Threat Detection & Response PowerPoint Template Dark and Google Slides
Description
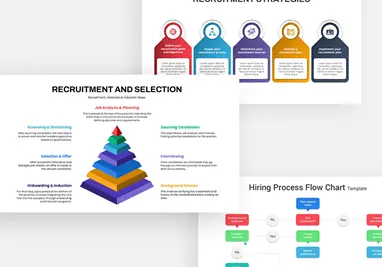
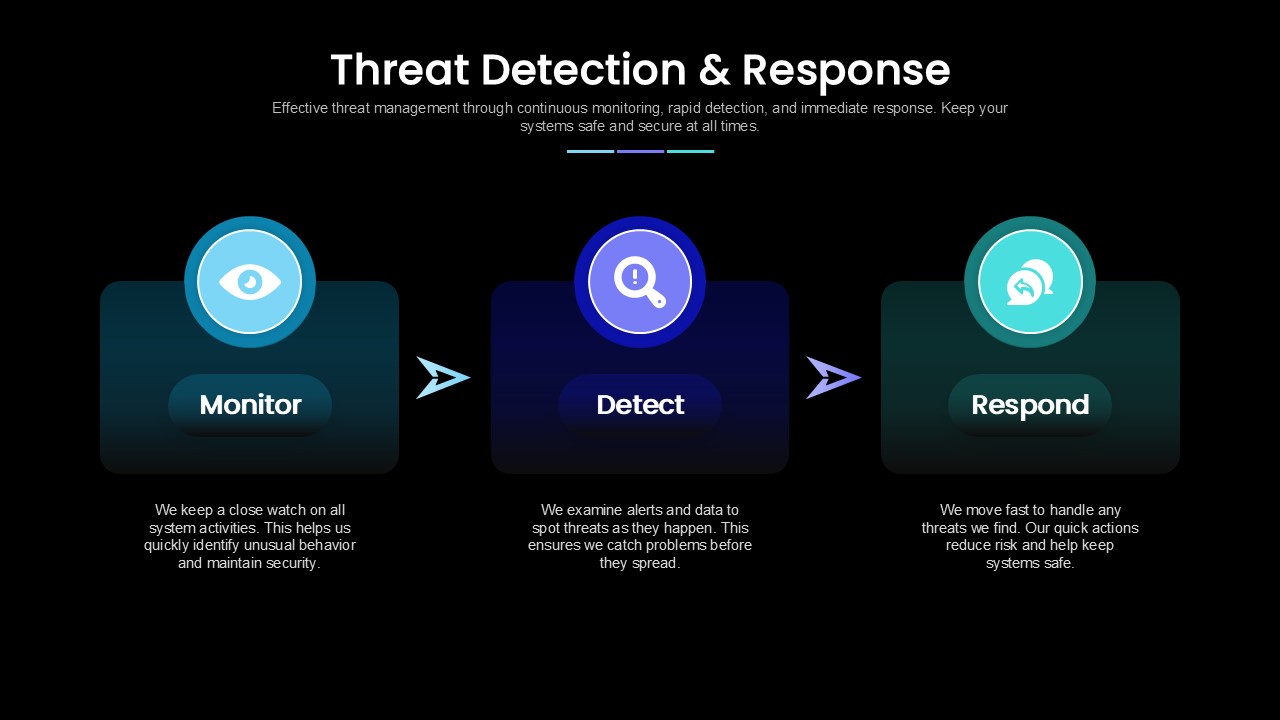
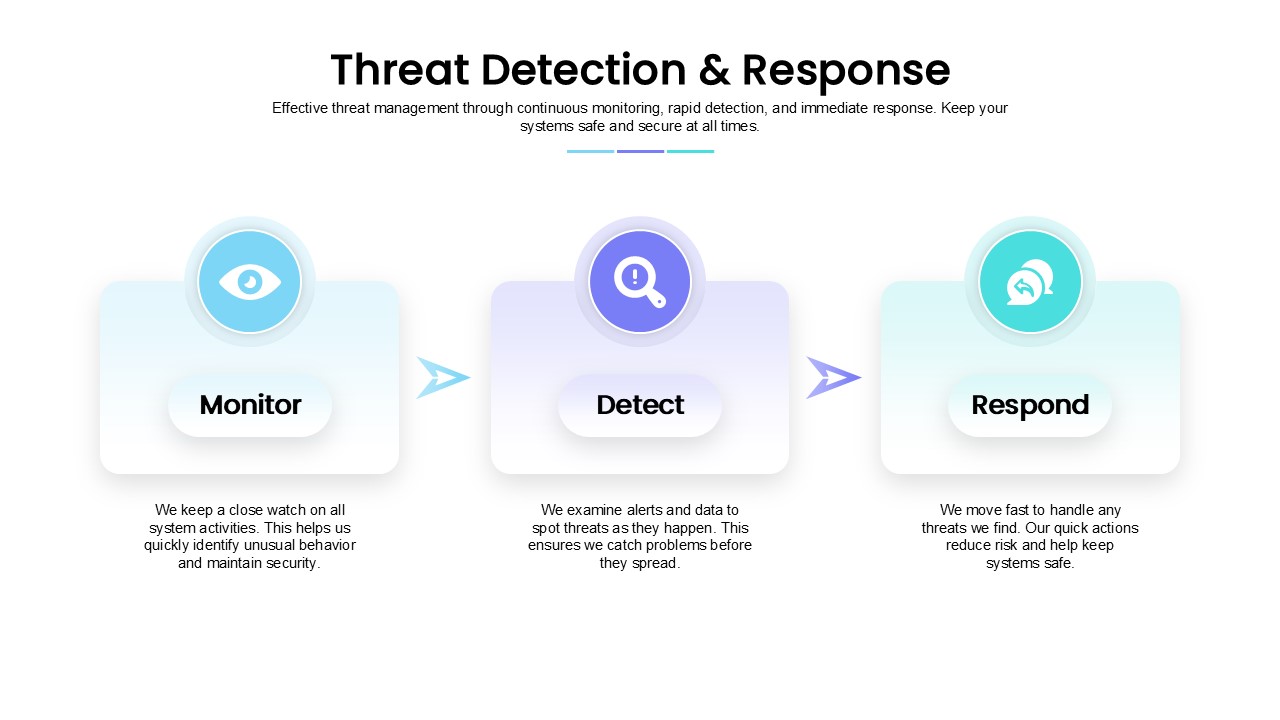
A clean, three-step workflow diagram illustrating the core phases of security incident management:
- Monitor – Continuous surveillance of system activities (light-blue card with eye icon).
- Detect – Real-time analysis of alerts and logs to identify threats early (lavender card with magnifying-glass/exclamation icon).
- Respond – Rapid, targeted remediation actions to contain and resolve incidents (teal card with circular-arrow icon).
Each phase is presented in its own rounded-corner card with gradient fill, icon, bold label, and brief explanatory text, connected by directional arrows. A concise header and sub-header frame the diagram.
Who Is It For
- Security Operations Center (SOC) Teams mapping out their incident-handling workflow.
- IT & Cybersecurity Managers presenting threat management processes to stakeholders.
- Risk & Compliance Officers outlining security controls and response plans.
- Security Consultants training clients on best practices for monitoring, detection, and incident response.
Other Uses
- Fraud Detection Workflows (e.g., Monitor transactions → Detect anomalies → Respond with holds).
- Network Performance Monitoring (Observe network health → Alert on issues → Remediate bottlenecks).
- Data Loss Prevention (Watch data flows → Spot unauthorized transfers → Block or quarantine).
- Operational Incident Management in DevOps or ITIL frameworks.
Login to download this file