zero-trust-security-model-dark-template-powerpoint-google-slides
Description
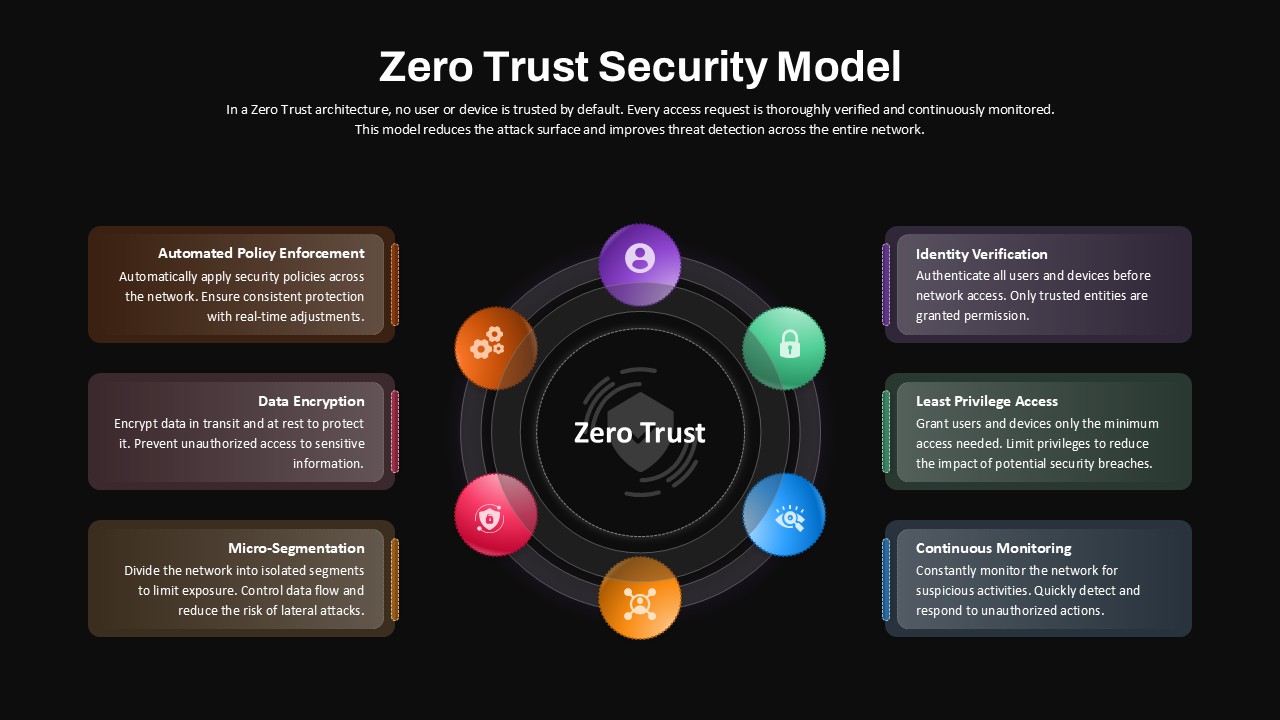
The Zero Trust Security Model slide provides a dynamic and structured approach to explaining the key components of the Zero Trust framework. This visual representation illustrates six critical elements of the model—Automated Policy Enforcement, Data Encryption, Micro-Segmentation, Identity Verification, Least Privilege Access, and Continuous Monitoring—all surrounding a central "Zero Trust" hub. Each component is color-coded and accompanied by descriptive text, offering a comprehensive overview of how to protect and verify users, devices, and data in a network.
The layout’s circular design allows for easy flow and understanding, guiding the audience through each security measure in a logical and intuitive way. The dark background enhances the vivid color scheme, making each section stand out while keeping the focus on the core message. This slide is ideal for cybersecurity professionals, IT teams, and stakeholders looking to present the Zero Trust model in an easy-to-understand yet detailed format.
Who is it for
This slide is perfect for IT security professionals, network administrators, and systems engineers who need to explain and implement the Zero Trust Security Model. It’s also valuable for business leaders, consultants, and educators involved in digital transformation, cybersecurity, or risk management initiatives. It can be used in internal training sessions or client-facing presentations.
Other Uses
This slide can also be adapted for presentations on network security best practices, digital risk management, and compliance audits. It can serve as a foundational tool for educating teams on how Zero Trust principles apply across an organization, or in discussions about mitigating cyber threats in an increasingly connected world.
Login to download this file