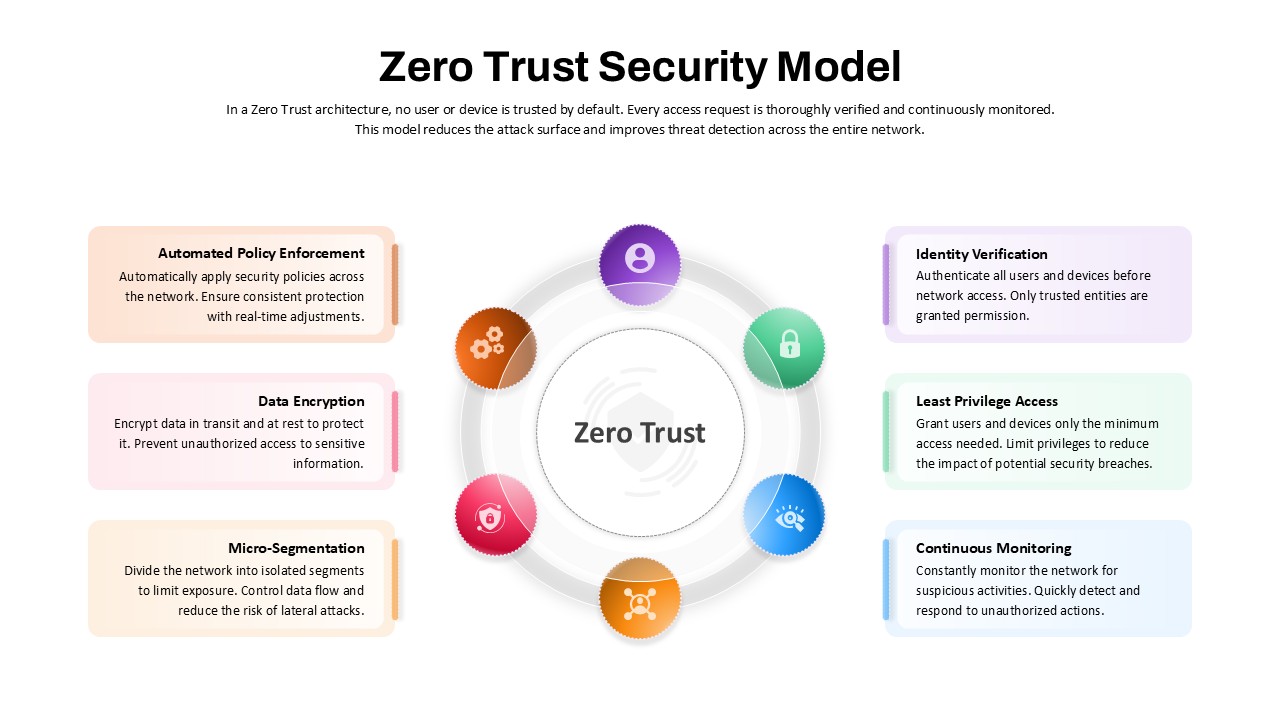
IT Cyber Security Template for PowerPoint & Google Slides
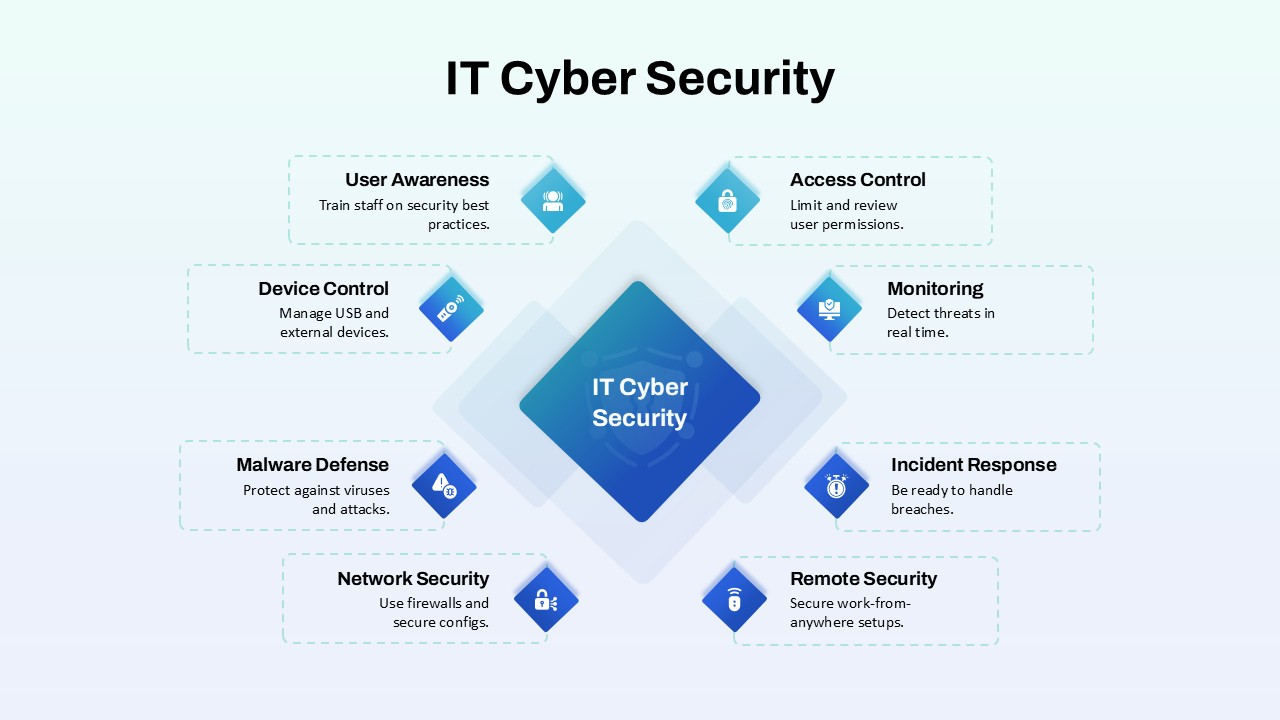
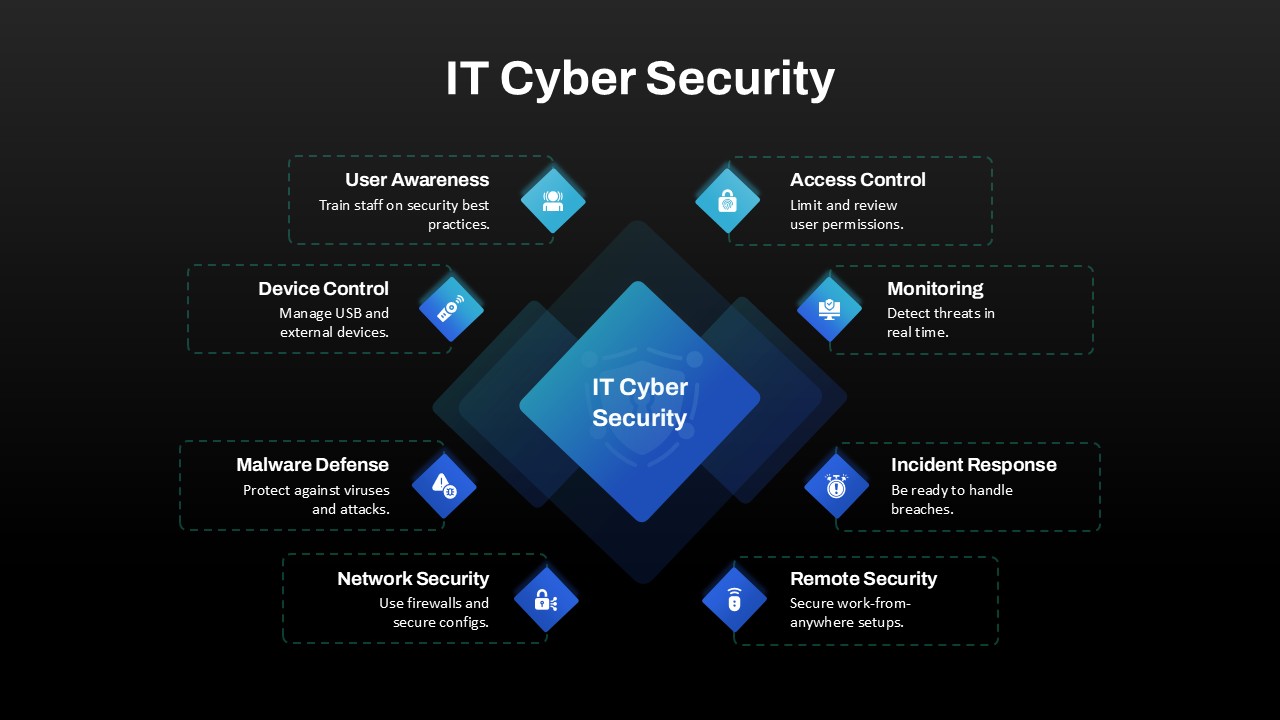
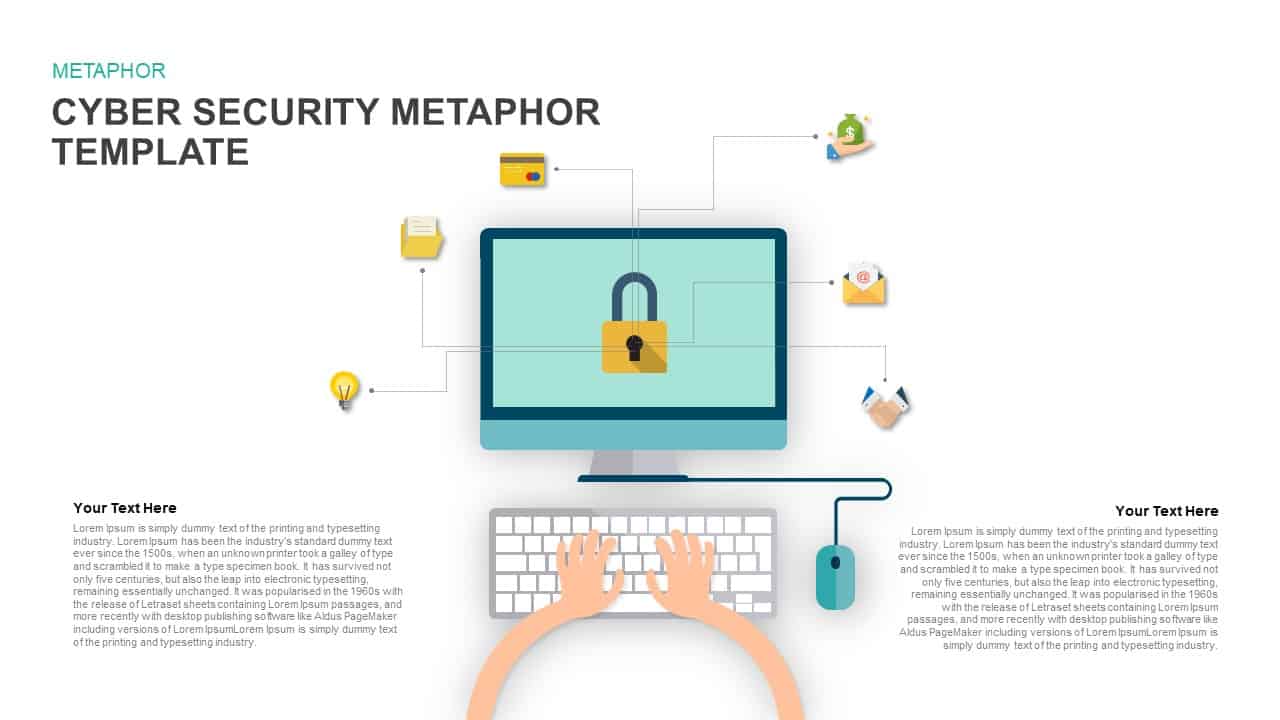
Leverage this IT cyber security hub-and-spoke diagram slide to present a comprehensive breakdown of essential security domains in a clear, visually engaging layout. At its center, a gradient blue diamond labeled “IT Cyber Security” anchors eight outward-pointing spokes, each terminating in a matching icon diamond and labelled callout for User Awareness, Access Control, Monitoring, Incident Response, Remote Security, Network Security, Malware Defense, and Device Control. The dashed outline containers and consistent iconography guide viewers across each security pillar, while generous white margins and modern sans-serif typography ensure clarity—whether projected in boardrooms, shared in virtual meetings, or embedded in stakeholder reports.
This fully editable template is built on master slides and populated with scalable vector graphics, making customization effortless. Swap icon glyphs to represent proprietary tools or in-house processes, adjust gradient hues to align with corporate branding, or modify callout text to reflect internal policy names. Intuitive placeholders allow you to update headings, descriptions, and connector styles in seconds. Layered objects facilitate high-resolution exports and support sequential animations, enabling presenters to reveal each security element one at a time and maintain audience focus during live demonstrations or recorded training sessions.
Optimized for both PowerPoint and Google Slides, this slide preserves formatting integrity across platforms and prevents version-control issues when collaborating with distributed teams. Use it during cybersecurity workshops, compliance briefings, or IT strategy sessions to align stakeholders on layered defense frameworks. Duplicate or reorder the hub-and-spoke segments to compare alternative architectures—such as zero-trust models or compliance controls—or integrate additional spokes for emerging topics like cloud security or IoT protection. By distilling complex IT safeguards into an intuitive visual framework, this template empowers presenters to communicate critical security measures with confidence, cohesion, and professional polish.
Who is it for
IT managers, cybersecurity professionals, network administrators, and compliance officers will benefit from this diagram when illustrating defense-in-depth strategies, training staff on best practices, or briefing executives on risk mitigation plans.
Other Uses
Repurpose this hub-and-spoke layout to map business continuity processes, project governance frameworks, technology service portfolios, or any multi-faceted IT initiative by simply updating icons, labels, and callout details.
Login to download this file