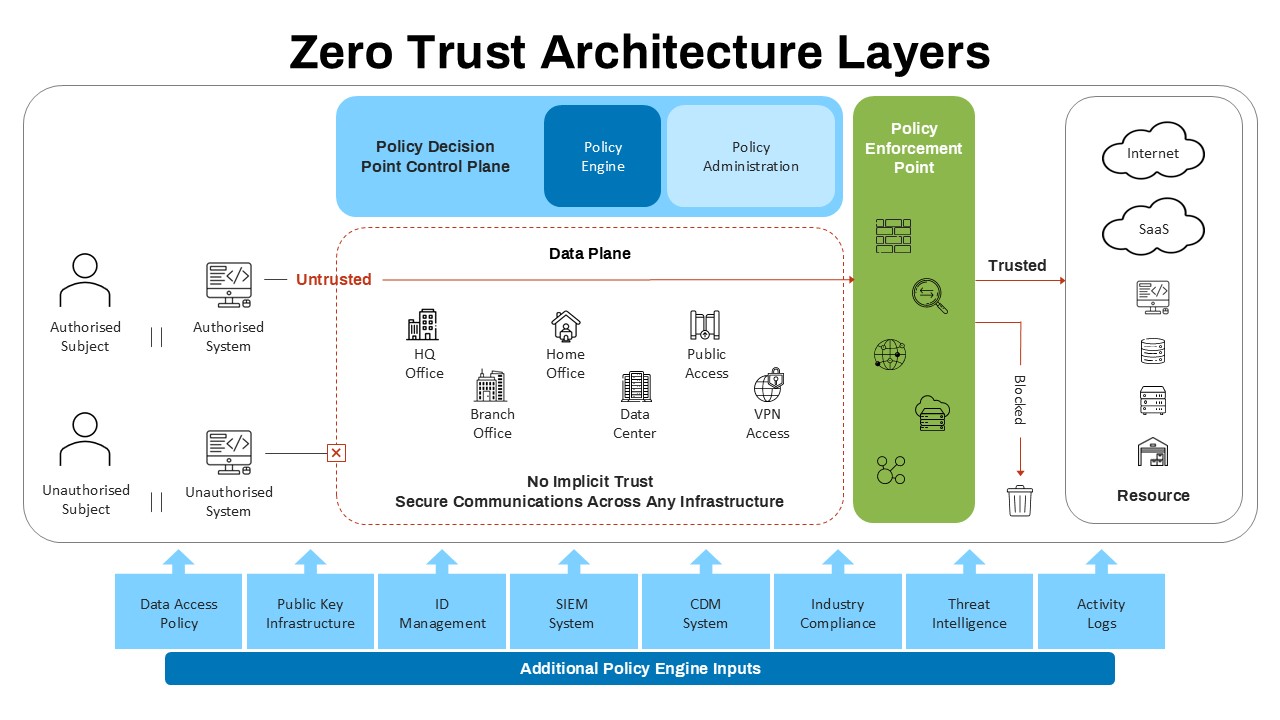
zero-trust-architecture-layers-dark-template-powerpoint-google-slides
Login to download this file
Popular Search Terms
Timeline Infographic
Business Deck
Roadmap Template
Pitch Deck
Sales Deck
Pyramid
Essentials
Must-have decks for quick wins
By Industry
Professionally tailored slides for every sector
By Style
Minimal, modern and creative designs
By Topic
Explore slides curated by purpose and theme
 Timeline
Timeline Roadmap
Roadmap Strategy
Strategy Goals
Goals Table
Table Comparison
Comparison SWOT
SWOT Agenda
Agenda Arrow
Arrow World Map
World Map Maps
Maps Process
Process Funnel
Funnel Team
Team Org Chart
Org Chart Pyramid
Pyramid Circular
Circular
 Business Plan
Business Plan Business Strategy
Business Strategy Business Proposal
Business Proposal Business Models
Business Models Digital Marketing
Digital Marketing Marketing Funnel
Marketing Funnel Customer Experience
Customer Experience Project Status
Project Status Gantt Chart
Gantt Chart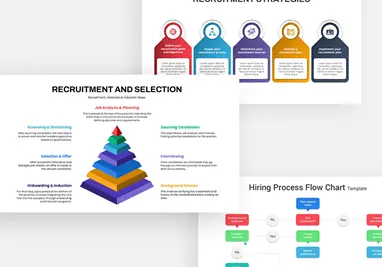 Recruitment
Recruitment Employee Performance
Employee Performance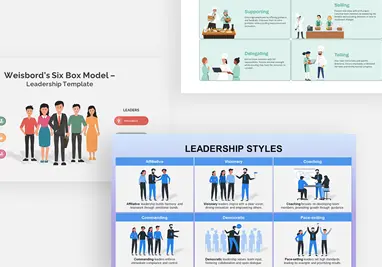 Leadership
Leadership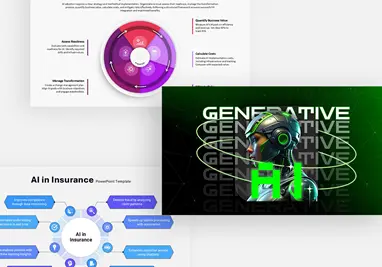 AI
AI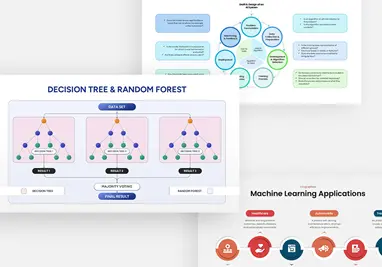 Machine Learning
Machine Learning
AI Presentation Maker
Install the Windows plugin for quick access to templates and design tools.
AI Infographics Maker
Use our Office 365 add - in to access templates directly from the cloud.
Exe Version
Install the Windows plugin for quick access to templates and design tools.
Office 365
Use our Office 365 add - in to access templates directly from the cloud.
Mac Version
Get the Mac plugin to easily browse, insert, and customize templates and visuals within PowerPoint.
Home » Zero Trust Architecture Layers template for PowerPoint & Google Slides » zero-trust-architecture-layers-dark-template-powerpoint-google-slides


Create professional presentations with this presentation slide template designed for business professionals. Perfect for business professionals. Works with PowerPoint and Google Slides.
Login to download this file
No. of Slides
2Item ID
SB05107Rating
0.0
(0 reviews)