Endpoint Security PowerPoint Template and google slides dark theme
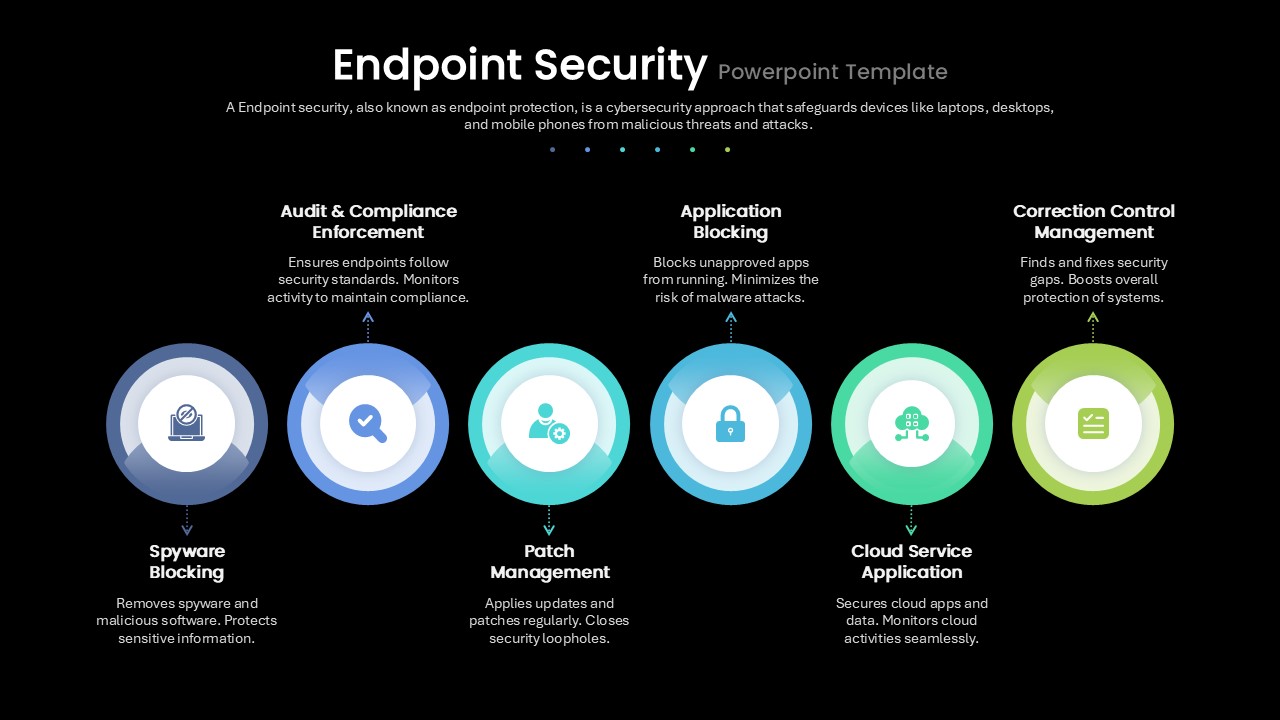
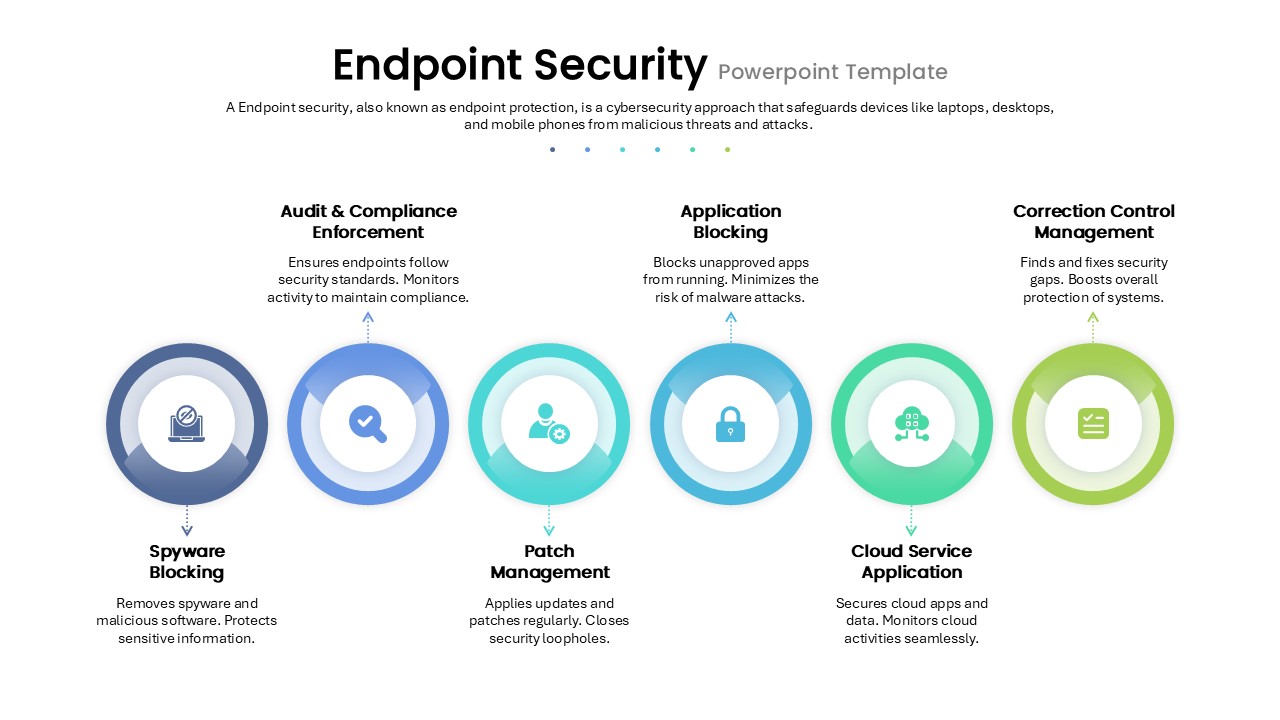
Leverage this endpoint security infographic slide to showcase the essential protection measures that safeguard devices—such as laptops, desktops, and mobile phones—against malware, compliance risks, and unauthorized access. The slide features a clean white canvas overlaid with a subtle circuit-pattern watermark for context. Across the center, six gradient ring–shaped progress icons—each in a distinct hue ranging from deep blue through teal to vibrant green—are evenly spaced. Icons depicting a spyware shield, compliance check, system update, locked app, cloud node, and security checklist convey each defense layer. Directional arrows link each ring to callouts above or below, where concise headings and descriptive text explain functions like spyware removal, audit and compliance enforcement, patch management, application blocking, cloud service protection, and corrective controls. The balanced layout—with ample white space, consistent line weights, and modern sans-serif typography—ensures that technical audiences can quickly grasp the multi-layered security workflow without visual clutter.
Built on master slides with vector-based artwork, this fully editable template offers intuitive placeholders for icons, headings, and detailed notes. Users can easily swap out icons to represent custom security tools or adjust ring colors to align with corporate branding. Text placeholders accommodate notes on policy enforcement, patch cadence, risk thresholds, and service-level objectives. By leveraging scalable, high-resolution graphics, presenters can seamlessly adapt the design for both on-screen presentations and printed reports. Whether you are documenting cyber-risk mitigation in a boardroom briefing or training IT teams on best practices, this template accelerates content creation, ensures design consistency, and reinforces the importance of a comprehensive endpoint security strategy. With this slide in your toolkit, you can visually narrate a layered defense approach that integrates detection, prevention, and continuous improvement measures—all within a cohesive visual framework.
Who is it for
IT security teams, cybersecurity professionals, IT managers, and network administrators will benefit from this slide when presenting endpoint protection strategies to stakeholders or training technical teams.
Other Uses
Beyond endpoint security, repurpose this layout for illustrating multi-layered defense strategies in compliance programs, network security audits, or vulnerability management workflows.
Login to download this file